filmov
tv
Cyber Security Access Models ( DAC, MAC, RBAC and ABAC ) - Arabic

Показать описание
Cyber Security Access Models ( DAC, MAC, RBAC and ABAC ) - Arabic
Cybersecurity and Zero Trust
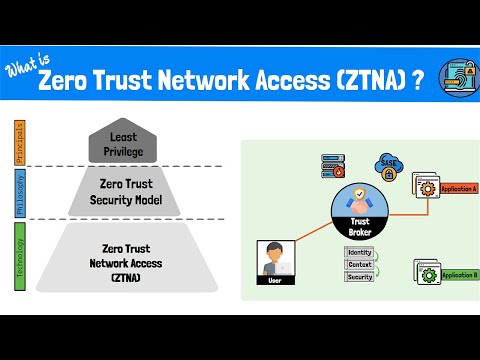
What is Zero Trust Network Access (ZTNA)? The Zero Trust Model, Framework and Technologies Explained
AI in Cybersecurity
Network Security Model
What Is Cyber Security | How It Works? | Cyber Security In 7 Minutes | Cyber Security | Simplilearn
Cybersecurity Architecture: Five Principles to Follow (and One to Avoid)
Foundations of Cybersecurity 4-8: Access Control Models
E49 - Not Another Demo - Grip Security
Access Control Models - CompTIA Security+ SY0-501 - 4.3
Cybersecurity Architecture: Who Are You? Identity and Access Management
Cybersecurity Expert Demonstrates How Hackers Easily Gain Access To Sensitive Information
CertMike Explains The Bell LaPadula Model
Discretionary Access Control
Mandatory Access Control (MAC) Models
Zero Trust Explained in 4 mins
What is an Access Control Cybersecurity Policy?
What is Access Control?
Cyber Security - Video Animation Services
Zero Trust Explained
Cyber Security Interview Questions You Must Know (Part 1)
How to Learn Cyber Security Faster In 5 Simple Steps
What Is Firewall ? | Firewall Explained | Firewalls and Network Security | Simplilearn
Networking For Cybersecurity | What you NEED to know
Комментарии
 0:11:47
0:11:47
 0:17:59
0:17:59
 0:07:44
0:07:44
 0:06:19
0:06:19
 0:11:47
0:11:47
 0:07:07
0:07:07
 0:17:34
0:17:34
 0:09:32
0:09:32
 0:30:00
0:30:00
 0:06:06
0:06:06
 0:31:15
0:31:15
 0:03:27
0:03:27
 0:07:12
0:07:12
 0:01:12
0:01:12
 0:02:35
0:02:35
 0:03:43
0:03:43
 0:03:11
0:03:11
 0:05:21
0:05:21
 0:00:15
0:00:15
 0:02:12
0:02:12
 0:10:47
0:10:47
 0:15:19
0:15:19
 0:05:39
0:05:39
 0:10:40
0:10:40