filmov
tv
How TOR Works

Показать описание
In this video I give you some brief insight into how TOR actually works.
and be sure to click that notification bell so you know when new videos are released. ₿💰💵💲Help Support the Channel by Donating Crypto💲💵💰₿
Bitcoin
3MMKHXPQrGHEsmdHaAGD59FWhKFGeUsAxV
Ethereum
0xeA4DA3F9BAb091Eb86921CA6E41712438f4E5079
Litecoin
MBfrxLJMuw26hbVi2MjCVDFkkExz8rYvUF
Dash
Xh9PXPEy5RoLJgFDGYCDjrbXdjshMaYerz
Zcash
t1aWtU5SBpxuUWBSwDKy4gTkT2T1ZwtFvrr
Chainlink
0x0f7f21D267d2C9dbae17fd8c20012eFEA3678F14
Bitcoin Cash
qz2st00dtu9e79zrq5wshsgaxsjw299n7c69th8ryp
Etherum Classic
0xeA641e59913960f578ad39A6B4d02051A5556BfC
USD Coin
0x0B045f743A693b225630862a3464B52fefE79FdB
and be sure to click that notification bell so you know when new videos are released. ₿💰💵💲Help Support the Channel by Donating Crypto💲💵💰₿
Bitcoin
3MMKHXPQrGHEsmdHaAGD59FWhKFGeUsAxV
Ethereum
0xeA4DA3F9BAb091Eb86921CA6E41712438f4E5079
Litecoin
MBfrxLJMuw26hbVi2MjCVDFkkExz8rYvUF
Dash
Xh9PXPEy5RoLJgFDGYCDjrbXdjshMaYerz
Zcash
t1aWtU5SBpxuUWBSwDKy4gTkT2T1ZwtFvrr
Chainlink
0x0f7f21D267d2C9dbae17fd8c20012eFEA3678F14
Bitcoin Cash
qz2st00dtu9e79zrq5wshsgaxsjw299n7c69th8ryp
Etherum Classic
0xeA641e59913960f578ad39A6B4d02051A5556BfC
USD Coin
0x0B045f743A693b225630862a3464B52fefE79FdB
How TOR Works- Computerphile
How TOR Works
How Tor Works? (The Onion Router)
Tor As Fast As Possible
What is Tor and Should You Use It? | Mashable Explains
What Is Tor Browser And How It Works? | Why Should You Use It? | Tor Browser Explained | Simplilearn
How Tor Works - A ComputeCycle Deep Dive
TOR Hidden Services - Computerphile
silk_road.onion | How They Got Caught #1 & How Tor Works
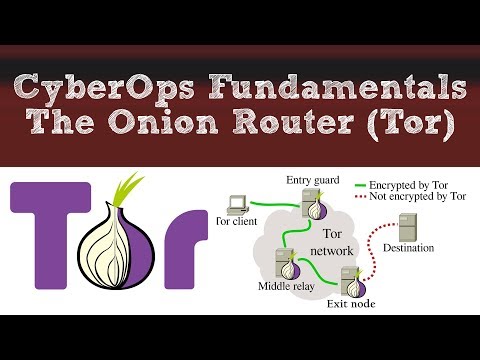
Cyber Ops Fundamentals: The Onion Router (Tor)
How does the Tor network hide your traffic?
The Ultimate Guide to Using Tor Browser Securely
Hundreds of Tor Relays are Being Used to De-anonymize Users
How to use Tor Browser | Tor Tutorial part 1
How to Use Tor Browser Safely in 2024: A Beginner's Guide
How TOR works | In Tamil | Cyber Voyage
Tor Browser Explained: Browsing the Internet Anonymously
Tor vs VPN | What's the Difference? (and which should you use?)
How To Access the DARK WEB in 2024 (3 Levels)
Tor Browser - How to Use, Tutorial for Beginners in 6 MINS! [ COMPLETE ]
Stop Using Tor With VPNs
The Secrets of The Tor Browser
How Tor works? || What is Tor Browser?
The Dark Web NEEDS You!
Комментарии
 0:14:19
0:14:19
 0:10:57
0:10:57
 0:23:48
0:23:48
 0:06:14
0:06:14
 0:02:25
0:02:25
 0:14:49
0:14:49
 0:10:11
0:10:11
 0:11:42
0:11:42
 0:35:51
0:35:51
 0:03:54
0:03:54
 0:05:02
0:05:02
 0:10:17
0:10:17
 0:08:57
0:08:57
 0:11:46
0:11:46
 0:05:41
0:05:41
 0:05:37
0:05:37
 0:04:13
0:04:13
 0:08:18
0:08:18
 0:15:20
0:15:20
 0:06:24
0:06:24
 0:11:41
0:11:41
 0:19:10
0:19:10
 0:04:19
0:04:19
 0:24:00
0:24:00