filmov
tv
Symmetric Key Cryptography: Cryptographic Techniques

Показать описание
This is the fifth in a series about cryptography; an extremely important aspect of computer science and cyber security. It reviews how the XOR logical operation can be used to encrypt at the bit level in symmetric key cryptography, then shows how this can be combined with permutation steps to create an even stronger cipher. It mentions a number of principles used in modern day block ciphers such as DES and AES, including the Feistel cipher, block ciphers, block chaining, the use of multiple sub keys and multiple encryption rounds.
Symmetric Key Cryptography: Cryptographic Techniques
Asymmetric Encryption - Simply explained
7 Cryptography Concepts EVERY Developer Should Know
Lec-81: Symmetric Key Cryptography in Network Security with examples
Symmetric Key Cryptography | Stream Cipher & Block Cipher Explained | Network Security | Simplil...
Cryptography
Encryption - Symmetric Encryption vs Asymmetric Encryption - Cryptography - Practical TLS
Cryptography: Crash Course Computer Science #33
Encryption 101 Symmetric vs Asymmetric 2024 10 17
Symmetric Key Cryptography: The XOR Cipher
Symmetric vs. Asymmetric Encryption - CompTIA Security+ SY0-401: 6.1
Symmetric Key Cryptography And Asymmetric Key Cryptography | Cryptography Tutorial | Simplilearn
Symmetric Key Cryptography - Cipher
Introduction to Basic Cryptography: Symmetric Key Cryptography
Symmetric Key and Public Key Encryption
Symmetric and Asymmetric Cryptography - SY0-601 CompTIA Security+ : 2.8
Cryptography – Key Terms
Symmetric Cryptosystems - Applied Cryptography
Public Key Cryptography - Computerphile
Symmetric Algorithms - CompTIA Security+ SY0-501 - 6.2
Private Key Encryption (Symmetric Key Encryption)
Symmetric Encryption Algorithms
Cryptography Full Course | Cryptography And Network Security | Cryptography | Simplilearn
Symmetric Key Cryptography ll Information and Cyber Security Course Explained in Hindi
Комментарии
 0:11:02
0:11:02
 0:04:40
0:04:40
 0:11:55
0:11:55
 0:06:14
0:06:14
 0:10:41
0:10:41
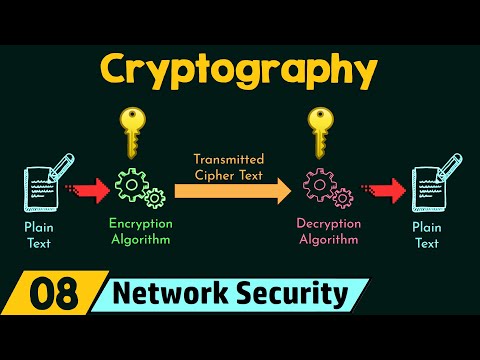 0:13:34
0:13:34
 0:13:58
0:13:58
 0:12:33
0:12:33
 0:04:31
0:04:31
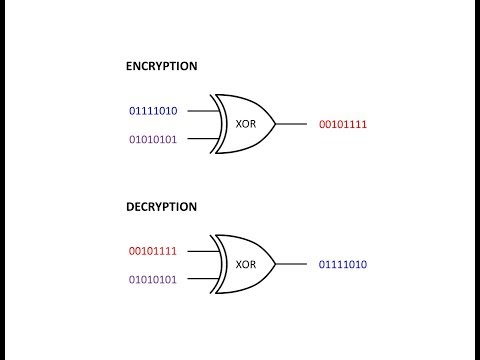 0:07:46
0:07:46
 0:04:18
0:04:18
 0:21:21
0:21:21
 0:08:19
0:08:19
 0:13:17
0:13:17
 0:06:45
0:06:45
 0:09:21
0:09:21
 0:09:39
0:09:39
 0:02:27
0:02:27
 0:06:20
0:06:20
 0:04:45
0:04:45
 0:04:52
0:04:52
 0:04:56
0:04:56
 2:15:01
2:15:01
 0:07:42
0:07:42