filmov
tv
Two Factor Authentication(2FA) Bypass Using Brute-Force Attack

Показать описание
During video we see how a weak protection against brute force attacks allows an attacker to automate a multi-step authentication process and successfully brute force verification code to bypass 2 factor authentication and log into the victim account.
Web Security Academy | Lab: 2FA bypass using a brute-force attack
NOTE: This video is made ONLY for educational purposes and to help developers and security researchers to enhance their security knowledge. Therefore, allowing them to remediate potential vulnerabilities in their OWN applications.
Web Security Academy | Lab: 2FA bypass using a brute-force attack
NOTE: This video is made ONLY for educational purposes and to help developers and security researchers to enhance their security knowledge. Therefore, allowing them to remediate potential vulnerabilities in their OWN applications.
Two Factor Authentication(2FA) Bypass Using Brute-Force Attack
How Hackers Bypass Two-Factor Authentication (2FA)?!
Hacking 101 - 2FA bypass with cookie replay attack #cyber #cybersecurity #tech
Hackers Bypass Google Two-Factor Authentication (2FA) SMS
🔴How to Bypass Two Factor Authentication 2FA Problem on Facebook 2024 | break Facebook 2Factor
Hacking Two Factor Authentication: Four Methods for Bypassing 2FA and MFA
Two Factor Authentication(2FA) Bypass | 2FA Broken Logic
MFA Can Be Easily Bypassed - Here's How
BYPASS 2FA Vulnerability - PoC
Working Fix! | Facebook 2 Factor Authentication Problem | Locked Out of Facebook 2FA Bypass
2FA Bypass | Authentication solution
STOP using this Two-Factor Authentication (2FA) method!
How to Login Facebook without Two Factor Authentication Code 2025 Bypass 2FA Problem Facebook 2025
2FA Bypass | How to Bypass OTP with Burp Suite | bug bounty poc | 2 Methods to bypass 2FA #bugbounty
2FA Bypassing Techniques
2FA simple bypass (Video solution, Audio)
Here's how hackers can get around 2-factor authentication
how hackers bypass 2 step verification
Authentication Vulnerabilities - Lab #14 2FA bypass using a brute-force attack | Short Version
This hack can bypass 2FA - What to look out for!
I Lost My Two-Factor Authentication (2FA) Device. How Do I Sign In?
2FA bypass using a bf attack (Video solution, Audio)
Two Factor Authentication (2FA) Bypass Hacking for LinkedIn (Joe the Hacker)
Instagram Two factor authentication kaise on kare 🔏 Instagram Two factor authentication Settings
Комментарии
 0:10:30
0:10:30
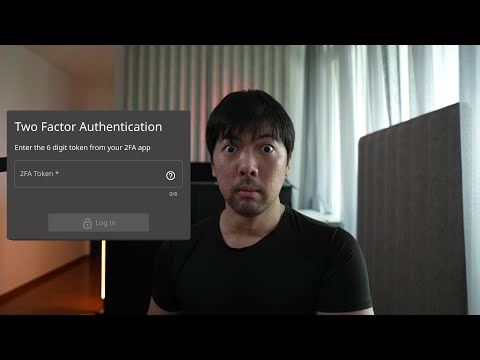 0:09:20
0:09:20
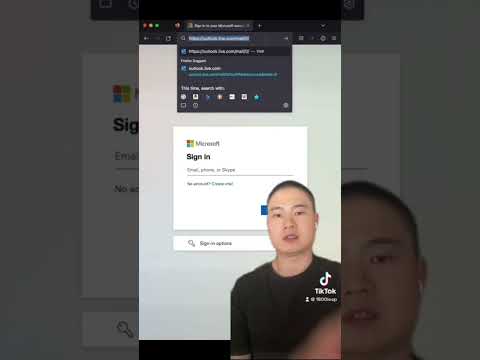 0:00:50
0:00:50
 0:12:47
0:12:47
 0:00:21
0:00:21
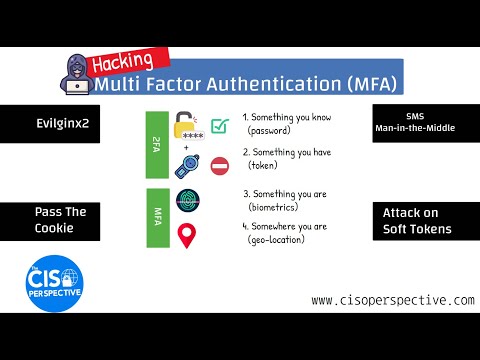 0:10:16
0:10:16
 0:07:47
0:07:47
 0:09:22
0:09:22
 0:01:04
0:01:04
 0:05:48
0:05:48
 0:02:57
0:02:57
 0:05:05
0:05:05
 0:07:07
0:07:07
 0:06:06
0:06:06
 0:12:43
0:12:43
 0:02:09
0:02:09
 0:02:01
0:02:01
 0:16:59
0:16:59
 0:09:39
0:09:39
 0:02:30
0:02:30
 0:07:26
0:07:26
 0:06:08
0:06:08
 0:07:13
0:07:13
 0:00:35
0:00:35