filmov
tv
What Is Active Directory Authentication? Basics, Management, Handling Shortcomings, & More
Показать описание
Resources and social media:
#jumpcloud #activedirectory #devicemanagement #kerberos #ldap
Transcription:
AD authentication is a system in Windows that checks if users, devices, and services are allowed to access the Active Directory network. It helps IT teams easily manage users and permissions, and it also lets them control devices and user settings with a feature called AD Group Policy.
AD authentication lets users sign in just once, and then access different parts of the company's network without having to sign in again. This is called single sign-on, or, SSO.
Before AD authentication, there were other systems called LAN Manager, or, “LM,” and NT LAN Manager, or, “NTLM,” but they used weak methods to protect information, making them vulnerable to cyber attacks. AD authentication was created to fix these issues, replacing LM and NTLM in the Windows 2000 operating system.
AD authentication uses two standards: Kerberos, and Lightweight Directory Access Protocol, or “LDAP”.
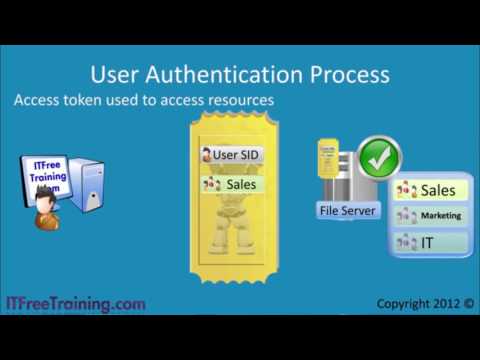
With Kerberos-based AD authentication, you only need to log in once to access multiple things on the network. Instead of sending your login details over the network, which was risky with older methods, Kerberos creates a special key just for you. This key lasts for a certain length of time, and while it’s active, you won’t have to keep re-entering your password. Kerberos also makes sure you only access things you're allowed to by creating a "token" with all the permissions and rights for your account.
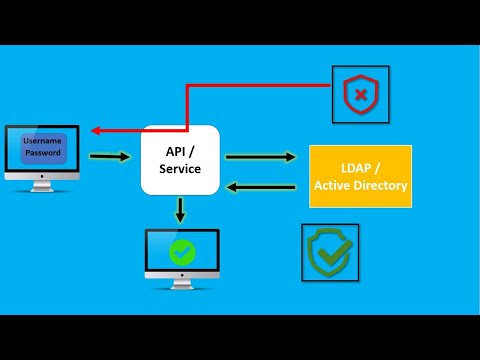
The second AD authentication standard is LDAP, which has two main options: simple authentication, and simple authentication and security layer, or, “SASL.”
In simple authentication, you simply use your login details to connect to the server. SASL, on the other hand, allows IT teams to create a more secure login process by layering on other authentication requirements like Kerberos to connect to the server. SASL improves security, because it separates the way you prove yourself from the actual applications you're using.
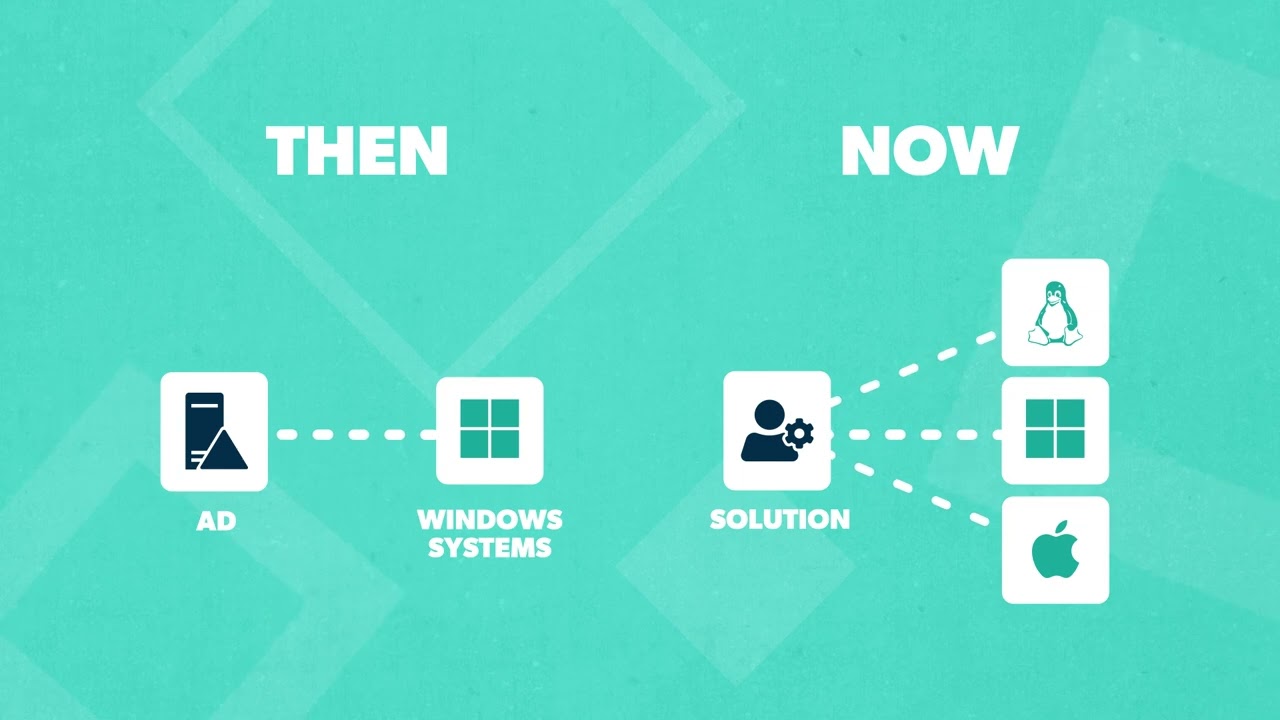
