filmov
tv
How do hackers get into your account?
Показать описание
How do hackers get into your system?
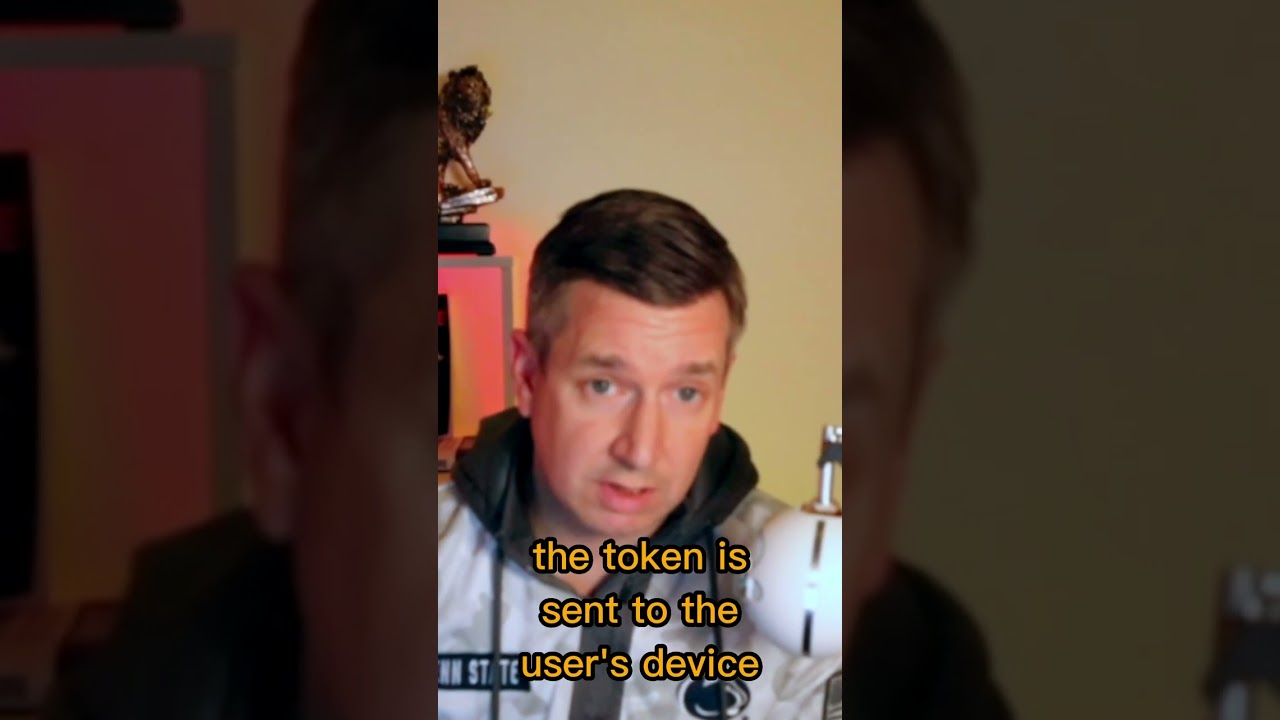
A man in the middle attack occurs when a hacker intercepts and alters communication between a user and a multi factor authentication server.
This enables the hacker to obtain the user's login credentials and also acquire the token that verifies the device's trustworthiness to services such as Microsoft or Google.
The token is transmitted to the user's device and can be stored there.
The hacker can then insert the token into a request sent to the server from the user's browser, which the server will recognize as a trusted device and grant access without the need for the user to enter their username, password, or multi factor authentication token.
#hackers
#multifactorauthentication
#cybersecurity
#protectyourbusiness
---
Bryan Hornung leads the top cyber security firm, Xact IT Solutions. With over 20 years of extensive experience in the field of cybersecurity, he is committed to his mission of empowering businesses. Bryan is dedicated to helping others build rock-solid security programs that protect against malicious hackers, drive business growth, and safeguard their reputation from potential damage caused by cyber threats.
A man in the middle attack occurs when a hacker intercepts and alters communication between a user and a multi factor authentication server.
This enables the hacker to obtain the user's login credentials and also acquire the token that verifies the device's trustworthiness to services such as Microsoft or Google.
The token is transmitted to the user's device and can be stored there.
The hacker can then insert the token into a request sent to the server from the user's browser, which the server will recognize as a trusted device and grant access without the need for the user to enter their username, password, or multi factor authentication token.
#hackers
#multifactorauthentication
#cybersecurity
#protectyourbusiness
---
Bryan Hornung leads the top cyber security firm, Xact IT Solutions. With over 20 years of extensive experience in the field of cybersecurity, he is committed to his mission of empowering businesses. Bryan is dedicated to helping others build rock-solid security programs that protect against malicious hackers, drive business growth, and safeguard their reputation from potential damage caused by cyber threats.
 0:13:07
0:13:07
 0:05:54
0:05:54
 0:11:55
0:11:55
 0:01:00
0:01:00
 0:00:31
0:00:31
 0:00:50
0:00:50
 0:03:27
0:03:27
 0:00:57
0:00:57
 0:01:00
0:01:00
 0:02:16
0:02:16
 0:05:42
0:05:42
 0:03:07
0:03:07
 0:06:05
0:06:05
 0:09:47
0:09:47
 0:00:58
0:00:58
 0:02:13
0:02:13
 0:09:48
0:09:48
 0:05:42
0:05:42
 0:07:30
0:07:30
 0:07:09
0:07:09
 0:09:06
0:09:06
 0:00:58
0:00:58
 0:18:16
0:18:16
 0:07:56
0:07:56