filmov
tv
7 - Cryptography Basics - Diffie-Hellman Key Exchange

Показать описание
In this video you'll learn about Diffie-Hellman key exchange method.
7 Cryptography Concepts EVERY Developer Should Know
7 - Cryptography Basics - Diffie-Hellman Key Exchange
Cryptography
The Science of Codes: An Intro to Cryptography
1 - Cryptography Basics
Asymmetric Encryption - Simply explained
Cryptography Lesson #1 - Block Ciphers
Encryption Basics | Cryptography
DPI: Daily Passive Income: Vfat.io
The RSA Encryption Algorithm (1 of 2: Computing an Example)
What is Cryptography | Cryptography Explained | Cryptography Basics | Intellipaat
Lecture 7 (Cryptography Basics)
2 - Cryptography Basics - Digital Signature
How Encryption Works - and How It Can Be Bypassed
Cryptography basics,types of algorithms and security services
Cryptography Basics
Basic Cryptography
Blockchain In 7 Minutes | What Is Blockchain | Blockchain Explained|How Blockchain Works|Simplilearn
ANDREW TATE SAYS THIS ABOUT CRYPTO FUTURE #shorts
What Is Cryptography | Encryption Basics
8 - Cryptography Basics - SSL TLS Protocol Explained
How to Encrypt with RSA (but easy)
Cryptocurrency In 5 Minutes | Cryptocurrency Explained | What Is Cryptocurrency? | Simplilearn
Introduction to Data Encryption Standard (DES)
Комментарии
 0:11:55
0:11:55
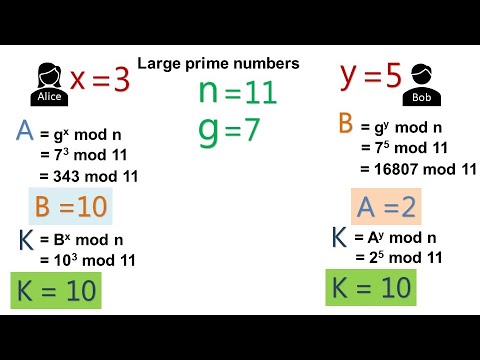 0:08:48
0:08:48
 0:13:34
0:13:34
 0:08:21
0:08:21
 0:15:23
0:15:23
 0:04:40
0:04:40
 0:04:17
0:04:17
 0:12:59
0:12:59
 0:15:12
0:15:12
 0:08:40
0:08:40
 0:02:18
0:02:18
 0:13:12
0:13:12
 0:05:17
0:05:17
 0:02:49
0:02:49
 0:10:53
0:10:53
 0:03:41
0:03:41
 0:07:58
0:07:58
 0:07:03
0:07:03
 0:00:34
0:00:34
 0:08:43
0:08:43
 0:13:38
0:13:38
 0:06:01
0:06:01
 0:05:33
0:05:33
 0:08:18
0:08:18