filmov
tv
Zero Trust Security for your APIs by Akshata Sawant

Показать описание
Are you a mid-level developer or an architect who’s curious about API Security and how to achieve it? In that case, we’re excited to help!!
As you already know APIs are the building blocks of your application network. They are the medium of communication and involve a lot of data transactions. As per Gartner’s report, API abuse will be the most frequent vector attack, and it’s quite evident. We have heard about the API abuses and attacks quite often.
In order to protect your APIs and provide complete security we will adopt the Zero Trust Security model. We will learn about the Zero trust model and the architecture. We will also understand how to implement the Zero Trust Security in easy steps.
By the end of the presentation you’ll have a fair idea about API Security and how to protect your API ecosystems using Zero Trust Security. Come along with your queries for us!
As you already know APIs are the building blocks of your application network. They are the medium of communication and involve a lot of data transactions. As per Gartner’s report, API abuse will be the most frequent vector attack, and it’s quite evident. We have heard about the API abuses and attacks quite often.
In order to protect your APIs and provide complete security we will adopt the Zero Trust Security model. We will learn about the Zero trust model and the architecture. We will also understand how to implement the Zero Trust Security in easy steps.
By the end of the presentation you’ll have a fair idea about API Security and how to protect your API ecosystems using Zero Trust Security. Come along with your queries for us!
Zero Trust Explained in 4 mins
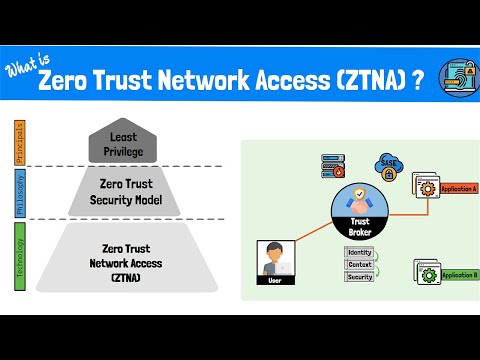
What is Zero Trust Network Access (ZTNA)? The Zero Trust Model, Framework and Technologies Explained
How Zero Trust Security Works
The 7 Principles of Absolute Zero Trust Security With Check Point Infinity
Zero Trust in 5 Minutes with Brian Deitch
Zero Trust Security for your APIs by Akshata Sawant
Zero Trust - CompTIA Security+ SY0-701 - 1.2
Cybersecurity and Zero Trust
Exploring Azure Identity, Access and Security | #AZ900withNavika
Is Zero Trust Security The Holy Grail of Cybersecurity?
What are the Principles of Zero Trust Security?
Zero Trust Security
What is Zero Trust Security?
Zero Trust Explained | Real World Example
Zero Trust Explained
How does endpoint management support your Zero Trust security?
What is Zero Trust Security?
What is zero trust in cybersecurity?
ThreatLocker: Zero Trust vs Malware & Exploits
What is zero trust security?
Zero Trust Security (ZTS) Explained: A Beginner's Guide for 2024
Using Zero Trust security for the hybrid cloud
Zero Trust Security Implementation - Essentials Series - Episode 1
What is Zero Trust Security? (with Palo Alto Networks) | CXOTalk
Комментарии
 0:03:43
0:03:43
 0:07:44
0:07:44
 0:04:38
0:04:38
 0:03:36
0:03:36
 0:04:39
0:04:39
 0:24:00
0:24:00
 0:10:05
0:10:05
 0:17:59
0:17:59
 0:53:12
0:53:12
 0:08:39
0:08:39
 0:07:44
0:07:44
 0:21:05
0:21:05
 0:01:31
0:01:31
 0:21:46
0:21:46
 0:02:12
0:02:12
 0:01:08
0:01:08
 0:04:17
0:04:17
 0:06:14
0:06:14
 0:11:41
0:11:41
 0:02:31
0:02:31
 0:07:38
0:07:38
 0:18:08
0:18:08
 0:08:57
0:08:57
 0:14:52
0:14:52