filmov
tv
Symmetric Key Cryptography: The XOR Cipher

Показать описание
This is the fourth in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers the XOR logical operation, that is the exclusive OR operation, explaining how it can be used to encrypt and decrypt a sequence of binary digits. XOR is an important process that is employed by many modern day ciphers. Using a spreadsheet, this video demonstrates how the XOR logical operation can be applied to a single character ASCII code to encrypt and decrypt it using the same symmetric key, and the same method.
Symmetric Key Cryptography: The XOR Cipher
XOR in Symmetric encryption
Cryptography 101 - - XOR Cipher
Asymmetric Encryption - Simply explained
XOR Encryption
XOR Cipher in Python - Simple Cryptography
019 Understanding XOR bit Cipher
Bitwise Operators 3: The XOR Operation
Why XOR is used everywhere in Cryptography?
Xor Function - Applied Cryptography
XOR Cipher | Simple Modern Cipher
Symmetric Key Cryptography: Cryptographic Techniques
Symmetric Key Cryptography | Stream Cipher & Block Cipher Explained | Network Security | Simplil...
Lec-81: Symmetric Key Cryptography in Network Security with examples
The Power of XOR
XOR Operator
XOR - Encryption Tutorial - 1
Use Python to encrypt and decrypt data using XOR encryption
Cryptography with Python! XOR
The Power of XOR in Cryptography
Mathematics: How to break XOR cipher with repeating key? (4 Solutions!!)
XOR encryption program in C (5 Solutions!!)
Took the Byte [easy]: HackTheBox Forensics Challenge (XOR decryption with CyberChef)
XOR Encryption and Decryption Cryptography
Комментарии
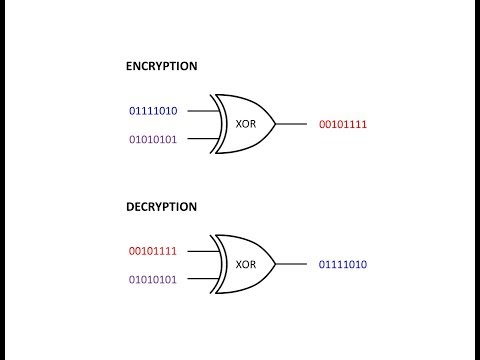 0:07:46
0:07:46
 0:02:30
0:02:30
 0:05:34
0:05:34
 0:04:40
0:04:40
 0:04:09
0:04:09
 0:10:09
0:10:09
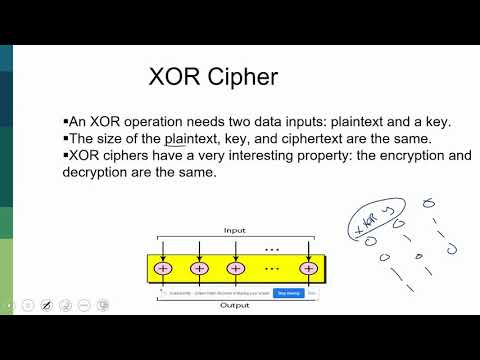 0:06:54
0:06:54
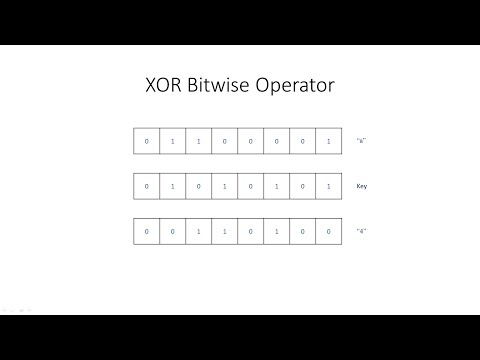 0:05:29
0:05:29
 0:07:14
0:07:14
 0:01:18
0:01:18
 0:08:46
0:08:46
 0:11:02
0:11:02
 0:10:41
0:10:41
 0:06:14
0:06:14
 0:04:41
0:04:41
 0:07:24
0:07:24
 0:05:01
0:05:01
 0:01:22
0:01:22
 0:27:26
0:27:26
 0:05:24
0:05:24
 0:02:59
0:02:59
 0:04:52
0:04:52
 0:03:04
0:03:04
 0:17:24
0:17:24