filmov
tv
Microsoft Defender course/training: Learn how to use Microsoft Defender

Показать описание
Watch this video to learn information on how to use and manage Microsoft Defender
CONCEPTS COVERERED IN THIS VIDEO:
Microsoft 365 Defender as an Extended Detection and Response (XDR)
*Visualizing the concepts of extended detection and responses (XDR)
*Configuring the Microsoft 365 Defender simulation lab
*Performing an attack using the simulation lab
*Microsoft 365 Defender incidents and automated investigations
*Microsoft 365 Defender action and submissions
*Using Kusto Query Language (KQL) for threat identification
*Microsoft Secure Score
*Microsoft 365 Defender threat analytics
*Custom detections and alerts
Getting started w/ Defender for Cloud,Defender for Servers & Defender for DevOps
*Introduction to Microsoft Defender for Cloud
*Regulatory compliance policies along with MCSB
*Remediations with secure score in Microsoft Defender for Cloud
*Microsoft Defender for Servers
*Microsoft Defender for DevOps
*Microsoft Defender External Attack Surface Management (EASM)
Basic concepts of the Microsoft Defender Suite and Services
*The Microsoft 365 Defender Suite
*Using the Defender and Purview admin centers
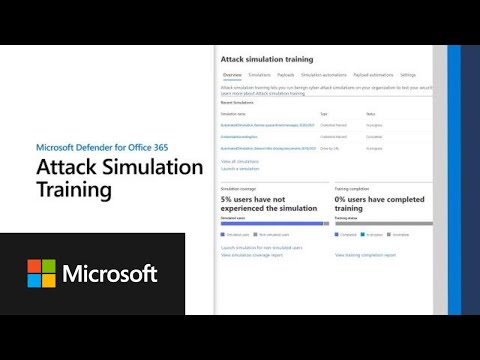
Microsoft Defender for Office 365
*What is Microsoft Defender for Office 365?
*Implementing policies for uses in Email, SharePoint, OneDrive, and Teams
*Dealing with threats using Defender for Office 365
*Performing a campaign email attack simulation in Microsoft Defender
Microsoft Defender for Cloud Apps and Data Loss Prevention (DLP)
*Understanding the concepts of Microsoft Defender for Cloud Apps
*Investigating security risks in Defender for Cloud Apps
*Concepts of data loss prevention in Microsoft Defender
*Alerts with data loss prevention policies (DLP)
*Data loss prevention (DLP) policy alert investigation
Microsoft Defender for Endpoint and Defender Vulnerability Management
*Understanding Microsoft Defender for Endpoint concepts
*Deploy a Windows 11 VM endpoint
*Attack surface reduction (ASR) support with Intune
*Working with device onboarding regarding Defender for Endpoint
*Something to be aware of about extra features
*Endpoint advanced features, alerts and incidents
*Endpoint vulnerabilities
*Device attack surface reduction (ASR)
*Device groups with Defender for Endpoint
*Microsoft Defender Vulnerability Management risk identification
*Endpoint threat indicators
*Device discovery of unmanaged devices
Microsoft Defender for Identity
*Microsoft Entra ID security risk mitigation
*Concepts of using Microsoft Entra Identity Protection
*Microsoft Entra Identity Protection security risk mitigation
*Microsoft Entra Identity Protection risks in regards to Microsoft Defender
*Microsoft Defender for Identity concepts
*Using Defender for Identity to mitigate threats with AD DS
Microsoft Defender for Cloud full management and configurations
*Settings config in Microsoft Defender for Cloud
*Roles in Microsoft Defender for Cloud
*Cloud workload protection
*Automation of onboarding Azure resource
*Azure Arc connections
*Multi-cloud connections
*Email notifications in Microsoft Defender for Cloud
*Using alert suppression rules
*Workflow automation configuration in Defender for Cloud
*Using sample alerts and incidents
*Using Microsoft Defender for Cloud recommendations
*Security alerts and incidents in Microsoft Defender for Cloud
*Using threat intelligence reports with Microsoft Defender for Cloud
Dealing with insider risks in Microsoft 365
*Concepts of insider risk policies
*Insider risk policy generation
*Insider risk policy alert investigation
Audit and search capabilities in Microsoft Defender and Microsoft Purview
*Licensing of unified audit logging
*Permissions for unified auditing
*Threat hunting with unified audit logging
*Threat hunting with Content Searches
Conclusion
*Cleaning up your lab environment
*Getting a Udemy certificate
*BONUS Where do I go from here?
