filmov
tv
Log4J - CVE 2021-44228 (Log4Shell) - Exploitation & Mitigation

Показать описание
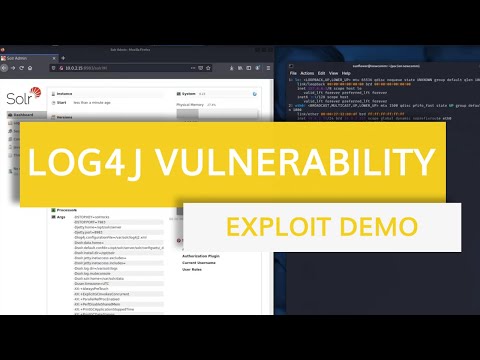
In this video, I demonstrate the process of exploiting the Log4J vulnerability, also known as Log4Shell as well as explore the process of mitigating the vulnerability on Apache Solr.
//WHAT IS LOG4J?
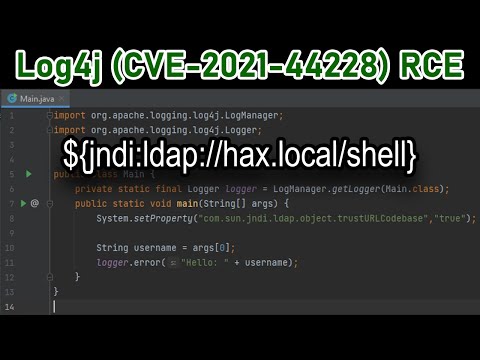
Apache Log4j is one of the most widely utilized, open-source Java-based logging utilities. It is used by various Apache solutions like Apache Tomcat, Apache Solr, and Apache Druid to name a few.
//WHAT IS LOG4SHELL?
On November 30th, 2021, the Apache log4j development team was made aware of a vulnerability in Log4j that could allow the injection of malicious input that could consequently facilitate remote code execution.
On December 9th, 2021, the Infosec community was made aware of this finding and the far-reaching impacts of the vulnerability.
The vulnerability could potentially allow attackers to take control of any system running Log4j by logging a certain string.
The vulnerability, now assigned as CVE-2021–44228 has a severity score of 10 (CRITICAL) and has been dubbed “Log4Shell”.
//LINKS
//PLATFORMS
//SOCIAL NETWORKS
//BOOKS
//SUPPORT THE CHANNEL
//CYBERTALK PODCAST
//WE VALUE YOUR FEEDBACK
We hope you enjoyed the video and found value in the content. We value your feedback, If you have any questions or suggestions feel free to post them in the comments section or contact us directly via our social platforms.
//THANK YOU!
Thanks for watching!
Благодарю за просмотр!
Kiitos katsomisesta
Danke fürs Zuschauen!
感谢您观看
Merci d'avoir regardé
Obrigado por assistir
دیکھنے کے لیے شکریہ
देखने के लिए धन्यवाद
Grazie per la visione
Gracias por ver
شكرا للمشاهدة
-----------------------------------------------------------------------------------
#Log4J#Log4Shell#CVE-2021-44228
//WHAT IS LOG4J?
Apache Log4j is one of the most widely utilized, open-source Java-based logging utilities. It is used by various Apache solutions like Apache Tomcat, Apache Solr, and Apache Druid to name a few.
//WHAT IS LOG4SHELL?
On November 30th, 2021, the Apache log4j development team was made aware of a vulnerability in Log4j that could allow the injection of malicious input that could consequently facilitate remote code execution.
On December 9th, 2021, the Infosec community was made aware of this finding and the far-reaching impacts of the vulnerability.
The vulnerability could potentially allow attackers to take control of any system running Log4j by logging a certain string.
The vulnerability, now assigned as CVE-2021–44228 has a severity score of 10 (CRITICAL) and has been dubbed “Log4Shell”.
//LINKS
//PLATFORMS
//SOCIAL NETWORKS
//BOOKS
//SUPPORT THE CHANNEL
//CYBERTALK PODCAST
//WE VALUE YOUR FEEDBACK
We hope you enjoyed the video and found value in the content. We value your feedback, If you have any questions or suggestions feel free to post them in the comments section or contact us directly via our social platforms.
//THANK YOU!
Thanks for watching!
Благодарю за просмотр!
Kiitos katsomisesta
Danke fürs Zuschauen!
感谢您观看
Merci d'avoir regardé
Obrigado por assistir
دیکھنے کے لیے شکریہ
देखने के लिए धन्यवाद
Grazie per la visione
Gracias por ver
شكرا للمشاهدة
-----------------------------------------------------------------------------------
#Log4J#Log4Shell#CVE-2021-44228
Комментарии
 0:45:40
0:45:40
 0:03:44
0:03:44
 0:17:44
0:17:44
 0:06:51
0:06:51
 0:01:46
0:01:46
 0:34:50
0:34:50
 0:05:25
0:05:25
 0:06:44
0:06:44
 0:16:07
0:16:07
 0:03:45
0:03:45
 0:08:09
0:08:09
 0:18:34
0:18:34
 0:05:57
0:05:57
 0:03:00
0:03:00
 0:05:52
0:05:52
 0:10:55
0:10:55
 0:07:37
0:07:37
 0:00:50
0:00:50
 0:01:27
0:01:27
 0:01:59
0:01:59
 0:02:39
0:02:39
 0:34:52
0:34:52
 0:16:31
0:16:31
 0:00:41
0:00:41