filmov
tv
Trying out some Deadly Linux Commands part 1

Показать описание
There are a selection of Terminal Commands in Linux that we're told are Deadly to run, but just how lethal are they? In this video I try out a selection of them in VirtualBox with Ubuntu 15.10.
0:20 Fork Bomb
1:47 rm -rf /
2:17 Disguised rm -rf /
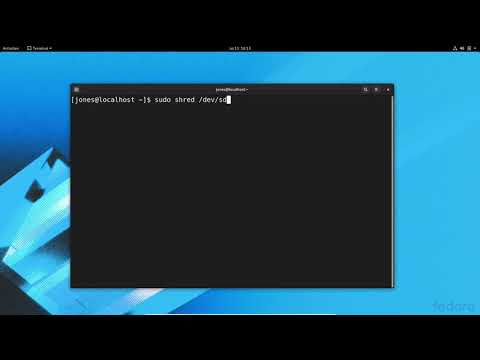
3:14 dd if=/dev/random of=/dev/sda
4:04 mv / /dev/null
4:28 rm -f /usr/bin/sudo;rm -f /bin/su
0:20 Fork Bomb
1:47 rm -rf /
2:17 Disguised rm -rf /
3:14 dd if=/dev/random of=/dev/sda
4:04 mv / /dev/null
4:28 rm -f /usr/bin/sudo;rm -f /bin/su
Trying out some Deadly Linux Commands part 1
Trying out Deadly Linux Commands part 2
Why don't more people use Linux?
I Forced Myself to Use Linux For ANOTHER 30 Days (Linux Challenge Part 2)
Hacking Linux with These Simple Commands Pt:1
When you first time install Kali linux for hacking 😄😄 #hacker #shorts
I forced EVERYONE to use Linux
So, I Tried Arch Linux.. (and Hyprland btw)
MX Linux - Xfce - More Fun with SSH.
Deadly Linux Terminal Commands part 3
100+ Linux Things you Need to Know
Microsoft's attempt at destroying Linux
NEVER USE THESE LINUX COMMANDS! | Dangerous Linux Commands | Deadly Linux Commands
Top 10 Dangerous Linux Commands - (Educational Purpose)
Most dangerous command ❌❌ #shorts #tech #coding #programming #funny #terminal #linux #command
Trying Linux For The First Time.. I LOVED IT! | Windows User Perspective
The most dangerous #linux command - rm #shorts #coding
Hacking Linux Without root by Running a Deadly Command
Never Use These LINUX Commands! | Dangerous LINUX Commands |
This Year in Linux, the Top Linux News of 2024
Never use this command 😱 #shorts #linux #kalilinux #android #iphone
Arch Linux Experience - Hyprland
Deadly Linux Commands: shred /dev/sda
what Linux Distro are you using??
Комментарии
 0:06:03
0:06:03
 0:06:21
0:06:21
 0:01:00
0:01:00
 0:30:49
0:30:49
 0:00:56
0:00:56
 0:00:32
0:00:32
 0:22:59
0:22:59
 0:36:10
0:36:10
 0:44:30
0:44:30
 0:06:22
0:06:22
 0:12:23
0:12:23
 0:20:51
0:20:51
 0:01:05
0:01:05
 0:02:33
0:02:33
 0:00:20
0:00:20
 0:09:35
0:09:35
 0:00:28
0:00:28
 0:05:45
0:05:45
 0:00:57
0:00:57
 0:29:26
0:29:26
 0:01:00
0:01:00
 0:39:02
0:39:02
 0:00:28
0:00:28
 0:00:45
0:00:45