filmov
tv
MFA Can Be Easily Bypassed - Here's How

Показать описание
🔗 Links Mentioned:
🐕 Follow Me:
🤔 Have questions, concerns, comments?:
🎧 Gear:
MFA Can Be Easily Bypassed - Here's How
How Hackers Bypass MFA! - (Multi-Factor Authentication)
MFA Fatigue Attacks - How MFA is Bypassed
How Attackers Bypass MFA (Multi-Factor Authentication) - Security Simplified
Attacker in the Middle - How MFA is Bypassed
Hacking Two Factor Authentication: Four Methods for Bypassing 2FA and MFA
How hackers are breaking into MFA enabled Microsoft 365 accounts
How to Bypass MFA - A Real Time Example (It's easy)
2024-10-30 CERIAS - Many Ways to Hack MFA
How Criminals Bypass Multi-Factor Authentication (MFA)
Is MFA Still Safe? | How Hackers Bypass MFA
How easy it was for bad guys to bypass MFA
Hackers Bypass Google Two-Factor Authentication (2FA) SMS
Bypass MFA (clicking any link?)
Hacks That Bypass Multi-Factor Authentication and How to Make Your MFA Solution Phishing Resistant
BYPASS 2FA Vulnerability - PoC
How session tokens get compromised to bypass MFA
Secure Microsoft 365 Now to Protect Against New MFA Bypass Trick
How Hackers Bypass MFA? [2 Ways To Stop Them]
How to Hack MFA (Multi-Factor Authentication)
Tactical Multi-Factor Authentication (MFA) Bypass Attacks
AiTM ATTACK: How to Bypass any MFA and the Steps You Can Take to Protect Your Business (EN version)
How Do Attackers Bypass MFA?
Mitigating MITM Phishing Toolkit Attacks that Bypass MFA
Комментарии
 0:09:22
0:09:22
 0:25:14
0:25:14
 0:03:55
0:03:55
 0:05:22
0:05:22
 0:03:58
0:03:58
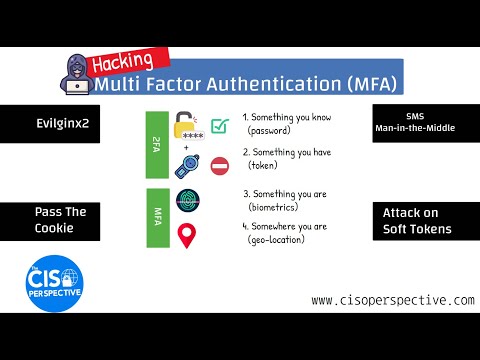 0:10:16
0:10:16
 0:06:00
0:06:00
 0:10:06
0:10:06
 0:57:11
0:57:11
 0:04:18
0:04:18
 0:08:13
0:08:13
 0:15:07
0:15:07
 0:12:47
0:12:47
 0:10:41
0:10:41
 0:00:57
0:00:57
 0:01:04
0:01:04
 0:05:04
0:05:04
 0:03:54
0:03:54
 0:08:34
0:08:34
 0:08:57
0:08:57
 1:20:29
1:20:29
 0:05:24
0:05:24
 0:01:27
0:01:27
 0:52:55
0:52:55