filmov
tv
How Hackers Bypass Two-Factor Authentication (2FA)?!

Показать описание
// Membership //
// Courses //
// Books //
// Social Links //
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
// Courses //
// Books //
// Social Links //
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
How Hackers Bypass Two-Factor Authentication (2FA)?!
Hackers Bypass Google Two-Factor Authentication (2FA) SMS
How Hackers Bypass Two Factor Authentication
how hackers bypass 2 step verification
How storing passwords let hackers bypass two factor authentication
Hacking Two Factor Authentication: Four Methods for Bypassing 2FA and MFA
Google 2 steps authentication bypass
BYPASS 2FA Vulnerability - PoC
Here's how hackers can get around 2-factor authentication
Two Factor Authentication(2FA) Bypass Using Brute-Force Attack
How Hackers Bypass MFA! - (Multi-Factor Authentication)
How hackers Bypass Multi Factor Authentication | Evilginx 2
This hack can bypass 2FA - What to look out for!
Two Factor Authentication(2FA) Bypass | 2FA Broken Logic
Hackers Bypass Google Two-Factor Authentication (2FA)
How Hackers Bypass Two Factor Authentication (2FA) And How to Protect Yourself part 1
2FA Bypass | Authentication solution
How hackers bypass two factor authentication #stackingsup #hacking #cybersecurity #cyberawareness
This Is How Hackers Bypass 2 Step Verification
How to Hack MFA (Multi-Factor Authentication)
Working Fix! | Facebook 2 Factor Authentication Problem | Locked Out of Facebook 2FA Bypass
NEW! How to Bypass Two Factor Authentication 2FA Problem on Facebook 2024 Locked Out of Facebook
How hackers bypass 2FA
MFA Can Be Easily Bypassed - Here's How
Комментарии
 0:09:20
0:09:20
 0:12:47
0:12:47
 0:01:10
0:01:10
 0:16:59
0:16:59
 0:08:29
0:08:29
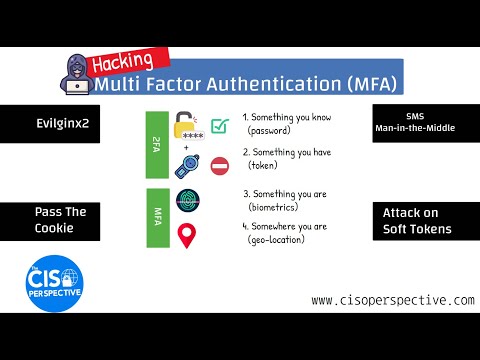 0:10:16
0:10:16
 0:00:56
0:00:56
 0:01:04
0:01:04
 0:02:01
0:02:01
 0:10:30
0:10:30
 0:25:14
0:25:14
 0:08:14
0:08:14
 0:02:30
0:02:30
 0:07:47
0:07:47
 0:06:13
0:06:13
 0:00:48
0:00:48
 0:02:57
0:02:57
 0:00:12
0:00:12
 0:08:39
0:08:39
 0:08:57
0:08:57
 0:05:48
0:05:48
 0:10:21
0:10:21
 0:01:01
0:01:01
 0:09:22
0:09:22