filmov
tv
Zero Trust Architecture – Applying ZTA in Today’s Environment

Показать описание
In the wake of the massive breach of computer systems of multiple government agencies discovered in December 2020, the US Federal Government is recommending that a Zero Trust security model be considered for all critical networks. As part of this major push to promote ZT adoption, DISA, NIST, and NSA are releasing specific guidelines. But is Zero Trust just a new marketing buzzword, a simple iteration over the well-known 'least privilege ' mindset, or a truly innovative strategy? Is Zero Trust truly attainable? If so, how do you get started and what are some of the tools and technologies that are available to implement it?
To answer these questions, join SANS instructors Ismael Valenzuela and Justin Henderson, co-authors of Security 530: Defensible Security Architecture and Engineering, as they provide their experience and provide specific advice on how to implement Zero Trust strategies.
#BlueTeamSummit #ZeroTrustArchitecture
To answer these questions, join SANS instructors Ismael Valenzuela and Justin Henderson, co-authors of Security 530: Defensible Security Architecture and Engineering, as they provide their experience and provide specific advice on how to implement Zero Trust strategies.
#BlueTeamSummit #ZeroTrustArchitecture
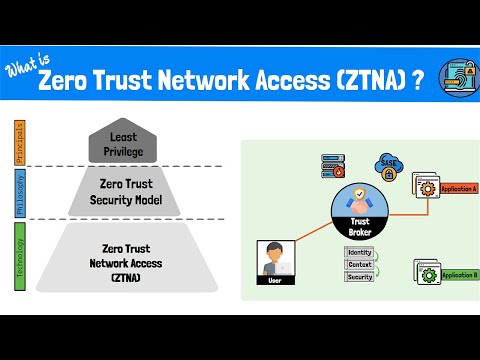
What is Zero Trust Network Access (ZTNA)? The Zero Trust Model, Framework and Technologies Explained
Zero Trust Explained in 4 mins
Zero Trust Architecture – Applying ZTA in Today’s Environment
Zero Trust Authentication and Architecture within NIST 800-207 Framework
Application architecture is simple if you don't suck at Zero-Trust Ep:3
Zero Trust Architecture Explained
How to design and setup a Zero-Trust Cloud Security Architecture?
Approaches to Applying Zero-Trust Architecture #shorts
The Future of API Security | Episode 3
What is Zero Trust Architecture?
Approaches to Applying Zero-Trust Architecture (NIST Insights) NextLabs Cybersecurity Expert Series
A Simplified and Practical Approach to Pursuing a Zero Trust Architecture
Zero Trust Series, part 4: How to implement zero trust cloud architecture
Applying Zero Trust Architecture for Secure Video Conferencing- Pexip
AWS re:Inforce 2023 - Steps toward a Zero Trust architecture on AWS (IAM307)
Zero Trust Overview (part 1)
Zero Trust - CompTIA Security+ SY0-701 - 1.2
What is Zero Trust Architecture?
Overview of Zero Trust Architectures
Zero Trust and Security Architecture
Cybersecurity Zero Trust Architecture : Explained For Beginners
Inside the Making of a Zero Trust Architecture
Implementing Zero Trust Architecture: A Step-by-Step Guide Part 1
How to apply a zero trust model for your deployments using Anthos
Комментарии
 0:07:44
0:07:44
 0:03:43
0:03:43
 0:52:23
0:52:23
 0:10:28
0:10:28
 0:16:30
0:16:30
 0:13:55
0:13:55
 0:04:01
0:04:01
 0:00:59
0:00:59
 0:13:36
0:13:36
 0:00:13
0:00:13
 0:06:16
0:06:16
 0:27:03
0:27:03
 0:02:37
0:02:37
 0:29:46
0:29:46
 0:54:38
0:54:38
 0:18:11
0:18:11
 0:10:05
0:10:05
 0:00:35
0:00:35
 0:45:42
0:45:42
 0:01:24
0:01:24
 0:32:47
0:32:47
 0:50:13
0:50:13
 0:37:45
0:37:45
 0:05:35
0:05:35