filmov
tv
Explaining Keystores | Part 2 - JCEKS

Показать описание
JCEKS (Java Cryptography Extension KeyStore) is an alternative to the JKS Keystore.
When strong cryptography was introduced into Java, the legacy JKS keystore with its "SHA-1 and XOR" encryption method was replaced by JCEKS, which uses Triple-DES (3DES) encryption to protect serialized keys when they are written to disk. There is a lot of JCEKS still around. So how exactly does the encryption work?
References:
/////
/////
Cryptosense CEO Dr. Graham Steel was formerly an academic researcher before founding Cryptosense in 2013. His cryptography expertise is the basis for the company's 'Analyzer' technology which allows customers to protect themselves against losing sensitive data.
When strong cryptography was introduced into Java, the legacy JKS keystore with its "SHA-1 and XOR" encryption method was replaced by JCEKS, which uses Triple-DES (3DES) encryption to protect serialized keys when they are written to disk. There is a lot of JCEKS still around. So how exactly does the encryption work?
References:
/////
/////
Cryptosense CEO Dr. Graham Steel was formerly an academic researcher before founding Cryptosense in 2013. His cryptography expertise is the basis for the company's 'Analyzer' technology which allows customers to protect themselves against losing sensitive data.
Explaining Keystores | Part 2 - JCEKS
Explaining Keystores | Part 3 - PKCS#12
Explaining Keystores | Part 1 - JKS
Explaining Keystores | Part 6 - Bouncy Castle FIPS Keystore (BCFKS)
Explaining Keystores | Part 4 - Bouncy Castle Keystore (BKS)
Cacert | Trust Store | Key Store in 3 minutes
Explaining Keystores | Part 5 - Bouncy Castle UBER
Java Keytool Tutorial: Part 2 - What is a KeyStore?
Should You Buy Games on G2A?
Keystore VS Truststore - JAVA Programming - Kiran Ahsan - Unique Tech
Episode 10: Understanding FIPS 140-2
OAuth 2 Explained In Simple Terms
Generating KeyStores and TrustStore using Keytool and OpenSSL - Part 2
SSL, TLS, HTTPS Explained
Key Players of SSL & TLS: Client, Server, Certificate Authority (CA) - Practical TLS
Asymmetric Encryption - Simply explained
GIANT ANACONDA or Loch Ness Monster? #shorts
OAuth 2.0 - PKCE
Java Keytool Tutorial : Part 1 - Introduction to Keytool
MTLS - Mutual TLS (Everything you need to know)
Securing Java Applications Part 2: Creating A Java KeyStore
Java Keystore - Introduction to Java Keystore | Encryption Consulting
Integrating Java Keystore with Luna HSM | Java Keystore - Part 2
SSL Chain of Trust | How SSL Chain Works | Root Cert, Intermediate Certificate, Server Certificate
Комментарии
 0:05:48
0:05:48
 0:04:37
0:04:37
 0:08:23
0:08:23
 0:03:48
0:03:48
 0:03:38
0:03:38
 0:03:32
0:03:32
 0:03:44
0:03:44
 0:16:34
0:16:34
 0:05:24
0:05:24
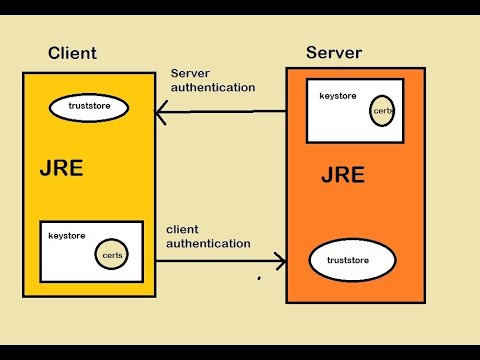 0:03:37
0:03:37
 0:05:02
0:05:02
 0:04:32
0:04:32
 0:17:07
0:17:07
 0:05:54
0:05:54
 0:05:40
0:05:40
 0:04:40
0:04:40
 0:00:29
0:00:29
 0:08:49
0:08:49
 0:15:17
0:15:17
 0:21:51
0:21:51
 0:09:44
0:09:44
 0:05:13
0:05:13
 0:15:04
0:15:04
 0:12:52
0:12:52