filmov
tv
What is Tor (The Onion Router)? [2023]

Показать описание
Tor, short for "The Onion Router," is a network protocol and a free open-source software project that aims to provide users with privacy and anonymity on the internet. It allows individuals to browse the web, send messages, and access online resources while maintaining their privacy and protecting their online activities from surveillance and censorship.
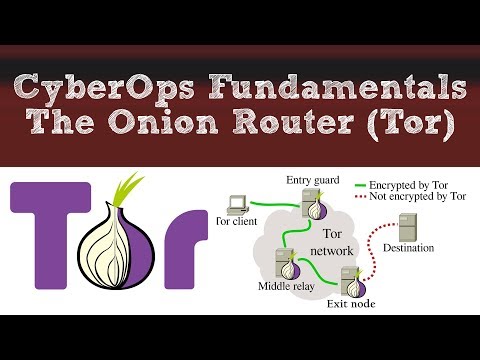
Tor operates by routing internet traffic through a network of volunteer-operated relays, which are distributed across the globe. When a user connects to the Tor network, their internet traffic is encrypted and passed through a series of these relays, creating a layered and anonymous pathway. Each relay only knows the IP address of the previous relay and the next relay in the chain, ensuring that no single relay or entity has complete visibility into the entire network flow.
This layered routing gives rise to the term "onion routing." It refers to the fact that, similar to the layers of an onion, the user's traffic is encapsulated in multiple layers of encryption as it passes through each relay. This makes it extremely difficult for anyone monitoring the network to trace the origin and destination of the traffic.
Tor also incorporates a feature called "hidden services" or the Tor Hidden Service Protocol (THS). Hidden services allow websites and services to be hosted on the Tor network, making them accessible only through Tor. These sites have addresses ending with ".onion" and are known for providing an extra layer of anonymity for both the server and the user.
The primary goals of Tor are to protect users' privacy, prevent censorship, and enable individuals to bypass geographical restrictions. It is widely used by journalists, activists, whistleblowers, and individuals who wish to maintain their privacy online. However, it's worth noting that while Tor provides strong anonymity and privacy protections, it can still be subject to certain attacks or vulnerabilities, and users should exercise caution and be aware of potential risks when using the network.
Tor operates by routing internet traffic through a network of volunteer-operated relays, which are distributed across the globe. When a user connects to the Tor network, their internet traffic is encrypted and passed through a series of these relays, creating a layered and anonymous pathway. Each relay only knows the IP address of the previous relay and the next relay in the chain, ensuring that no single relay or entity has complete visibility into the entire network flow.
This layered routing gives rise to the term "onion routing." It refers to the fact that, similar to the layers of an onion, the user's traffic is encapsulated in multiple layers of encryption as it passes through each relay. This makes it extremely difficult for anyone monitoring the network to trace the origin and destination of the traffic.
Tor also incorporates a feature called "hidden services" or the Tor Hidden Service Protocol (THS). Hidden services allow websites and services to be hosted on the Tor network, making them accessible only through Tor. These sites have addresses ending with ".onion" and are known for providing an extra layer of anonymity for both the server and the user.
The primary goals of Tor are to protect users' privacy, prevent censorship, and enable individuals to bypass geographical restrictions. It is widely used by journalists, activists, whistleblowers, and individuals who wish to maintain their privacy online. However, it's worth noting that while Tor provides strong anonymity and privacy protections, it can still be subject to certain attacks or vulnerabilities, and users should exercise caution and be aware of potential risks when using the network.
 0:04:54
0:04:54
 0:14:19
0:14:19
 0:03:54
0:03:54
 0:02:01
0:02:01
 0:02:25
0:02:25
 0:03:33
0:03:33
 0:06:14
0:06:14
 0:08:18
0:08:18
 0:05:00
0:05:00
 0:14:49
0:14:49
 0:01:02
0:01:02
 0:23:48
0:23:48
 0:06:50
0:06:50
 0:42:50
0:42:50
 0:11:42
0:11:42
 0:10:57
0:10:57
 0:01:14
0:01:14
 0:11:46
0:11:46
 0:24:54
0:24:54
 0:06:24
0:06:24
 0:55:24
0:55:24
 0:05:02
0:05:02
 0:11:54
0:11:54
 0:08:54
0:08:54