filmov
tv
Syscalls, Kernel vs. User Mode and Linux Kernel Source Code - bin 0x09

Показать описание
We will have a look at what syscalls are and what it has to do with the kernel mode an user mode. We do this by exploring a kernel function and trace it down to the assembler level.
-=[ ❤️ Support ]=-
-=[ 🐕 Social ]=-
-=[ ❤️ Support ]=-
-=[ 🐕 Social ]=-
Syscalls, Kernel vs. User Mode and Linux Kernel Source Code - bin 0x09
Linux Tutorial: How a Linux System Call Works
System Calls
Operating Systems; Kernel Mode and User Mode
User mode vs Kernel Mode
What is a Kernel?
User Mode vs Kernel Mode
what is kernel in operating system ? #shorts #bydubebox #kernel
User mode vs Kernel mode in operating system
L-1.10: User mode and Kernel mode in operating system in hindi
1.4 User Mode Vs Kernel Mode
what is kernel space and user space ? #shorts #linux #kernel #bydubebox
Linux Kernel, System Calls and Modules - Linux Basics In 5 Minutes
How system call works ? #shorts #linux #os #internals #bydubebox
what is system call in operating system? #shorts #linux #kernel #bydubebox
Operating System Concepts: System Calls and Type of System Calls, Context Switch
GWU OS: System Architecture -- System Calls
Kernel vs User Level Threads
user mode Vs kernel mode : 3 differences Explained diagramatically.
System Calls Going from User to OS Code
Unix & Linux: Linux Kernel Mode Vs User Mode
Linux Internals - SysCalls
What is a Kernel| Shell in operating system | System calls in operating system| User & Kernel mo...
When you first time install Kali linux for hacking 😄😄 #hacker #shorts
Комментарии
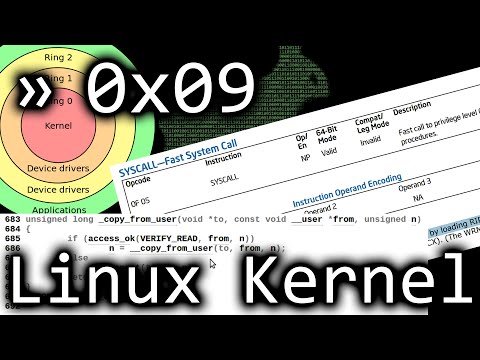 0:13:24
0:13:24
 0:02:31
0:02:31
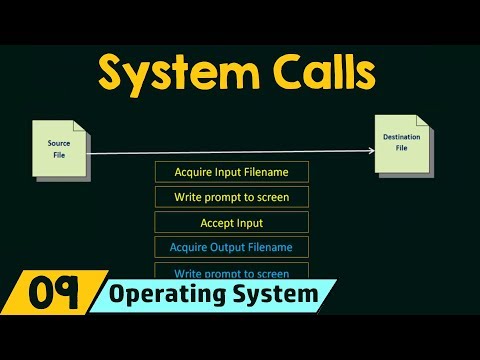 0:12:39
0:12:39
 0:03:50
0:03:50
 0:03:42
0:03:42
 0:05:38
0:05:38
 0:03:46
0:03:46
 0:00:16
0:00:16
 0:03:35
0:03:35
 0:06:46
0:06:46
 0:07:05
0:07:05
 0:00:33
0:00:33
 0:05:35
0:05:35
 0:00:30
0:00:30
 0:00:27
0:00:27
 0:24:40
0:24:40
 0:57:47
0:57:47
 0:01:30
0:01:30
 0:04:19
0:04:19
 0:02:46
0:02:46
 0:01:34
0:01:34
 0:21:21
0:21:21
 0:05:42
0:05:42
 0:00:32
0:00:32