filmov
tv
Cybersecurity and Zero Trust

Показать описание
With cyber attacks becoming ever more sophisticated, cyber security has become a very hot topic.
In this video, Bob Kalka explains three major trends in cybersecurity today: zero trust, threat management, and modernization.
Chapters
0:00 - Intro
0:15 - Zero Trust
3:14 - Identity Governance
3:31 - Identity Analytics
3:48 - Privileged Account Management
4:21 - Access Management
4:33 - Adaptive Authentication
5:54 - Discovery & Classification
6:08 - Encryption
6:17 - Data & File Activity Monitoring
6:33 - Key Management
7:22 - Data Risk Insights
7:49 - Transactional Fraud
7:54 - Configuration Management
9:20 - Threat Management
14:30 - Modernization
16:05 - A Federated Approach
17:39 - Conclusion
#CyberSecurity #ZeroTrust #IBMSecurity
Cybersecurity and Zero Trust
Zero Trust Explained in 4 mins
Zero Trust - CompTIA Security+ SY0-701 - 1.2
Zero Trust Explained | Real World Example
What is zero trust in cybersecurity?
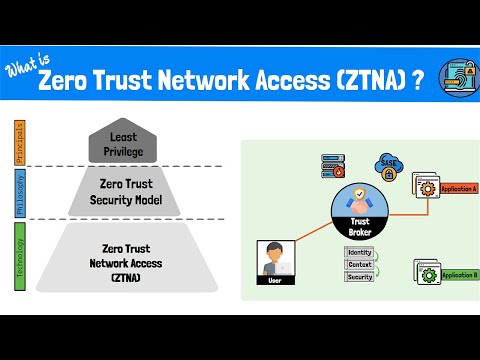
What is Zero Trust Network Access (ZTNA)? The Zero Trust Model, Framework and Technologies Explained
Is Zero Trust Security The Holy Grail of Cybersecurity?
Zero Trust Cybersecurity for Mobile Endpoint
Why Zero Trust is the Key to Cybersecurity in 2024 and Beyond
Zero Trust in 5 Minutes with Brian Deitch
Zero Trust Explained | Cybersecurity Insights #17
Cybersecurity Journey to Zero Trust: Episode 1
Zero Trust Explained
How Zero Trust Security Works
Understanding and Getting Started with ZERO TRUST
ASC2020 - Zero Trust Model of Cybersecurity - Ahmed Abdelhamid
Zero Trust Cybersecurity Explained
The Cybersecurity Moonshot and Zero Trust
Zero Trust + AI: the future of cybersecurity
Overview of Zero Trust Architectures
Cybersecurity Journey to Zero Trust: Episode 4
What is Zero Trust Security? (with Palo Alto Networks) | CXOTalk
Cybersecurity Journey to Zero Trust: Episode 3
No More Firewalls! How Zero-Trust Networks Are Reshaping Cybersecurity
Комментарии
 0:17:59
0:17:59
 0:03:43
0:03:43
 0:10:05
0:10:05
 0:21:46
0:21:46
 0:06:14
0:06:14
 0:07:44
0:07:44
 0:08:39
0:08:39
 0:06:19
0:06:19
 0:12:16
0:12:16
 0:04:39
0:04:39
 0:02:30
0:02:30
 0:32:10
0:32:10
 0:02:12
0:02:12
 0:04:38
0:04:38
 0:57:11
0:57:11
 0:57:42
0:57:42
 0:10:21
0:10:21
 0:18:13
0:18:13
 0:01:04
0:01:04
 0:45:42
0:45:42
 0:25:58
0:25:58
 0:14:52
0:14:52
 0:19:04
0:19:04
 0:45:02
0:45:02