filmov
tv
Symmetric Key and Public Key Encryption
Показать описание
Download the PDF handout
Encryption Types
Encryption is the process of scrambling data so it cannot be read without a decryption key. Encryption prevents data being read by a 3rd party if it is intercepted by a 3rd party. The two encryption methods that are used today are symmetric and public key encryption.
Symmetric Key
Symmetric key encryption uses the same key to encrypt data as decrypt data. This is generally quite fast when compared with public key encryption. In order to protect the data, the key needs to be secured. If a 3rd party was able to gain access to the key, they could decrypt any data that was encrypt with that data. For this reason, a secure channel is required to transfer the key if you need to transfer data between two points. For example, if you encrypted data on a CD and mail it to another party, the key must also be transferred to the second party so that they can decrypt the data. This is often done using e-mail or the telephone. In a lot of cases, sending the data using one method and the key using another method is enough to protect the data as an attacker would need to get both in order to decrypt the data.
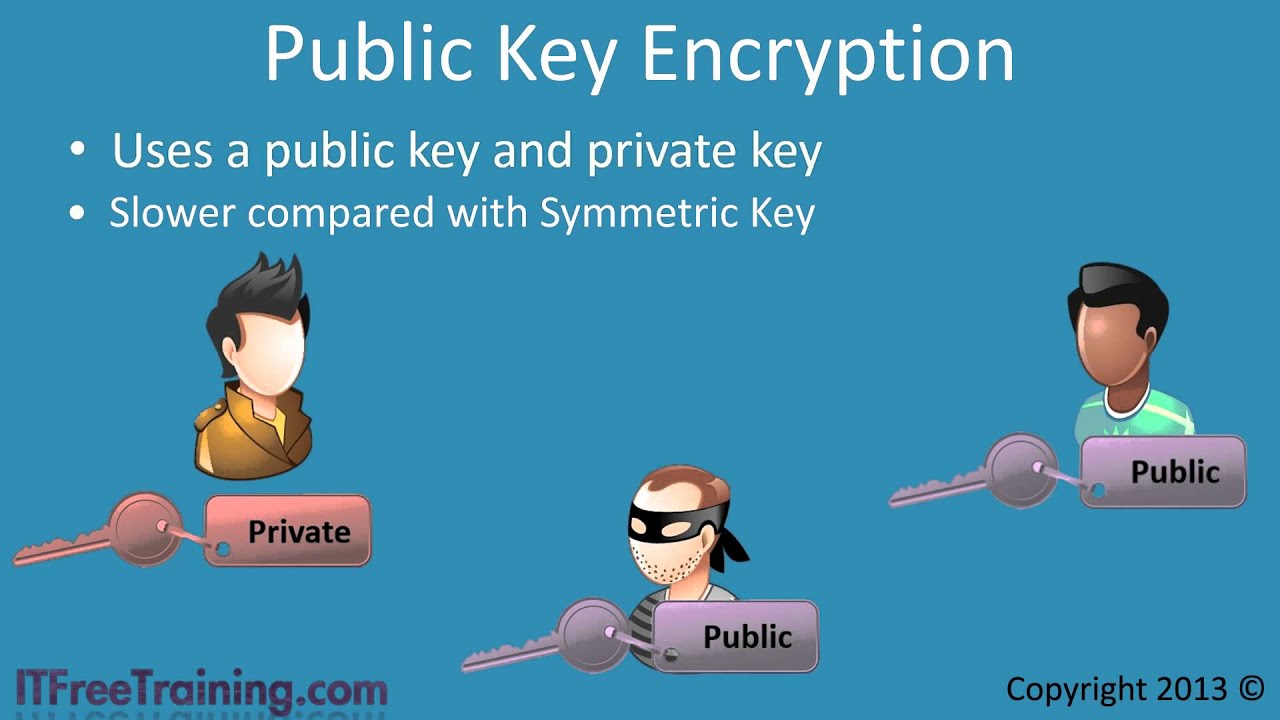
Public Key Encryption
This method of encryption uses two keys. One key is used to encrypt data and the other key is used to decrypt data. The advantage of this is that the public key can be downloaded by anyone. Anyone with the public key can encrypt data that can only be decrypted using a private key. This means the public key does not need to be secured. The private key does need to be keep in a safe place. The advantage of using such a system is the private key is not required by the other party to perform encryption. Since the private key does not need to be transferred to the second party there is no risk of the private key being intercepted by a 3rd party. Public Key encryption is slower when compared with symmetric key so it is not always suitable for every application. The math used is complex but to put it simply it uses the modulus or remainder operator. For example, if you wanted to solve X mod 5 = 2, the possible solutions would be 2, 7, 12 and so on. The private key provides additional information which allows the problem to be solved easily. The math is more complex and uses much larger numbers than this but basically public and private key encryption rely on the modulus operator to work.
Combing The Two
There are two reasons you want to combine the two. The first is that often communication will be broken into two steps. Key exchange and data exchange. For key exchange, to protect the key used in data exchange it is often encrypted using public key encryption. Although slower than symmetric key encryption, this method ensures the key cannot accessed by a 3rd party while being transferred. Since the key has been transferred using a secure channel, a symmetric key can be used for data exchange. In some cases, data exchange may be done using public key encryption. If this is the case, often the data exchange will be done using a small key size to reduce the processing time.
The second reason that both may be used is when a symmetric key is used and the key needs to be provided to multiple users. For example, if you are using encryption file system (EFS) this allows multiple users to access the same file, which includes recovery users. In order to make this possible, multiple copies of the same key are stored in the file and protected from being read by encrypting it with the public key of each user that requires access.
References
Комментарии
 0:04:40
0:04:40
 0:06:45
0:06:45
 0:06:20
0:06:20
 0:09:22
0:09:22
 0:12:33
0:12:33
 0:06:14
0:06:14
 0:02:12
0:02:12
 0:13:58
0:13:58
 0:00:57
0:00:57
 0:03:19
0:03:19
 0:04:18
0:04:18
 0:11:18
0:11:18
 0:06:40
0:06:40
 0:08:40
0:08:40
 0:04:52
0:04:52
 0:10:41
0:10:41
 0:09:18
0:09:18
 0:11:55
0:11:55
 0:09:21
0:09:21
 0:05:06
0:05:06
 0:03:35
0:03:35
 0:06:55
0:06:55
 0:08:15
0:08:15
 0:03:04
0:03:04