filmov
tv
UniFi: How to Securely Configure Switch Port VLAN Traffic Restrictions and Avoid VLAN Hopping

Показать описание
Connecting With Us
---------------------------------------------------
Lawrence Systems Shirts and Swag
---------------------------------------------------
AFFILIATES & REFERRAL LINKS
---------------------------------------------------
Amazon Affiliate Store
UniFi Affiliate Link
All Of Our Affiliates that help us out and can get you discounts!
Gear we use on Kit
Use OfferCode LTSERVICES to get 10% off your order at
Digital Ocean Offer Code
HostiFi UniFi Cloud Hosting Service
Protect you privacy with a VPN from Private Internet Access
Patreon
TImestamps
00:00 - UniFi Changes to Port VLAN Traffic Restrictions
00:48 UniFi Default Port VLAN Settings
03:41 When to use VLAN Traffic Restrictions
04:25 Where to Set The VLAN Traffic Restrictions
#unifi #networking
UniFi: How to Securely Configure Switch Port VLAN Traffic Restrictions and Avoid VLAN Hopping
Configuring VLANs, Firewall Rules, and WiFi Networks - UniFi Network Application
Unifi Network Complete Setup 2024
UniFi Network Setup & Configuration Guide | 2023
5 Security Features in UniFi You Need to Enable (And Why)
UniFi - Recommended settings for IoT devices
Unifi Network Optimization
UniFi Network BEGINNERS Configuration Guide | 2024
Top 13 Unifi Network Setup Tips - Planning and Optimization
Unifi Network Complete Setup 2023
My Full Unifi Network Setup - Firewall Rules, VLANs, WiFi, and more
Securing Your Unifi Network
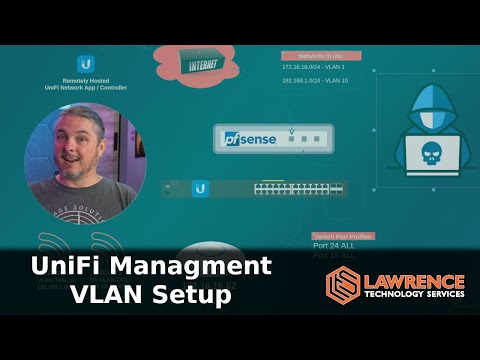
UniFi Management VLAN & Network Security
Configure VLANs on Unifi Switches
UniFi Network • Installation and configuration tutorial
Secure IoT Network Configuration
How Secure is your IOT Network configuration? Make it secure with UniFi in 4 simple steps
Unifi for Beginners - How it Works and The Reasons for its Success
Ubiquiti UniFi Switch Port Security
Secure your network - How to Setup OpenVPN Server on UniFi Dream Machine Pro
Unifi Security Gateway - First Time Setup
Part 2 | Ultimate Home Network 2021 | VLANs, Firewall Rules, and WiFi Networks for IoT UniFi 6.0
Unifi for Newbies - Securing with Firewall Rules
UniFi secure IoT network setup with Google Cast and AirPlay support
Комментарии
 0:09:13
0:09:13
 0:30:39
0:30:39
 0:43:19
0:43:19
 0:38:31
0:38:31
 0:09:11
0:09:11
 0:07:15
0:07:15
 0:08:10
0:08:10
 0:46:14
0:46:14
 0:40:02
0:40:02
 0:47:17
0:47:17
 0:26:52
0:26:52
 0:11:26
0:11:26
 0:10:13
0:10:13
 0:20:13
0:20:13
 0:19:31
0:19:31
 0:34:30
0:34:30
 0:21:27
0:21:27
 0:08:55
0:08:55
 0:09:03
0:09:03
 0:11:19
0:11:19
 0:17:35
0:17:35
 0:33:21
0:33:21
 1:14:26
1:14:26
 0:06:00
0:06:00