filmov
tv
Java Keystore - Introduction to Java Keystore | Encryption Consulting

Показать описание
Java Keystore - Introduction to Java Keystore | Encryption Consulting
#javakeystore #keystore #cryptographickeys
👉SUBSCRIBE
Be sure to Subscribe and click that Bell Icon for notifications!
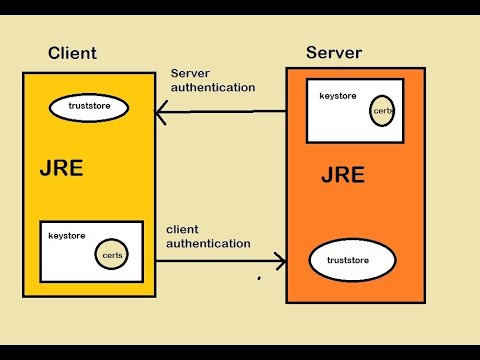
Java Keystore offers one of many ways to generate, store, manage and use cryptographic keys. Keystore can also be integrated with HSM to provide extra security that will ensure private are module protected. We would have a walkthrough on upcoming Part 2 and 3 on integrating Keystore with nCipher and Thales Luna HSM. Stay Tuned!
References
------------------------------------------------------------------------------------------------------------------------------------------------------------
For latest updates, follow us on –
Video tags-
java keystore
introduction to java keystore
java keystore tutorial
java keystore explained
cryptography
application security
cryptography inventory
prevent data loss
data security
cloud data security
data security compliance
cryptography compliance
devops security
protect sensitive data
cryptography audit
avoid data breaches
automate cryptography audit
automate cloud security audit
keystore attack
jks keystore
encryption consulting
#javakeystore #keystore #cryptographickeys
👉SUBSCRIBE
Be sure to Subscribe and click that Bell Icon for notifications!
Java Keystore offers one of many ways to generate, store, manage and use cryptographic keys. Keystore can also be integrated with HSM to provide extra security that will ensure private are module protected. We would have a walkthrough on upcoming Part 2 and 3 on integrating Keystore with nCipher and Thales Luna HSM. Stay Tuned!
References
------------------------------------------------------------------------------------------------------------------------------------------------------------
For latest updates, follow us on –
Video tags-
java keystore
introduction to java keystore
java keystore tutorial
java keystore explained
cryptography
application security
cryptography inventory
prevent data loss
data security
cloud data security
data security compliance
cryptography compliance
devops security
protect sensitive data
cryptography audit
avoid data breaches
automate cryptography audit
automate cloud security audit
keystore attack
jks keystore
encryption consulting
 0:08:23
0:08:23
 0:05:13
0:05:13
 0:00:38
0:00:38
 0:05:08
0:05:08
 0:03:32
0:03:32
 0:05:48
0:05:48
 0:15:17
0:15:17
 0:04:37
0:04:37
 0:03:37
0:03:37
 0:05:31
0:05:31
 0:05:54
0:05:54
 0:09:44
0:09:44
 0:16:34
0:16:34
 0:17:07
0:17:07
 0:01:51
0:01:51
 0:10:17
0:10:17
 0:08:24
0:08:24
 0:27:48
0:27:48
 0:00:53
0:00:53
 0:03:26
0:03:26
 0:17:21
0:17:21
 0:03:23
0:03:23
 0:06:25
0:06:25
 0:03:42
0:03:42