filmov
tv
Zero Trust Explained

Показать описание
By implementing Zero Trust, you can reduce risk, build trust, and improve protection across your identities, devices, applications, data, infrastructure, and networks.
Today’s organizations need a new security model that more effectively adapts to the complexity of the modern environment, embraces the mobile workforce, and protects people, devices, apps, and data wherever they’re located.
► Follow us on social:
#MicrosoftSecurity #ZeroTrust
Today’s organizations need a new security model that more effectively adapts to the complexity of the modern environment, embraces the mobile workforce, and protects people, devices, apps, and data wherever they’re located.
► Follow us on social:
#MicrosoftSecurity #ZeroTrust
Zero Trust Explained in 4 mins
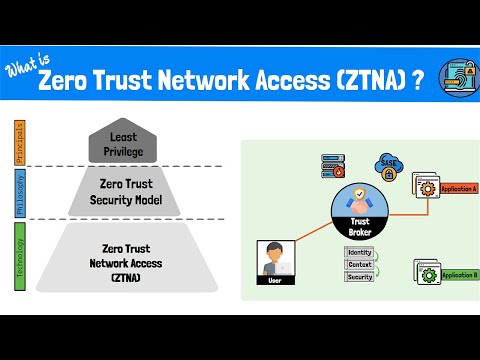
What is Zero Trust Network Access (ZTNA)? The Zero Trust Model, Framework and Technologies Explained
Zero Trust Explained
Zero Trust Explained | Real World Example
Zero Trust in 5 Minutes with Brian Deitch
Cybersecurity and Zero Trust
Zero Trust - CompTIA Security+ SY0-701 - 1.2
What is zero trust in cybersecurity?
Exploring Azure Identity, Access and Security | #AZ900withNavika
Zero Trust Architecture Explained
How Zero Trust Security Works
Overview of Zero Trust Architectures
🔥Zero Trust Security Model Explained Simply | What is Zero Trust Security?
Understanding and Getting Started with ZERO TRUST
What is Zero Trust Security? (with Palo Alto Networks) | CXOTalk
Why Implement Zero Trust
What is Zero Trust Security?
Zscaler Zero Trust Exchange Explained | 5-min Overview
Zero Trust Authentication and Architecture within NIST 800-207 Framework
Cybersecurity Zero Trust Architecture : Explained For Beginners
Zero Trust Explained | Cybersecurity Insights #17
What Is Zero Trust Network Access (ZTNA)?
What is Zero Trust: Basics explained
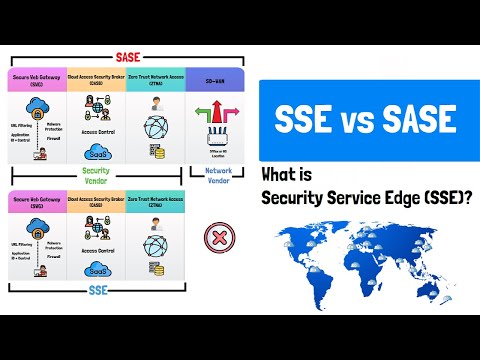
What is Security Service Edge (SSE)? SASE vs SSE vs VPN
Комментарии
 0:03:43
0:03:43
 0:07:44
0:07:44
 0:21:46
0:21:46
 0:04:39
0:04:39
 0:17:59
0:17:59
 0:10:05
0:10:05
 0:06:14
0:06:14
 0:53:12
0:53:12
 0:01:41
0:01:41
 0:04:38
0:04:38
 0:45:42
0:45:42
 0:12:25
0:12:25
 0:57:11
0:57:11
 0:14:52
0:14:52
 0:06:57
0:06:57
 0:01:31
0:01:31
 0:05:26
0:05:26
 0:10:28
0:10:28
 0:32:47
0:32:47
 0:02:30
0:02:30
 0:03:36
0:03:36
 0:03:39
0:03:39
 0:06:36
0:06:36