filmov
tv
Zero Trust Cybersecurity Explained: Top Tips For Ultimate Online Security

Показать описание
🚨 Cybersecurity Tip of the Day: Understanding Zero Trust Environments 🚨
In today’s evolving threat landscape, organizations need to shift their mindset from "trust but verify" to "never trust, always verify." This is the essence of a Zero Trust environment.
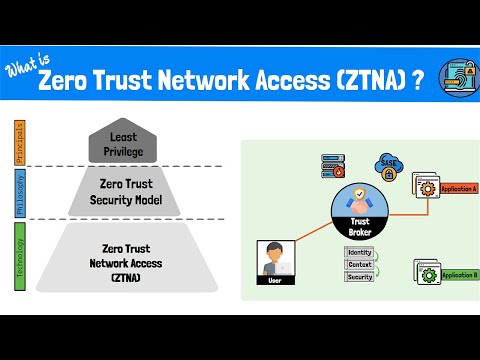
🔒 What is Zero Trust? Zero Trust is a security framework that assumes no one—inside or outside the network—should be trusted by default. Instead, every user, device, and application must be continuously authenticated, authorized, and validated before being granted access to critical resources.
Why is Zero Trust important?
Reduces the Risk of Data Breaches: By minimizing implicit trust, Zero Trust limits the potential for malicious actors to move laterally within the network.
Protects Remote Workforces: As remote work and BYOD policies grow, Zero Trust provides a robust defense against potential vulnerabilities.
Adapts to Modern Threats: With cyber threats becoming more sophisticated, a Zero Trust approach ensures that organizations stay one step ahead.
🌐 Adopting a Zero Trust model is not just a trend; it’s a necessity in the digital age. It’s about building a security-first culture that focuses on resilience, vigilance, and continuous improvement.
💬 What’s your organization doing to embrace Zero Trust? Share your thoughts below!
#CyberSecurity #ZeroTrust #DataProtection #InfoSec #CyberAwareness #SecurityBestPractices #innovativetechnologies #upstatetechsupport
In today’s evolving threat landscape, organizations need to shift their mindset from "trust but verify" to "never trust, always verify." This is the essence of a Zero Trust environment.
🔒 What is Zero Trust? Zero Trust is a security framework that assumes no one—inside or outside the network—should be trusted by default. Instead, every user, device, and application must be continuously authenticated, authorized, and validated before being granted access to critical resources.
Why is Zero Trust important?
Reduces the Risk of Data Breaches: By minimizing implicit trust, Zero Trust limits the potential for malicious actors to move laterally within the network.
Protects Remote Workforces: As remote work and BYOD policies grow, Zero Trust provides a robust defense against potential vulnerabilities.
Adapts to Modern Threats: With cyber threats becoming more sophisticated, a Zero Trust approach ensures that organizations stay one step ahead.
🌐 Adopting a Zero Trust model is not just a trend; it’s a necessity in the digital age. It’s about building a security-first culture that focuses on resilience, vigilance, and continuous improvement.
💬 What’s your organization doing to embrace Zero Trust? Share your thoughts below!
#CyberSecurity #ZeroTrust #DataProtection #InfoSec #CyberAwareness #SecurityBestPractices #innovativetechnologies #upstatetechsupport
 0:17:59
0:17:59
 0:01:09
0:01:09
 0:07:44
0:07:44
 0:02:30
0:02:30
 0:21:46
0:21:46
 0:04:56
0:04:56
 0:45:42
0:45:42
 0:04:39
0:04:39
 1:10:37
1:10:37
 0:08:39
0:08:39
 0:02:12
0:02:12
 0:08:48
0:08:48
 0:03:39
0:03:39
 0:10:05
0:10:05
 0:07:38
0:07:38
 0:01:07
0:01:07
 0:00:26
0:00:26
 0:49:39
0:49:39
 0:12:25
0:12:25
 0:17:34
0:17:34
 0:30:26
0:30:26
 0:02:14
0:02:14
 0:09:25
0:09:25
 0:47:05
0:47:05