filmov
tv
Zero Trust Explained | Cybersecurity Insights #17

Показать описание
What is Zero Trust?
Imagine walking through an airport and having to validate your trustworthiness with every stride. That’s Zero Trust! It is a ‘verify all’ approach. Never trust; always verify every relationship – networks, devices, data, apps, and users – at every step.
Benefits of Zero Trust
Applying Zero Trust provides three main benefits: improved intelligence, faster containment, and better performance. Intelligence – understand your security posture. Containment – trap the threat to prevent it from advancing. Performance – through segmentation, there are fewer resources so system traffic does not get bogged down.
Asset intelligence is the foundation of Zero Trust; without knowledge of what you have, there’s no way to know what needs verifying. Get on the Zero Trust path and achieve persistent security.
----
Watch more episodes of the Cybersecurity Insights series:
----
Endpoint Risk Report
Zero Trust Explained in 4 mins
Cybersecurity and Zero Trust
Zero Trust Explained | Cybersecurity Insights #17
Zero Trust Explained | Real World Example
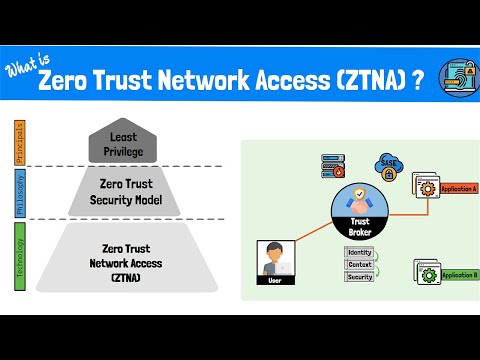
What is Zero Trust Network Access (ZTNA)? The Zero Trust Model, Framework and Technologies Explained
Is Zero Trust Security The Holy Grail of Cybersecurity?
What is zero trust in cybersecurity?
Zero Trust Explained
🎓 MASTERCLASS: Digital Transformation & Business Strategy | The Ultimate Guide for 2025–2030 and...
What Is Zero Trust? An Easy Explanation In 60 Seconds
Zero Trust - CompTIA Security+ SY0-701 - 1.2
Cybersecurity Zero Trust Architecture : Explained For Beginners
What are the Principles of Zero Trust Security?
Zero Trust : Explained The Future of Cybersecurity
Zero Trust Explained: 👉The Cybersecurity Game-Changer!💡
Zero Trust Security Model Explained
zero trust explained-#cyberSecurity #cyberAwareness
Zero Trust Explained #cybersecurity #zerotrust
What is zero trust security?
What is zero trust architecture?
Zero Trust Architecture Explained in 1 Minute! 🔒| Cyber Security Concepts
Key Principles of Zero-Trust Security Explained
Zero Trust in 5 Minutes with Brian Deitch
'What is Zero Trust Security? The Future of Cybersecurity Explained!'
Комментарии
 0:03:43
0:03:43
 0:17:59
0:17:59
 0:02:30
0:02:30
 0:21:46
0:21:46
 0:07:44
0:07:44
 0:08:39
0:08:39
 0:06:14
0:06:14
 0:02:12
0:02:12
 1:29:10
1:29:10
 0:01:18
0:01:18
 0:10:05
0:10:05
 0:32:47
0:32:47
 0:07:44
0:07:44
 0:06:35
0:06:35
 0:01:29
0:01:29
 0:05:27
0:05:27
 0:02:06
0:02:06
 0:01:38
0:01:38
 0:02:31
0:02:31
 0:03:02
0:03:02
 0:00:54
0:00:54
 0:03:24
0:03:24
 0:04:39
0:04:39
 0:05:10
0:05:10