filmov
tv
Unix system calls (1/2)

Показать описание
Unix system calls (1/2)
System Calls
Unix system calls 1 our of 2
Unix system calls (2/2)
System Calls | Read | Write | Open | Close | Linux
QEEE Lecture 2- UNIX system calls
Linux Tutorial: How a Linux System Call Works
fork() and exec() System Calls
LINUX Administration + AWS tutorials || Demo - 1 || by Mr. Shakeel On 25-11-2024 @7AM IST
Learn Unix / Linux System calls - Write ()
Learn Unix/ Linux System Calls - Open ()
Introduction to Unix system calls
Learn Unix/Linux System Calls - Creat ()
Unix System Calls Introduction
Implement UNIX system calls like ps, fork, join, exec family, and wait for process management SPOS
Operating systems Example 1.002 GATE CS 2012 (fork system call)
Syscalls, Kernel vs. User Mode and Linux Kernel Source Code - bin 0x09
Linux/ Unix Tutorial || System calls in Linux OS by Shiva
Operating System Services, System Calls and OS Structure
8 - Unix System Call Linux Part 1
L-1.7: System Calls in Operating system and its types in Hindi
4. Open(),Read(),Write(),Close() System calls in Unix Terminal #unix #linux
Types of System Calls
L-1.8: Fork System call with Example | Fork() system call questions
Комментарии
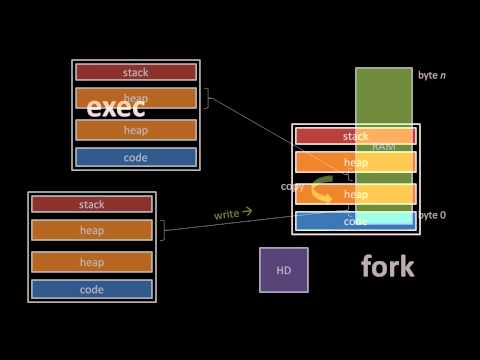 0:45:16
0:45:16
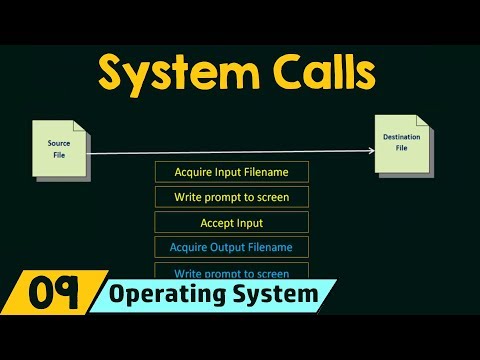 0:12:39
0:12:39
 0:45:16
0:45:16
 0:51:18
0:51:18
 0:09:30
0:09:30
 1:01:59
1:01:59
 0:02:31
0:02:31
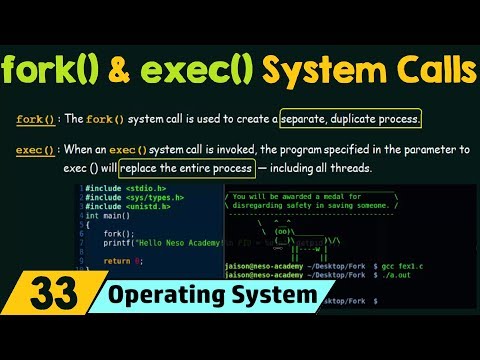 0:20:34
0:20:34
 0:47:31
0:47:31
 0:02:45
0:02:45
 0:03:36
0:03:36
 1:36:00
1:36:00
 0:07:42
0:07:42
 0:01:52
0:01:52
 0:03:27
0:03:27
 0:03:52
0:03:52
 0:13:24
0:13:24
 0:19:47
0:19:47
 0:12:54
0:12:54
 0:42:45
0:42:45
 0:10:07
0:10:07
 0:10:04
0:10:04
 0:11:23
0:11:23
 0:10:02
0:10:02