filmov
tv
The Hidden Networks: Onion Routing, TOR, Lokinet, I2P, Freenet

Показать описание
This is a primer on how you can layer a hidden network over the public networks and operate only in a completely encrypted environment. This video will cover TOR, Lokinet, I2P, Freenet and the specific applications of the darknet vs the darkweb.
-----------------------------------
-----------------------------------
Merch Store
-----------------------------------
I'm the Internet Privacy Guy. I'm a public interest technologist. I'm here to educate. You are losing your Internet privacy and Internet security every day if you don't fight for it. Your data is collected with endless permanent data mining. Learn about a TOR router, a VPN , antivirus, spyware, firewalls, IP address, wifi triangulation, data privacy regulation, backups and tech tools, and evading mass surveillance from NSA, CIA, FBI. Learn how to be anonymous on the Internet so you are not profiled. Learn to speak freely with pseudo anonymity. Learn more about the dangers of the inernet and the dangers of social media, dangers of email.
I like alternative communication technology like Amateur Radio and data communications using Analog. I'm a licensed HAM operator.
Please follow me on
Odysee
Rumble
-----------------------------------
-----------------------------------
Merch Store
-----------------------------------
I'm the Internet Privacy Guy. I'm a public interest technologist. I'm here to educate. You are losing your Internet privacy and Internet security every day if you don't fight for it. Your data is collected with endless permanent data mining. Learn about a TOR router, a VPN , antivirus, spyware, firewalls, IP address, wifi triangulation, data privacy regulation, backups and tech tools, and evading mass surveillance from NSA, CIA, FBI. Learn how to be anonymous on the Internet so you are not profiled. Learn to speak freely with pseudo anonymity. Learn more about the dangers of the inernet and the dangers of social media, dangers of email.
I like alternative communication technology like Amateur Radio and data communications using Analog. I'm a licensed HAM operator.
Please follow me on
Odysee
Rumble
Комментарии
 0:22:23
0:22:23
 0:11:42
0:11:42
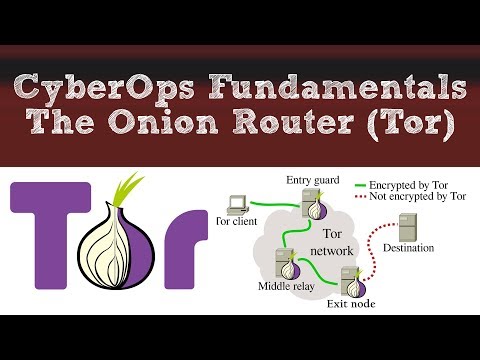 0:03:54
0:03:54
 0:14:19
0:14:19
 0:15:20
0:15:20
 0:05:02
0:05:02
 0:13:15
0:13:15
 0:11:41
0:11:41
 0:05:00
0:05:00
 0:00:20
0:00:20
 0:00:33
0:00:33
 0:07:41
0:07:41
 0:00:55
0:00:55
 0:18:13
0:18:13
 0:06:24
0:06:24
 0:01:02
0:01:02
 0:00:49
0:00:49
 0:06:14
0:06:14
 0:10:57
0:10:57
 0:02:09
0:02:09
 0:00:37
0:00:37
 1:18:09
1:18:09
 0:00:59
0:00:59
 0:00:45
0:00:45