While AD was designed for Windows systems and devices, in today’s IT environment, admins often have to create solutions for managing different operating systems, like Linux and Mac, too. Luckily, there are solutions to manage these newer systems.
For Linux, there are two ways to connect to Active Directory: LDAP, and Samba.
To use LDAP on Linux, admins have to reconfigure the device to access the pluggable authentication module, also called PAM. Since AD focuses on Kerberos, IT teams using LDAP for Linux devices have to manually handle the whole authentication process.
The other option is Samba, a tool that helps Linux systems work well with Windows. IT teams can use Samba as a middleman to enable AD authentication on Linux computers. This connection allows them to create domains, set up a shared printer server, and configure PAM so that users can log in and use local services.
For Mac devices, you can connect to Active Directory using an LDAP and AD connector. These tools help configure Macs so that users can access their basic account information from the AD infrastructure so they can get to company resources from their device. The AD connector can also link AD authentication with roles in the Mac's access management system.
The AD connector takes care of all the things needed to prove that a macOS device is allowed to use the AD infrastructure. But here's the catch: Macs running macOS 10.12 or later can't join an AD domain unless the domain has at least Windows 2008. To make AD work on those Macs, IT teams have to use weaker security measures, which is risky for the organization's safety.
Since AD was developed to focus on Windows, combining it with other OSes and cloud-based systems is not very efficient. Instead of having one central system for authentication and authorization, organizations end up with many smaller systems, which makes things more complex and time-consuming for IT admins to manage. And when onboarding new users in a cloud-first environment, this process becomes even more complex, and often requires the involvement of multiple departments.
 0:05:19
0:05:19
 0:03:46
0:03:46
 0:04:33
0:04:33
 0:15:25
0:15:25
 0:01:12
0:01:12
 0:04:48
0:04:48
 0:14:19
0:14:19
 0:11:17
0:11:17
 0:06:48
0:06:48
 0:03:24
0:03:24
 0:30:57
0:30:57
 0:11:41
0:11:41
 0:06:19
0:06:19
 0:24:02
0:24:02
 0:08:18
0:08:18
 0:14:14
0:14:14
 0:06:02
0:06:02
 0:01:51
0:01:51
 0:04:13
0:04:13
 0:02:24
0:02:24
 0:31:54
0:31:54
 0:12:30
0:12:30
 0:35:44
0:35:44
 0:17:27
0:17:27