filmov
tv
OAuth 2 0 and OpenID Connect for Single Page Applications Philippe De Ryck

Показать описание
-
Managed by the OWASP® Foundation
Managed by the OWASP® Foundation
An Illustrated Guide to OAuth and OpenID Connect
OAuth 2.0 and OpenID Connect (in plain English)
OAuth 2.0 & OpenID Connect (OIDC): Technical Overview
Introduction to OAuth 2.0 and OpenID Connect By Philippe De Ryck
OAuth 2.0 explained with examples
OAuth 2 0 and OpenID Connect for Single Page Applications Philippe De Ryck
Что такое OAuth 2.0 и OpenID Connect за 15 минут
What is OAuth 2.0 and OpenID Connect?
OpenID Connect vs OAuth | OpenID Connect explained
Introduction to OAuth 2.0 and OpenID Connect • Philippe De Ryck • GOTO 2018
How To Secure Applications Using OpenID Connect and OAuth 2.0
ID Tokens VS Access Tokens: What's the Difference?
OAuth 2.0 Explained - Authentication Example using OpenID, JWT and Opaque Tokens
Learn OAuth2.0 & OpenID Connect in Under 20 minutes
OAuth 2.0: An Overview
Как работает OAuth 2 - введение (просто и понятно)
OAuth and OpenID Connect - Know the Difference
Oauth2.0 and OpenID Connect with F5 APM - Part 1
Everything You Ever Wanted to Know About OAuth and OIDC
SAML Vs OAuth Vs Openid Differences and Application
SAML vs. OpenID (OIDC): What's the Difference?
SSO: SAML vs OAUTH vs OIDC
oAuth for Beginners - How oauth authentication🔒 works ?
Profiling OAuth 2 0 and OpenID Connect for Enterprise Use - OSW 2020
Комментарии
 0:16:36
0:16:36
 1:02:17
1:02:17
 0:16:19
0:16:19
 2:43:46
2:43:46
 0:10:03
0:10:03
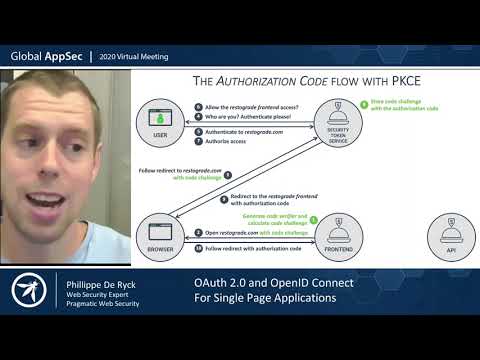 0:36:53
0:36:53
 0:14:27
0:14:27
 0:08:39
0:08:39
 0:08:50
0:08:50
 0:47:18
0:47:18
 0:30:33
0:30:33
 0:08:38
0:08:38
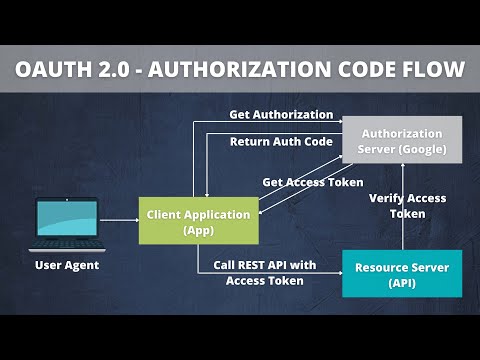 0:09:52
0:09:52
 0:17:12
0:17:12
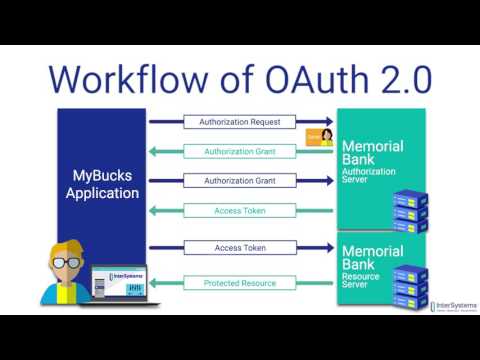 0:06:34
0:06:34
 0:05:07
0:05:07
 0:10:18
0:10:18
 0:17:32
0:17:32
 0:33:21
0:33:21
 0:07:40
0:07:40
 0:02:49
0:02:49
 0:06:24
0:06:24
 0:10:43
0:10:43
 0:20:35
0:20:35