filmov
tv
MTLS - Mutual TLS (Everything you need to know)

Показать описание
MTLS Part-I:
MTLS Part - II (API Gateway)
Github:
MTLS Part - II (API Gateway)
Github:
MTLS - Mutual TLS (Everything you need to know)
What is Mutual TLS (mTLS)?
What Is Mutual TLS (mTLS), Why Do We Need It, And How Do We Get It?
TLS Vs mTLS - How certificates are exchanged ?
Mutual TLS (mTLS) - The Future of Cybersecurity explained with real life examples
mTLS Explained in 15 minutes | Mutual TLS Concepts | LetsDoCoding
Mutual TLS (mTLS) Overview
Tutorial: Two-Way SSL Mutual Authentication
Lightning Talk: Effortless, Sidecar-Less Mutual TLS and Rich Authorization Policies up and... L. Sun
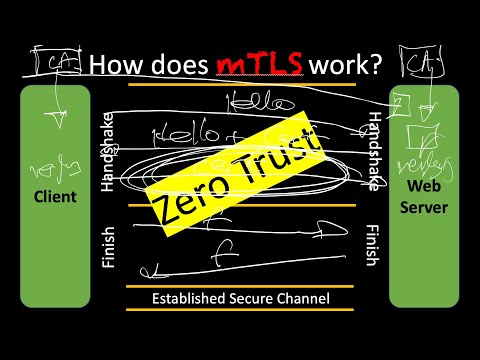
TLS Part 4: How does mTLS work?
SSL, TLS, HTTPS Explained
What is mTLS (mutual TLS)?
One Way TLS and Mutual TLS(mTLS)
How does mTLS work within a service mesh?
OAuth 2.0 mutual client authentication (mTLS)
Amazon API Gateway Mutual TLS with DEMO | Custom Domain vs. Custom Domain Mutual TLS (mTLS)
Mutual TLS | The Backend Engineering Show
Mutual TLS (mTLS) Detailed Handshake
Exploring Mutual TLS (mTLS) : Generate Client Certificates
What is MTLS?
Intro to Mutual TLS
AWS - Создаём Serverless API + MutualTLS и Что такое mTLS
mTLS with NGINX
Network encryption basics | What is Mutual TLS (mTLS) ? -TTWA ep# 2 with Frank Yue
Комментарии
 0:21:51
0:21:51
 0:02:18
0:02:18
 0:19:05
0:19:05
 0:00:47
0:00:47
 0:09:01
0:09:01
 0:14:26
0:14:26
 0:03:15
0:03:15
 0:02:44
0:02:44
 0:05:40
0:05:40
 0:04:03
0:04:03
 0:05:54
0:05:54
 0:00:58
0:00:58
 0:14:36
0:14:36
 0:04:31
0:04:31
 0:09:52
0:09:52
 0:16:33
0:16:33
 0:50:16
0:50:16
 0:12:05
0:12:05
 0:01:01
0:01:01
 0:01:03
0:01:03
 0:05:12
0:05:12
 0:20:22
0:20:22
 0:31:01
0:31:01
 0:41:58
0:41:58