filmov
tv
Zero Trust Explained in 4 mins

Показать описание
A zero trust approach aims to wrap security around every user, every device, every connection — every time. Unify and integrate your security tools to protect your most valuable assets and proactively manage threats.
#ZeroTrust #CloudSecurity #IBMSecurity
Zero Trust Explained in 4 mins
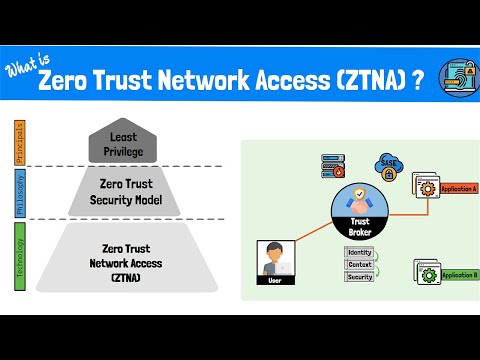
What is Zero Trust Network Access (ZTNA)? The Zero Trust Model, Framework and Technologies Explained
Zero Trust Explained | Real World Example
What is Zero Trust? (explained in 1 min)
Zero Trust In Four Minutes
Zero Trust Explained
Zero Trust Architecture Explained
What is Cisco Zero Trust?
What are the Principles of Zero Trust Security?
What is Zero Trust?
Why Implement Zero Trust
Cybersecurity and Zero Trust
Zero Trust in 5 Minutes with Brian Deitch
Zero Trust Authentication Defined
What is zero trust security?
Microsoft Zero Trust Security for Endpoints
Cybersecurity Zero Trust Architecture : Explained For Beginners
What is Zero Trust Security?
Zero Trust - CompTIA Security+ SY0-701 - 1.2
The 4 Phases of the Zero Trust Journey
Zero Trust Explained | Cybersecurity Insights #17
Zero Trust Network Access (ZTNA) vs Virtual Private Networking (VPN)
Making Zero Trust Real - Governance
TechBullets: Top 4 Use Cases for a Zero Trust Data Center
Комментарии
 0:03:43
0:03:43
 0:07:44
0:07:44
 0:21:46
0:21:46
 0:01:15
0:01:15
 0:04:02
0:04:02
 0:02:12
0:02:12
 0:13:55
0:13:55
 0:02:31
0:02:31
 0:07:44
0:07:44
 0:01:34
0:01:34
 0:06:57
0:06:57
 0:17:59
0:17:59
 0:04:39
0:04:39
 0:05:06
0:05:06
 0:02:31
0:02:31
 0:15:23
0:15:23
 0:32:47
0:32:47
 0:04:17
0:04:17
 0:10:05
0:10:05
 0:34:28
0:34:28
 0:02:30
0:02:30
 0:10:24
0:10:24
 0:16:59
0:16:59
 0:02:07
0:02:07