filmov
tv
Attack and Detection of Shadow Credentials

Показать описание
How to Force a certificate into Active Directory and escalate to complete
Active Directory takeover. I will show how to detect the usage of overpass the hash and detect MSDSKeyCredential linkage to a domain controller computer account. Bonus, I do the entire demo with AV turned on using obfuscated versions of Rubeus and Mimikatz.
-~-~~-~~~-~~-~-
Please watch: "Red Team Tips February 1st: OPSEC Safe Active Directory Enumeration with SilentHound "
-~-~~-~~~-~~-~-
Active Directory takeover. I will show how to detect the usage of overpass the hash and detect MSDSKeyCredential linkage to a domain controller computer account. Bonus, I do the entire demo with AV turned on using obfuscated versions of Rubeus and Mimikatz.
-~-~~-~~~-~~-~-
Please watch: "Red Team Tips February 1st: OPSEC Safe Active Directory Enumeration with SilentHound "
-~-~~-~~~-~~-~-
Attack and Detection of Shadow Credentials
DCShadow attack Analysis and Detection (Mimikatz,Qradar)
Wallarm Demo: Shadow API Detection
Attack and Detection of DFSCoerce and NTLM relaying ADCS attacks.
How to know if your PC is hacked? Suspicious Network Activity 101
Attack Detection Fundamentals: Workshop #1 - Initial Access
Threat Detection with Python as a Security Analyst - Shadow Session w/ IBM SkillsBuild
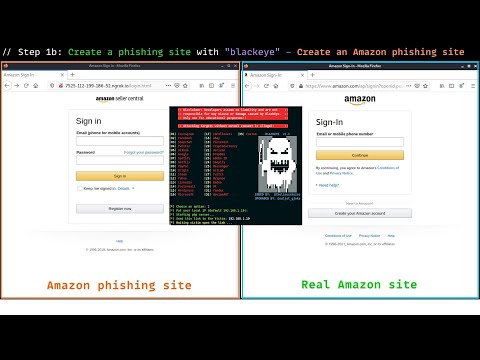
Create a phishing site in 4 minutes?? | Suprisingly easy and convenient
Simple Penetration Testing Tutorial for Beginners!
AI-Based, Real-Time Threat Detection at Scale
+91 9176206235(call/whatsapp) PhD in Cyber Attack Detection In IoT Devices | Attack Source Code Ns2
Harman Singh - Active Directory Threats & Detection
LinkShadow at the forefront of next-gen cybersecurity analysis & threat detection
Disable This Android Privacy Setting ASAP!
Linux EDR Duplicate User Password Hash Attack Detection and Forensics
The Radioactive Nightmare Beneath Chernobyl: The Elephant's Foot #shorts #historyfacts
The Bloop Diet - Gargantuan Leviathan says Hello! #shorts
when you put these on..
This Gets You a Lazy Eye
SentinelOne Demo: SentinelOne VS Dark Power Ransomware - Detection and Response
Authenticator Bypass
Ancient Craft Watching us From Orbit | The Black Knight Satellite
when you dont realize you entered the deadzone
Detecting privilege escalation and exploitation with Intrusion Detection | TryHackMe
Комментарии
 0:14:02
0:14:02
 0:22:12
0:22:12
 0:02:34
0:02:34
 0:22:28
0:22:28
 0:10:19
0:10:19
 1:06:36
1:06:36
 0:58:32
0:58:32
 0:04:06
0:04:06
 0:15:25
0:15:25
 0:02:19
0:02:19
 0:01:59
0:01:59
 0:58:17
0:58:17
 0:09:29
0:09:29
 0:00:29
0:00:29
 0:04:13
0:04:13
 0:00:51
0:00:51
 0:00:26
0:00:26
 0:00:20
0:00:20
 0:00:14
0:00:14
 0:03:48
0:03:48
 0:01:00
0:01:00
 0:21:30
0:21:30
 0:01:40
0:01:40
 0:13:16
0:13:16