filmov
tv
Zero Trust Security and Identity Management with Boundary

Показать описание
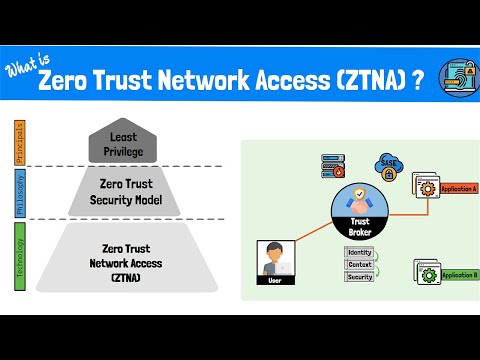
Modern systems and applications are built around resources that require frequent access by users who may be a developer, DevOps engineer, SRE, or sysadmin in the public domain. These resources often reside in private networks that are inaccessible from an outside network. Traditional approaches such as VPNs, bastion hosts, and gateway nodes are often chosen to bridge connections between private and public networks, but these are complex and expensive to setup. Further, individual credentials for each resource (DB credentials, SSH keys, etc.) need to be shared with users. This is not a recommended practice in software development and may result in security breach.
In this context, I will be discussing about the open source tool HashiCorp Boundary, which aims to abstract away much of the complexity by providing a linear approach in granting and maintaining access to infrastructure resources.
Speaker: Suman Chakraborty
GitHub: @suchakra012
Twitter: @itsmesumanc
#Boundary #Multi-cloud #ZeroTrustSecurity
HashiCorp provides infrastructure automation software for multi-cloud environments, enabling enterprises to unlock a common cloud operating model to provision, secure, connect, and run any application on any infrastructure. HashiCorp open source tools Vagrant, Packer, Terraform, Vault, Consul, Nomad, Boundary, and Waypoint allow organizations to deliver applications faster by helping enterprises transition from manual processes and ITIL practices to self-service automation and DevOps practices.
Twitter: @hashicorp
In this context, I will be discussing about the open source tool HashiCorp Boundary, which aims to abstract away much of the complexity by providing a linear approach in granting and maintaining access to infrastructure resources.
Speaker: Suman Chakraborty
GitHub: @suchakra012
Twitter: @itsmesumanc
#Boundary #Multi-cloud #ZeroTrustSecurity
HashiCorp provides infrastructure automation software for multi-cloud environments, enabling enterprises to unlock a common cloud operating model to provision, secure, connect, and run any application on any infrastructure. HashiCorp open source tools Vagrant, Packer, Terraform, Vault, Consul, Nomad, Boundary, and Waypoint allow organizations to deliver applications faster by helping enterprises transition from manual processes and ITIL practices to self-service automation and DevOps practices.
Twitter: @hashicorp
 0:03:43
0:03:43
 0:07:44
0:07:44
 0:17:59
0:17:59
 0:28:38
0:28:38
 0:04:51
0:04:51
 0:05:06
0:05:06
 0:47:22
0:47:22
 0:08:32
0:08:32
 0:17:07
0:17:07
 0:45:14
0:45:14
 0:02:35
0:02:35
 0:01:38
0:01:38
 0:12:25
0:12:25
 1:02:52
1:02:52
 0:36:36
0:36:36
 0:02:37
0:02:37
 0:02:48
0:02:48
 0:57:11
0:57:11
 0:44:18
0:44:18
 0:08:36
0:08:36
 0:09:34
0:09:34
 0:01:31
0:01:31
 0:48:00
0:48:00
 0:05:35
0:05:35