filmov
tv
How to remotely control a target/webserver reverse shell hacking

Показать описание
#####
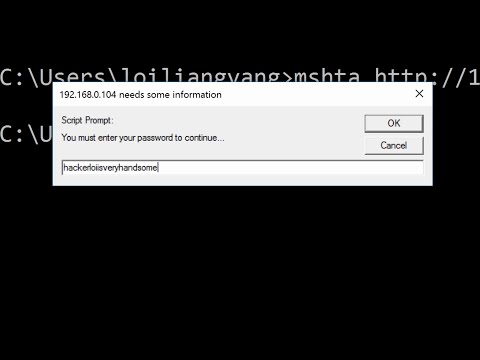
The filter in this task is a client-side filter
#####
In this video, we will explore how to bypass website filters to upload a file and gain access to a target system. Using the Gobuster tool, we will enumerate the target to brute-force URIs including directories and files as well as DNS subdomains. We will then deploy a PHP Monkey reverse shell script to create a backdoor that allows us to remotely access and control the target system. To ensure our success, we will use Netcap to monitor and listen for incoming traffic on our own machine. Join us to learn about these powerful tools and techniques in ethical hacking and cybersecurity.
Check out my favorite course and certificate about Practical DevSecOps.
The filter in this task is a client-side filter
#####
In this video, we will explore how to bypass website filters to upload a file and gain access to a target system. Using the Gobuster tool, we will enumerate the target to brute-force URIs including directories and files as well as DNS subdomains. We will then deploy a PHP Monkey reverse shell script to create a backdoor that allows us to remotely access and control the target system. To ensure our success, we will use Netcap to monitor and listen for incoming traffic on our own machine. Join us to learn about these powerful tools and techniques in ethical hacking and cybersecurity.
Check out my favorite course and certificate about Practical DevSecOps.
How to remotely control another Android phone? 📱🔧 Check out this video tutorial to learn! 🎥👀...
Remotely Control iPad from iPhone
Remotely Control Android from Another Android
How To Remotely Access Another Mac …The EASY Way!
How to Remotely Control Your Computer Using Any Device (access your desktop from anywhere)
How to control your android phone remotely
Remotely Control Any PC with an image?!
How to control iPhone remotely from Windows, macOS or Android
How to Control Your Phone Remotely by Using Airdroid App?
Quick Fix: How to remotely access another computer
How Hackers Remotely Control Any PC?!
How to Access any Computer Remotely | How to Control any Laptop in another Laptop | Remote Desktop
How to remotely control a Windows PC with a phone for free!
How to Start Your Car Remotely with Your Original Car Key #howto #remote #start
How to Remotely Control Someone's Screen on Zoom in 2024
Remotely Control Any PC // Kali Linux Tutorial
watch how Hackers Remotely Control Any phone?! protect your phone from hackers now!
Remotely Control Any PC With This Simple Tool!
Remotely Control Any PC in 4 mins 59 seconds
AnyDesk Tutorial: Remotely Access Your Computer with Ease
How to Remotely Control your RØDECaster Video with WiFi
This is the remote control of the universe
How to Remote Control a Computer Remotely Free and Easily with LogMeIn
Remotely access a smartphone from another phone or laptop, | access files| full control easy .
Комментарии
 0:01:28
0:01:28
 0:00:27
0:00:27
 0:02:26
0:02:26
 0:03:47
0:03:47
 0:07:06
0:07:06
 0:03:02
0:03:02
 0:12:42
0:12:42
 0:04:11
0:04:11
 0:01:14
0:01:14
 0:02:31
0:02:31
 0:09:47
0:09:47
 0:03:46
0:03:46
 0:00:34
0:00:34
 0:00:28
0:00:28
 0:02:28
0:02:28
 0:08:06
0:08:06
 0:10:11
0:10:11
 0:04:44
0:04:44
 0:04:59
0:04:59
 0:01:14
0:01:14
 0:00:32
0:00:32
 0:00:48
0:00:48
 0:09:36
0:09:36
 0:13:26
0:13:26