filmov
tv
How to fix the Log4j vulnerability on Windows Server

Показать описание
How to fix the Log4j vulnerability on Windows Server
CVE-2021-44228 Apache Log4j
Command to search for the file:
Variable name:LOG4J_FORMAT_MSG_NO_LOOKUPS
Variable value: true
Powershell command to set the variable:
[System.Environment]::SetEnvironmentVariable('LOG4J_FORMAT_MSG_NO_LOOKUPS','true',[System.EnvironmentVariableTarget]::Machine)
How to fix the Log4j vulnerability on Windows Server
How to mitigate Log4j vulnerability | Example | log4j 2.17 | step by step update | imp links #log4j2
Logs on Fire? | Log4j Vulnerability | How to remediate them ASAP? | Tech Primers
How to Fix Log4j Vulnerability? (Windows, Mac, and Linux)
The Log4j Vulnerability: Patching and Mitigation
Log4j Vulnerability | How to protect your Systems and Servers from Log4j | Fix this ASAP!!!
How to find Log4j version | step by step log4j update | Example | log4j vulnerability fix #log4j
log4j vulnerability fix with maven
How to mitigate the Log4j vulnerability on Windows servers for Fastvue Reporter (the correct way!)
Latest Update on Log4j Security Issue: How to fix log4j issue in Eclipse/IntelliJ/.m2/CommandLine
Apache Log4j Security Vulnerabilities: What we need to do?
How to Fix the Log4J Exploit in Minecraft Client
Log4j2 sample code Non Maven Project | Fix Log4j Security Vulnerabilities | Java Programming
How to Fix the Minecraft Java Security Exploit (Minecraft Log4j Security Bug Fix)
log4j vulnerability fix | internet on fire 🔥 #log4j #vulnerability
How to fix the Log4j2 vulnerability | Mitigate Log4J CVE2021-44228 Zero-Day Without Patching
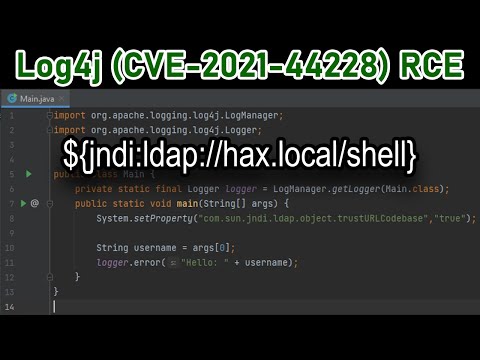
Log4j (CVE-2021-44228) RCE Vulnerability Explained
How to fix the new Log4J Hack on Minecraft!
Free Resources for Log4Shell Mitigation [fix Log4j CVE-2021-44228]
How to fix the Log4J RCE Exploit In Minecraft (and how to check it) | Cerhanz
How to fix the Java Apache Log4j bug (Minecraft chat vulnerability issue)
Log4j Vulnerability explained and fix CVE-2021-44832
How to fix the Java Apache Log4j bug (Minecraft chat vulnerability issue) TLauncher
How to fix the Java Apache Log4j bug (Minecraft chat vulnerability issue) Minecraft Launcher
Комментарии
 0:03:05
0:03:05
 0:11:35
0:11:35
 0:15:04
0:15:04
 0:01:40
0:01:40
 0:11:19
0:11:19
 0:03:34
0:03:34
 0:11:50
0:11:50
 0:00:39
0:00:39
 0:00:57
0:00:57
 0:20:35
0:20:35
 0:08:20
0:08:20
 0:01:11
0:01:11
 0:08:54
0:08:54
 0:16:44
0:16:44
 0:06:57
0:06:57
 0:04:19
0:04:19
 0:03:44
0:03:44
 0:00:47
0:00:47
 0:10:55
0:10:55
 0:03:01
0:03:01
 0:00:33
0:00:33
 0:07:40
0:07:40
 0:00:34
0:00:34
 0:00:34
0:00:34