filmov
tv
How does the Tor network hide your traffic?

Показать описание
The Onion Router (Tor) creates a network for encrypting data traffic. Using a Tor browser, you can hide your identity, your location, the websites you visit, and some other browsing activities. Today I will demonstrate how the Tor network works.
Playlists:
Privacy Enhanced Technologies
Business continuity
Cyber Attacks and Defense
Basic Cryptography
Advanced Cryptography:
Public Key Infrastructure
Remote Access & WAN Technologies
Playlists:
Privacy Enhanced Technologies
Business continuity
Cyber Attacks and Defense
Basic Cryptography
Advanced Cryptography:
Public Key Infrastructure
Remote Access & WAN Technologies
How TOR Works
How does the Tor network hide your traffic?
How TOR Works- Computerphile
Tor As Fast As Possible
What is Tor and Should You Use It? | Mashable Explains
How to use Tor Browser | Tor Tutorial part 1
What Is Tor Browser And How It Works? | Why Should You Use It? | Tor Browser Explained | Simplilearn
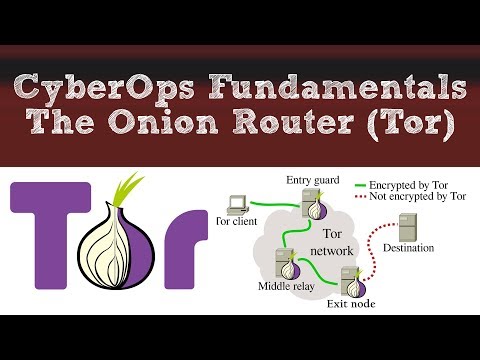
Cyber Ops Fundamentals: The Onion Router (Tor)
Tor Browser Explained: Browsing the Internet Anonymously
Tor vs VPN | What's the Difference? (and which should you use?)
Dark Web: How The Unseen Internet Is Accessed
The Secrets of The Tor Browser
Tor Browser - How to Use, Tutorial for Beginners in 6 MINS! [ COMPLETE ]
What is Tor Network and How does it work? | Explained |
TOR Hidden Services - Computerphile
The Ultimate Guide to Using Tor Browser Securely
What is the TOR network and how does it work?
How Tor Works? (The Onion Router)
How to Use Tor Browser Safely in 2024: A Beginner's Guide
Is TOR Still Anonymous? and How Were People Caught Using TOR?
Hundreds of Tor Relays are Being Used to De-anonymize Users
Stop Using Tor With VPNs
The Onion Router (Tor) Network
How To Find Anything On The Dark Web
Комментарии
 0:10:57
0:10:57
 0:05:02
0:05:02
 0:14:19
0:14:19
 0:06:14
0:06:14
 0:02:25
0:02:25
 0:11:46
0:11:46
 0:14:49
0:14:49
 0:03:54
0:03:54
 0:04:13
0:04:13
 0:08:18
0:08:18
 0:03:40
0:03:40
 0:19:10
0:19:10
 0:06:24
0:06:24
 0:03:23
0:03:23
 0:11:42
0:11:42
 0:10:17
0:10:17
 0:04:05
0:04:05
 0:23:48
0:23:48
 0:05:41
0:05:41
 0:12:06
0:12:06
 0:08:57
0:08:57
 0:11:41
0:11:41
 0:06:50
0:06:50
 0:02:07
0:02:07