CONCEPTS COVERERED IN THIS VIDEO:
Microsoft 365 Defender as an Extended Detection and Response (XDR)
*Visualizing the concepts of extended detection and responses (XDR)
*Configuring the Microsoft 365 Defender simulation lab
*Performing an attack using the simulation lab
*Microsoft 365 Defender incidents and automated investigations
*Microsoft 365 Defender action and submissions
*Using Kusto Query Language (KQL) for threat identification
*Microsoft Secure Score
*Microsoft 365 Defender threat analytics
*Custom detections and alerts
Getting started w/ Defender for Cloud,Defender for Servers & Defender for DevOps
*Introduction to Microsoft Defender for Cloud
*Regulatory compliance policies along with MCSB
*Remediations with secure score in Microsoft Defender for Cloud
*Microsoft Defender for Servers
*Microsoft Defender for DevOps
*Microsoft Defender External Attack Surface Management (EASM)
Basic concepts of the Microsoft Defender Suite and Services
*The Microsoft 365 Defender Suite
*Using the Defender and Purview admin centers
Microsoft Defender for Office 365
*What is Microsoft Defender for Office 365?
*Implementing policies for uses in Email, SharePoint, OneDrive, and Teams
*Dealing with threats using Defender for Office 365
*Performing a campaign email attack simulation in Microsoft Defender
Microsoft Defender for Cloud Apps and Data Loss Prevention (DLP)
*Understanding the concepts of Microsoft Defender for Cloud Apps
*Investigating security risks in Defender for Cloud Apps
*Concepts of data loss prevention in Microsoft Defender
*Alerts with data loss prevention policies (DLP)
*Data loss prevention (DLP) policy alert investigation
Microsoft Defender for Endpoint and Defender Vulnerability Management
*Understanding Microsoft Defender for Endpoint concepts
*Deploy a Windows 11 VM endpoint
*Attack surface reduction (ASR) support with Intune
*Working with device onboarding regarding Defender for Endpoint
*Something to be aware of about extra features
*Endpoint advanced features, alerts and incidents
*Endpoint vulnerabilities
*Device attack surface reduction (ASR)
*Device groups with Defender for Endpoint
*Microsoft Defender Vulnerability Management risk identification
*Endpoint threat indicators
*Device discovery of unmanaged devices
Microsoft Defender for Identity
*Microsoft Entra ID security risk mitigation
*Concepts of using Microsoft Entra Identity Protection
*Microsoft Entra Identity Protection security risk mitigation
*Microsoft Entra Identity Protection risks in regards to Microsoft Defender
*Microsoft Defender for Identity concepts
*Using Defender for Identity to mitigate threats with AD DS
Microsoft Defender for Cloud full management and configurations
*Settings config in Microsoft Defender for Cloud
*Roles in Microsoft Defender for Cloud
*Cloud workload protection
*Automation of onboarding Azure resource
*Azure Arc connections
*Multi-cloud connections
*Email notifications in Microsoft Defender for Cloud
*Using alert suppression rules
*Workflow automation configuration in Defender for Cloud
*Using sample alerts and incidents
*Using Microsoft Defender for Cloud recommendations
*Security alerts and incidents in Microsoft Defender for Cloud
*Using threat intelligence reports with Microsoft Defender for Cloud
Dealing with insider risks in Microsoft 365
*Concepts of insider risk policies
*Insider risk policy generation
*Insider risk policy alert investigation
Audit and search capabilities in Microsoft Defender and Microsoft Purview
*Licensing of unified audit logging
*Permissions for unified auditing
*Threat hunting with unified audit logging
*Threat hunting with Content Searches
Conclusion
*Cleaning up your lab environment
*Getting a Udemy certificate
*BONUS Where do I go from here?
Комментарии
 2:10:03
2:10:03
 0:24:29
0:24:29
 1:44:12
1:44:12
 0:48:31
0:48:31
 0:28:00
0:28:00
 0:44:56
0:44:56
 4:04:11
4:04:11
 2:43:33
2:43:33
 1:10:06
1:10:06
 0:09:47
0:09:47
 0:06:02
0:06:02
 2:31:21
2:31:21
 0:21:03
0:21:03
 0:18:17
0:18:17
 0:05:24
0:05:24
 0:25:18
0:25:18
 2:36:41
2:36:41
 0:36:44
0:36:44
 0:08:20
0:08:20
 0:14:14
0:14:14
 0:47:07
0:47:07
 0:02:46
0:02:46
 0:01:01
0:01:01
 0:30:22
0:30:22