filmov
tv
OAuth 2.0 - a dead simple explanation

Показать описание
00:00 What is OAuth 2.0?
00:13 What problem does OAuth 2.0 solve?
02:04 OAuth 2.0 Client Registration
03:06 OAuth 2.0 Confidential vs. public clients
04:21 OAuth 2.0 Authorization Code Grant
06:43 OAuth 2.0 Access and Refresh Tokens and JWTs
08:03 OAuth 2.0 Grant types: client credentials grant, implicit grant, resource owner password grant, device grant
09:03 Outro
OAuth 2.0 is an "authorization framework [that] allows third party applications to get limited access to an HTTP service" (RFC 6749).
OAuth 2.0 is all about giving third party applications limited access to APIs. Prior to OAuth 2.0, the third party would have asked for the user's credentials and would have used these credentials on the respective API. OAuth 2.0 eliminates the need for password sharing by introducing a new entity called the OAuth 2.0 authorization server.
The OAuth 2.0 authorization server issues access and refresh tokens to third party applications thereby eliminating the need of credential sharing. The third party application is called the client in OAuth terminology. The API the third party wants to get access to is called the resource server or the protected resource.
Before a third party can get limited access to an API, it first needs to register itself with the OAuth 2.0 Authorization server. The third party application, the so called client, gets a client id upon registration with the OAuth 2.0 authorization server. If the client can keep data secret, then it will also obtain client credentials. The simplest form of a client credential would be a shared secret called the client secret. OAuth 2.0 also supports more sophisticated means auf authenticating against the OAuth 2.0 authorization server such as mutual TLS (mTLS).
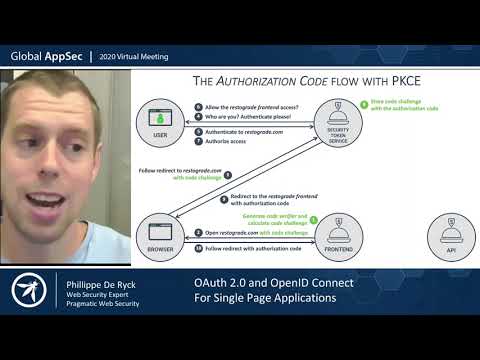
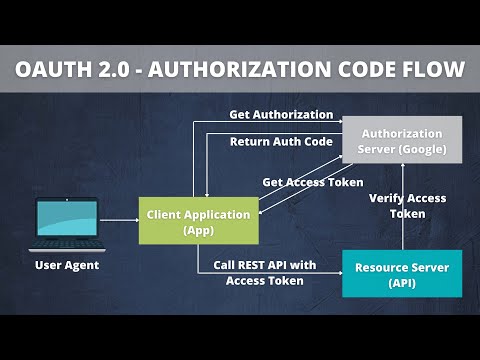
Once the client is registered, the client performs one of the OAuth flows that are also known as grant types. The most popular grant types are the OAuth 2.0 authorization code grant which orchestrates an approval flow between the resource owner, the OAuth 2.0 authorization server and the protected resource.
Contrast this with the client credentials grant which is made for machine-to-machine communication. The resource owner password grant and the implicit grant are insecure according to the OAuth 2.0 Security best current practices and must not be used. Then there is also the OAuth 2.0 device grant which is built for devices that do not have a browser or where entering credentials is cumbersome such as Smart TVs.
While the OAuth 2.0 RFC does not mandate the access and refresh tokens to be structured, in most deployments they are actually JSON Web Tokens (JWTs). This has the advantage that the protected resource can validate the signature of the token locally without having to make a REST call to the authorization server to check for the validity of the token.
Комментарии
 0:04:32
0:04:32
 0:09:16
0:09:16
 0:10:03
0:10:03
 1:02:17
1:02:17
 0:36:53
0:36:53
![[2023] OAuth 2](https://i.ytimg.com/vi/fIQ-wy-RvOk/hqdefault.jpg) 0:14:37
0:14:37
 0:19:56
0:19:56
 0:09:21
0:09:21
 2:43:46
2:43:46
 0:10:18
0:10:18
 0:57:18
0:57:18
 0:54:27
0:54:27
 0:09:52
0:09:52
 0:03:04
0:03:04
 1:34:24
1:34:24
 0:00:55
0:00:55
 0:17:18
0:17:18
 0:08:47
0:08:47
 0:08:07
0:08:07
 0:17:13
0:17:13
 0:11:49
0:11:49
 0:22:30
0:22:30
 0:02:16
0:02:16
 1:02:48
1:02:48