filmov
tv
How to Bypass MFA - A Real Time Example (It's easy)

Показать описание
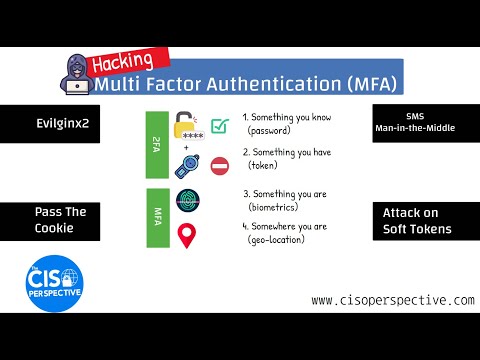
Not all multi-factor authentication (MFA) can offer the same level protection against different types of attacks.
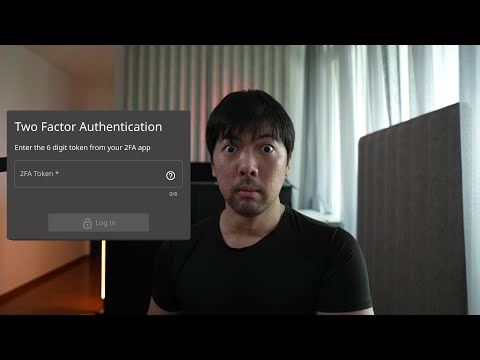
In this video we’re going to demonstrate just how easy it is for phishing attacks to steal a user’s credentials and authenticated session cookie. Even with MFA in place.
To set the scene we have Alice who works for a business that operates in the cloud.
1. She has a Microsoft 365 account, and she has some responsible roles looking after the company's Azure estate.
2. She uses a very secure password, over 128 characters long
3. and she's configured push based multifactor authentication using the Microsoft Authenticator app on her company phone to secure her access
However, having MFA in place with a secure password doesn’t mean her account is safe from adversary or man in the middle phishing attacks.
We’re going to show you how.
HOW BUSINESSES CAN PROTECT THEMSELVES
As you can see, having MFA enabled and set up does not necessarily mean that you or your users are secure. Different multifactor authentication technologies provide different levels of security. Targeted spear phishing can often look legit, with business email compromise being a common attack vector used by hackers. Phishing URLs can also be easily configured to temporarily lay dormant and redirect to legitimate URLs, whilst a spear phishing campaign is started.
Phishing resistant methods utilising web authentication, such as FIDO 2, for example, is one such MFA method, which is resistant to this type of attack.
FOLLOW THE TEAM
TIME STAMPS
Intro 00:00-01:07
Setting the scene 01:08 - 02:20
Setting up the attack - 02:21 - 04:10
Bypassing MFA - 04:12 - 06:18
Preventing the attack 06:19 - 08:26
Key takeaways - 08:27 - 10:05
In this video we’re going to demonstrate just how easy it is for phishing attacks to steal a user’s credentials and authenticated session cookie. Even with MFA in place.
To set the scene we have Alice who works for a business that operates in the cloud.
1. She has a Microsoft 365 account, and she has some responsible roles looking after the company's Azure estate.
2. She uses a very secure password, over 128 characters long
3. and she's configured push based multifactor authentication using the Microsoft Authenticator app on her company phone to secure her access
However, having MFA in place with a secure password doesn’t mean her account is safe from adversary or man in the middle phishing attacks.
We’re going to show you how.
HOW BUSINESSES CAN PROTECT THEMSELVES
As you can see, having MFA enabled and set up does not necessarily mean that you or your users are secure. Different multifactor authentication technologies provide different levels of security. Targeted spear phishing can often look legit, with business email compromise being a common attack vector used by hackers. Phishing URLs can also be easily configured to temporarily lay dormant and redirect to legitimate URLs, whilst a spear phishing campaign is started.
Phishing resistant methods utilising web authentication, such as FIDO 2, for example, is one such MFA method, which is resistant to this type of attack.
FOLLOW THE TEAM
TIME STAMPS
Intro 00:00-01:07
Setting the scene 01:08 - 02:20
Setting up the attack - 02:21 - 04:10
Bypassing MFA - 04:12 - 06:18
Preventing the attack 06:19 - 08:26
Key takeaways - 08:27 - 10:05
Комментарии
 0:09:20
0:09:20
 0:09:22
0:09:22
 0:10:06
0:10:06
 0:12:47
0:12:47
 0:08:57
0:08:57
 0:10:16
0:10:16
 0:03:58
0:03:58
 0:04:18
0:04:18
 1:35:25
1:35:25
 0:08:13
0:08:13
 0:01:04
0:01:04
 0:06:00
0:06:00
 0:16:59
0:16:59
 0:09:23
0:09:23
 0:00:56
0:00:56
 0:02:29
0:02:29
 0:08:14
0:08:14
 0:12:46
0:12:46
 0:02:09
0:02:09
 0:08:50
0:08:50
 0:03:44
0:03:44
 0:05:24
0:05:24
 0:10:41
0:10:41
 0:00:24
0:00:24