filmov
tv
Buffer Overflows and Integer Overflows - CompTIA Security+ SY0-401: 3.5

Показать описание
- - - - -
A poorly developed application can allow the bad guys to manipulate memory using buffer overflows and integer overflows. In this video, you’ll learn how an overflow works and what you can do to prevent these security issues.
- - - - -
FOLLOW PROFESSOR MESSER:
A poorly developed application can allow the bad guys to manipulate memory using buffer overflows and integer overflows. In this video, you’ll learn how an overflow works and what you can do to prevent these security issues.
- - - - -
FOLLOW PROFESSOR MESSER:
Buffer Overflows and Integer Overflows - CompTIA Security+ SY0-401: 3.5
What is a Buffer Overflow Attack?
Buffer Overflows Part 6 - Integer Overflows
Buffer Overflows - CompTIA Security+ SY0-701 - 2.3
Integer Overflows
What is an Integer Overflow Vulnerability? | Hacking 101
Buffer Overflow P20 | Integer Overflow | CTF Walkthrough
What Is BUFFER OVERFLOW? | Overflow Of Input | Programming Errors Explained
Buffer overflow - Integer Overflow
Buffer Overflows - SY0-601 CompTIA Security+ : 1.3
From Missingno to Heartbleed: Buffer Exploits and Buffer Overflows
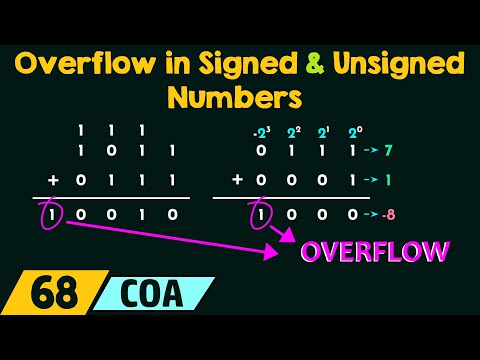
Overflow in Signed and Unsigned Numbers
How They Hack: Simple Buffer Overflow
Integer/ Buffer Overflow Vulnerability - Real World Example
PHP INTEGER UNDERFLOW/OVERFLOW VULNERABILITY
Buffer Overflow 101: Ep 1 - x86 Memory Fundamentals
BUFFER OVERFLOW Tutorial (SO gefährlich ist es) #1.0
What is Integer Overflow Attack? | Impossible Number 247 CTF
When Integer Overflows attack: How an Integer Overflow can can lead to Remote Code Execution
2 Running a Buffer Overflow Attack - Computerphile || Why do buffers overflow
Buffer Overflows - CompTIA Security+ SY0-501 - 1.2
Buffer Overflow Hacking Tutorial (Bypass Passwords)
Integer Overflow
Buffer Overflows - Software Debugging
Комментарии
 0:05:06
0:05:06
 0:02:24
0:02:24
 0:09:02
0:09:02
 0:03:37
0:03:37
 0:11:23
0:11:23
 0:04:53
0:04:53
 0:31:15
0:31:15
 0:04:45
0:04:45
 0:01:23
0:01:23
 0:02:38
0:02:38
 0:06:15
0:06:15
 0:10:11
0:10:11
 0:07:37
0:07:37
 0:04:29
0:04:29
 0:00:33
0:00:33
 0:08:43
0:08:43
 0:05:16
0:05:16
 0:03:11
0:03:11
 0:09:13
0:09:13
 0:07:57
0:07:57
 0:03:06
0:03:06
 0:55:39
0:55:39
 0:08:22
0:08:22
 0:01:36
0:01:36