filmov
tv
researcher accidentally finds 0-day affecting his entire internet service provider

Показать описание
This is truly one of the craziest scenarios I've ever seen. An API endpoint left wide open lets you hack anyone's router.
Thanks for letting me make this video Sam!
🛒 GREAT BOOKS FOR THE LOWEST LEVEL🛒
🔥🔥🔥 SOCIALS 🔥🔥🔥
Thanks for letting me make this video Sam!
🛒 GREAT BOOKS FOR THE LOWEST LEVEL🛒
🔥🔥🔥 SOCIALS 🔥🔥🔥
researcher accidentally finds 0-day affecting his entire internet service provider
When you Accidentally Compromise every CPU on Earth
THIS IS NOT A WAVE BUT THE ENTIRE OCEAN FOLDING OVER
Cybersecurity Expert Demonstrates How Hackers Easily Gain Access To Sensitive Information
Mistakenly Grabbing Molten Glass (For safety/hazard education, don’t try!) #shorts
Psychiatrist films her own panic attack. #drsasha #panicattack #anxiety #shorts
This Zombie Virus Was Just Found...
How Microsoft Accidentally Backdoored 270 MILLION Users
Whatever This Stupid Girl Answers In Exam Becomes Reality & World Turns Chaotic
The boy randomly pressed the ATM, and the balance doubled by 1000 times, and he became a millionaire
Photos Taken Before Horrible Disasters😨
'Internet meme ruined my career' BBC News
😱What if ACCIDENTALLY different Blood Group is Injected in Your Body? #shorts
Accidental Discoveries That Changed The World
Could 2 People Actually Repopulate Earth
The accident that changed the world - Allison Ramsey and Mary Staicu
Drones Sacrificed for Spectacular Volcano Video | National Geographic
When A Criminal Is Smarter Than The Police
How fentanyl kills: A CBC News explainer
Antikythera Mechanism: The ancient 'computer' that simply shouldn't exist - BBC REEL
The Most Controversial Problem in Philosophy
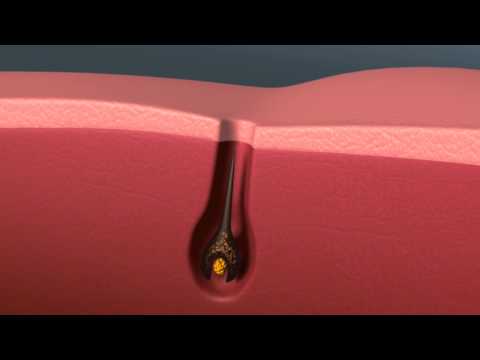
The Hair Growth Cycle
This Dinosaur Was Literally Alive One Week Ago. Dinosaur Found in Perfect Condition
Elon Musk Tells Us What The Navy Saw While Diving in the Ocean
Комментарии
 0:29:02
0:29:02
 0:15:59
0:15:59
 0:00:23
0:00:23
 0:03:27
0:03:27
 0:00:19
0:00:19
 0:00:59
0:00:59
 0:00:35
0:00:35
 0:14:45
0:14:45
 0:10:32
0:10:32
 0:10:15
0:10:15
 0:00:43
0:00:43
 0:02:11
0:02:11
 0:00:57
0:00:57
 0:05:38
0:05:38
 0:13:59
0:13:59
 0:04:51
0:04:51
 0:03:30
0:03:30
 0:13:15
0:13:15
 0:01:47
0:01:47
 0:06:54
0:06:54
 0:10:19
0:10:19
 0:00:20
0:00:20
 0:24:06
0:24:06
 0:20:13
0:20:13