filmov
tv
Why The Log4j Exploit Was So Dangerous

Показать описание
Why is Log4jShell, or CVE-2021-44228 so dangerous? There are a number of reasons, and we go through them in this video. First, the barrier for attackers to use this exploit is incredibly low and the payoff is incredibly high.This exploit leads to unauthenticated remote code execution (RCE) on systems running log4j, which includes systems running Minecraft and hosting Steam, iCloud, and other apps. Patching can also be a problem for engineering teams, and we go through that here as well.
Ref:
⭐️ Find me at:
Interested in starting a lab or sprucing up your home office? Check out these affiliate links for cool things I highly recommend! These also go to help support the channel!
👇👇👇👇👇👇👇👇👇👇👇
Note: I receive a small commission from any purchases of any of the gear shown in the affiliate link above. This supports the channel and keeps the content free! 😎 Enjoy the quality of this video? Consider getting what I use to make this content!
Ref:
⭐️ Find me at:
Interested in starting a lab or sprucing up your home office? Check out these affiliate links for cool things I highly recommend! These also go to help support the channel!
👇👇👇👇👇👇👇👇👇👇👇
Note: I receive a small commission from any purchases of any of the gear shown in the affiliate link above. This supports the channel and keeps the content free! 😎 Enjoy the quality of this video? Consider getting what I use to make this content!
Log4J & JNDI Exploit: Why So Bad? - Computerphile
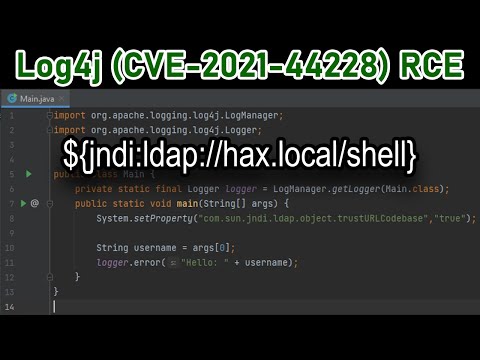
Log4j (CVE-2021-44228) RCE Vulnerability Explained
Apache Log4j: The Exploit that Almost Killed the Internet
Minecraft Beaten in 0:00.050 Using Log4j Exploit
SheHacksPurple: Log4J explained for Software Developers and AppSec Folks
How Hackers Exploit Log4J to Get a Reverse Shell (Ghidra Log4Shell Demo) | HakByte
Rules to detect Log4j Exploits
Log4j Vulnerability Could Give Hackers Control Over Millions of Devices
Why The Log4j Exploit Was So Dangerous
log4j (Log4Shell) Security Issue Explained at a High Level
The Log4j Vulnerability Exploit Explained
Log4j Vulnerability (Log4Shell) Explained // CVE-2021-44228
Understanding the Log4j Vulnerability | Exploiting VMware VCenter & a reverse shell🔥| Patch NOW!...
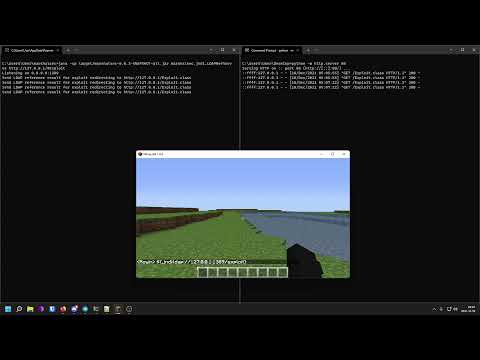
Log4j Remote Code Execution Exploit in Minecraft
Log4J Vulnerability (Log4Shell) Explained - for Java developers
Log4j 2 RCE Exploit PoC (CVE-2021-44832)
The Scariest Week in Minecraft History
Apache log4j Vulnerability Explained
What We've Learned About The Log4J Exploits So Far
What is Log4j & why is everyone talking about it? (in 60 seconds)
Log4j Vulnerability | How to protect your Systems and Servers from Log4j | Fix this ASAP!!!
Log4j exploit is so much bigger than you realize. Every company is getting owned
Log4j Exploit / Vulnerability Explained. Minecraft Infected!
Exploits Explained: How Log4j, Buffer Overflows and Other Exploits Work
Комментарии
 0:26:31
0:26:31
 0:03:44
0:03:44
 0:15:41
0:15:41
 0:00:23
0:00:23
 0:06:37
0:06:37
 0:08:42
0:08:42
 0:02:53
0:02:53
 0:09:34
0:09:34
 0:11:31
0:11:31
 0:03:00
0:03:00
 0:22:41
0:22:41
 0:17:44
0:17:44
 0:20:30
0:20:30
 0:00:12
0:00:12
 0:20:50
0:20:50
 0:00:42
0:00:42
 0:09:48
0:09:48
 0:15:08
0:15:08
 0:07:43
0:07:43
 0:01:01
0:01:01
 0:03:34
0:03:34
 0:00:16
0:00:16
 0:07:13
0:07:13
 0:09:08
0:09:08