filmov
tv
3 - Cryptography Basics - Digital Certificate

Показать описание
In this video you'll learn about Digital Certificate and it's applications
3 - Cryptography Basics - Digital Certificate
7 Cryptography Concepts EVERY Developer Should Know
What is Cryptography | Cryptography Explained | Cryptography Basics | Intellipaat
2 - Cryptography Basics - Digital Signature
Cryptography
3. Blockchain Basics & Cryptography
Asymmetric Encryption - Simply explained
The Science of Codes: An Intro to Cryptography
3 MUST Knows for Crypto
CISSP Bootcamp - Session 9 - Domain 3 - Cryptography Basics
The RSA Encryption Algorithm (1 of 2: Computing an Example)
1 - Cryptography Basics
Cryptography in 3 minutes | Cryptography explained
COM-402 Spring 2018 Lecture 3: Cryptography Basics (Part 1)
Cryptography 101 - The Basics
Coins VS Tokens: What's the Difference? | 3-min crypto
7 - Cryptography Basics - Diffie-Hellman Key Exchange
Principles of Cryptography: Basics
Basic Cryptography
Security Part2 - Basics of cryptography - 3 Integrity
Cryptography - Basics #cryptography #studymaterial #informatio #theory
Cryptography Basics
Blockchain In 7 Minutes | What Is Blockchain | Blockchain Explained|How Blockchain Works|Simplilearn
Cryptography Full Course | Cryptography And Network Security | Cryptography | Simplilearn
Комментарии
 0:11:28
0:11:28
 0:11:55
0:11:55
 0:02:18
0:02:18
 0:05:17
0:05:17
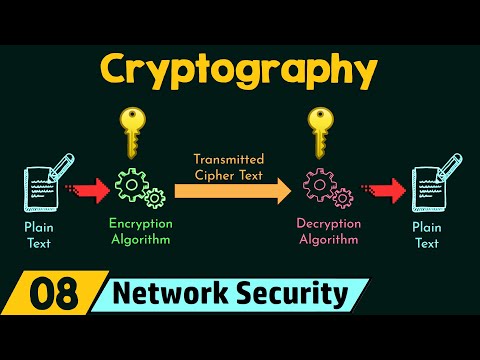 0:13:34
0:13:34
 1:17:38
1:17:38
 0:04:40
0:04:40
 0:08:21
0:08:21
 0:08:03
0:08:03
 0:52:43
0:52:43
 0:08:40
0:08:40
 0:15:23
0:15:23
 0:03:08
0:03:08
 0:59:13
0:59:13
 0:08:57
0:08:57
 0:03:02
0:03:02
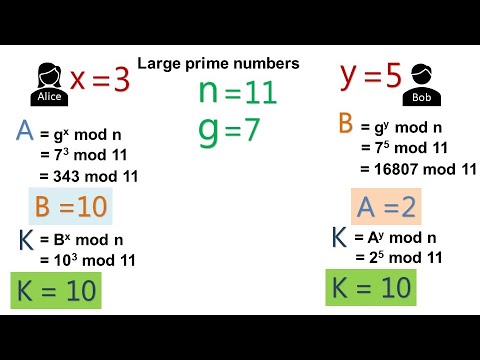 0:08:48
0:08:48
 0:06:07
0:06:07
 0:07:58
0:07:58
 0:24:51
0:24:51
 0:04:29
0:04:29
 0:03:41
0:03:41
 0:07:03
0:07:03
 2:15:01
2:15:01