filmov
tv
Hack All The Things: 20 Devices in 45 Minutes
Показать описание
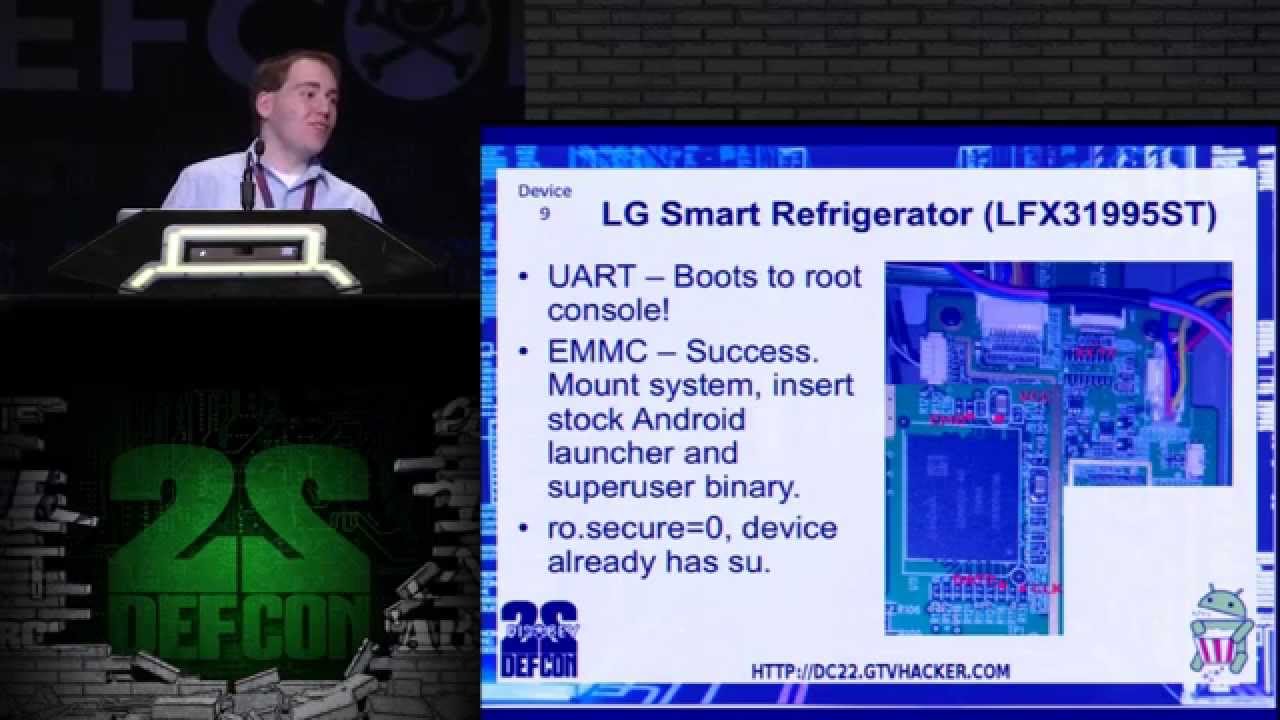
When we heard Hack All The Things, we took it as a challenge. So at DEF CON this year we're doing exactly that, we're hacking everything. We've taken all of our previous experience exploiting embedded devices and used it to bring you a presentation filled with more exploits than ever before™. This presentation will feature exploits for over 20 devices including but not limited to TVs, baby monitors, media streamers, network cameras, home automation devices, and VoIP gateways. Gain root on your devices, run unsigned kernels; it's your hardware, it's internet connected, and it's horribly insecure.
Follow us at: @Exploiteers
Follow us at: @Exploiteers
Hack All The Things: 20 Devices in 45 Minutes
he hacked my websites
Secret hack for Toca boca
War Robots Components Hack
This trick makes your arms look 2x bigger (skinny guy hack)
PC keyboard light on hacks |#lifehack |#hack | #short | #video | #shortsvideos
😳 best mom and dad hack to avoid poop being smeared all of the wall #mom #momhack #hack #lifehack
Vegas Hotel Hack: I tried the $20 Trick at 3 Hotels (what happened)?
vCon pre TADHack Session 20th Sep Intro and Developer Requests
Hack prank on friend! #shorts
iOS 18 - 20 Settings You NEED to Change Immediately
hack
Book Hack #shorts
How to Legally Rob Walmart (SECRET HACK) #shorts
CRAZY BLOX FRUITS HACK I FOUND
Balloon Life Hack | 5 minutes craft | #shorts
Don't Believe Viral Hack👅 Part-2 🤯😱😳 #shorts #trendinghacks #viralshorts #viralhacks #short #ha...
I Ruined My Skin with this Beauty Hack... #shorts #skincare
DC motor Amazing Hack | howto | Fan and USB #shorts
How to MEMORIZE Large Amounts of Information Quickly - Perfect Memory Hack #17
solder not sticking to tip #shorts #hack
How to hack any Roblox Account
Can A Flipper Zero Hack A PHONE? #Shorts
Light Bulb + Battery Life Hack You Won’t Believe!!!! 💡😵
Комментарии
 0:48:50
0:48:50
 0:34:24
0:34:24
 0:00:05
0:00:05
 0:00:21
0:00:21
 0:00:44
0:00:44
 0:00:13
0:00:13
 0:00:09
0:00:09
 0:07:26
0:07:26
 0:21:04
0:21:04
 0:00:20
0:00:20
 0:12:45
0:12:45
 0:01:30
0:01:30
 0:00:36
0:00:36
 0:01:00
0:01:00
 0:00:39
0:00:39
 0:00:19
0:00:19
 0:00:27
0:00:27
 0:00:26
0:00:26
 0:00:51
0:00:51
 0:16:53
0:16:53
 0:00:44
0:00:44
 0:00:44
0:00:44
 0:00:44
0:00:44
 0:00:14
0:00:14